Databases are constantly evolving to handle new use cases, incorporate more intelligence, and store more data, giving developers and organizations a wide range of database types to meet their varying needs. Because aspects including architecture, capabilities, configuration options, and authentication methods are unique to each database type, so are the security threats—requiring custom security measures and protection capabilities to address the most common threats across databases.
Azure Cosmos DB is a fully managed NoSQL database for modern, fast, and flexible app development, offering single-digit millisecond response times, automatic and instant scalability, and multiple SDKs and APIs to support a variety of non-relational data models.
Today we’re excited to announce a new addition to our database protection offering