DevSecOps
Build secure apps on a trusted platform. Embed security in your developer workflow and foster collaboration between developers, security practitioners, and IT operators.
Securely deliver innovative apps at DevOps speed
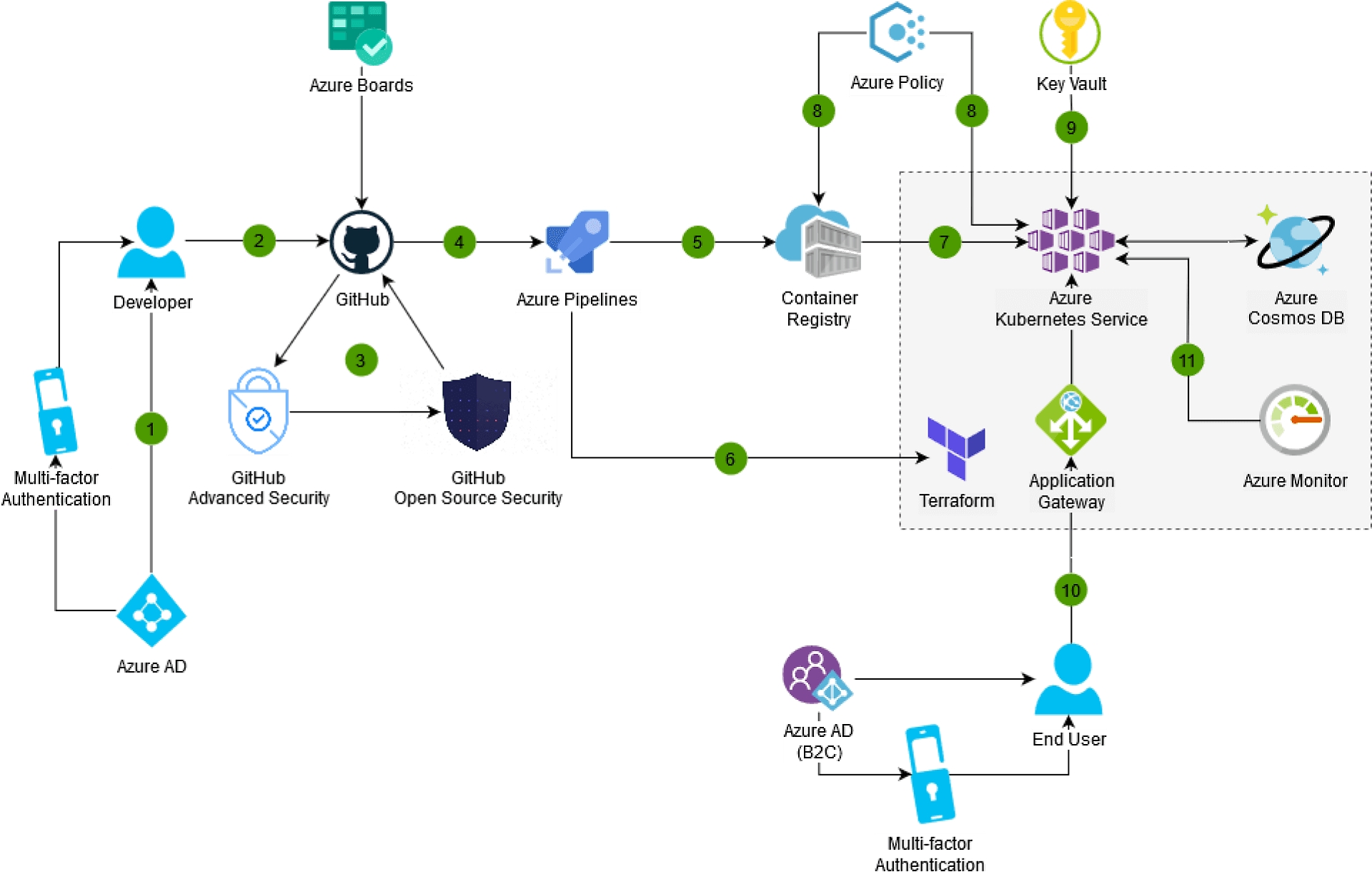
As new types of cybersecurity attacks rise, harden your development environment and software supply chain by integrating security early in the development cycle. DevSecOps combines GitHub and Azure products and services to foster collaboration between DevOps and SecOps teams. Use the complete solution to deliver more secure, innovative apps at DevOps speed.


Help protect your environment by involving everyone in your organization in building and operating secure applications. "Shift-left" security is about incorporating security thinking in the earliest stages of development, from planning to development, packaging, and deployment. Detect potential security vulnerabilities automatically at code review time by integrating security into the developer workflow with Microsoft Visual Studio and GitHub.


Achieve better control of your software supply chain when using third-party code and open-source software for your applications. Develop with confidence using Azure and GitHub products and services that inspect your code in production, and trace third-party components in use for increased security.


Use an extensive set of Azure services that make operating your application more convenient and safe. Run your code on managed application platforms, including Kubernetes, and use trusted services to manage your keys, tokens, and secrets more securely. Increase confidence in the security of your environment with policies. Help ensure smooth, safe operations with real-time monitoring solutions for your applications and infrastructure.


Help protect your application, code, and infrastructure with tight access control. Azure offers leading identity services for your organization’s internal users and external consumers who access your applications. Use the DevSecOps tools and identity platform to secure access to your code on GitHub, manage granular permissions for Azure resources, and offer authentication and authorization services for your applications.
Leverage a complete set of products and services—or choose only the ones you need
Get advanced features that help you secure your app's code, dependencies, and secrets, available for GitHub and Azure DevOps
- Identify vulnerabilities in your code with CodeQL, the industry’s leading semantic code analysis engine.
- Identify and remediate security issues in your dependencies using Dependabot for security alerts and automated security updates.
- Get automatically notified and block pushes where credentials are mistakenly committed into source control with secret scanning.
Confidently build production-ready container images with full end-to-end traceability. With Azure Pipelines for continuous integration and continuous delivery (CI/CD), your code is compiled and packaged into a Docker container on each commit and automatically deployed to a test environment. Trace the commits, work items, and artifacts of every image to understand the code running in your environment.
Use GitHub Actions to automate and run software workflows on any GitHub event like push, issue creation, or a new release. Combine and configure actions for the services you use and save time with matrix workflows that simultaneously test across multiple operating systems. Build, test, and deploy code with support for any language of your choice.
Build, store, secure, scan, replicate, and manage container images and artifacts with Azure Container Registry. Identify vulnerable container images in your CI/CD workflows with automatic scanning using Microsoft Defender for Cloud.
Start with secure configuration of your cloud infrastructure as code (IaC) with Azure Resource Manager (ARM) or other templates to quickly onboard developers with minimal burden. Apply and enforce templatized configurations that ensure consistent security across the organization, paired with Microsoft Defender for Cloud IaC template scanning to minimize cloud misconfigurations reaching production environments.
Deploy your AKS cluster directly from your CI/CD pipeline, using infrastructure-as-code solutions such as Terraform.
Use Azure Policy with AKS to help ensure that operations are compliant.
Securely store and manage keys, certificates, tokens, and other secrets with Azure Key Vault so your applications can load them at run time while avoiding the risk of including keys inside applications' code. Bolster security to FIPS 140-2 Level 2 and Level 3 compliance by importing and generating keys in hardware security modules (HSMs).
Combine with secret scanning from GitHub Advanced Security or GitHub Advanced Security for Azure DevOps to protect against vulnerabilities caused by pushing secrets to code repositories.
Whether you're building an external-facing or internal line-of-business app, use Microsoft Entra ID (formerly Azure AD) to manage identity and access control.
Eliminate the need for managing Azure service principal secrets and other cloud credentials in the GitHub secret store with Microsoft Entra ID (formerly Azure AD) workload identity federation capabilities. Manage all cloud resource access more securely in Azure. These capabilities also minimize the risk of service downtime due to expired credentials in GitHub.
Authenticate users with your organization's directory and rely on advanced security features such as multifactor authentication, Microsoft Entra ID (formerly Azure AD) Identity Protection, and anomalous activity reports.
Help protect access to your Azure resources and the Azure portal with granular role-based access control (RBAC).
Manage access to your business-to-consumer applications for external users with Microsoft Entra ID (formerly Azure AD) B2C.
Monitor your application and infrastructure in real time using Azure Monitor. Identify issues with your code and potentially suspicious activities and anomalies.
Azure Monitor integrates with release pipelines in Azure Pipelines to enable automatic approval of quality gates or release rollback based on monitoring data.
Microsoft Defender for Cloud continually assesses, secures, and defends Azure, on-premises, or multicloud workloads and security postures. Provide full visibility into the DevOps inventory and the security posture of pre-production application code and resource configurations.

Learn how to secure all your enterprise DevOps environments
Explore the ideal secure setup of Enterprise DevOps tools and practices. This e-book focuses specifically on hardening developer, DevOps platform, and application environments.
Related products
Visual Studio Code
A powerful, lightweight code editor for cloud development.
Azure DevOps
Services for teams to share code, track work, and ship software.
GitHub Enterprise
Innovate at scale by securely bringing open-source code and best practices to your enterprise projects.
Azure Key Vault
Safeguard and maintain control of keys and other secrets.
Microsoft Entra ID (formerly Azure Active Directory)
Synchronize on-premises directories and enable single sign-on.
Azure Monitor
Full observability into your applications, infrastructure, and network.
Microsoft Defender for Cloud
Protect your multi-cloud and hybrid environments.
GitHub Advanced Security for Azure DevOps
Code, secret, and dependency scanning that's native to the developer workflow.
DevSecOps in Azure
If your business is storing custom or client data, develop solutions to cover the management and interface of this data with security in mind. DevSecOps utilizes security best practices from the beginning of development, rather than auditing at the end, using a shift-left strategy.
Get started with DevSecOps
Learn how to enable DevSecOps with GitHub and Azure.
Learn more about cloud security
Find out how to safeguard your multicloud apps and resources.







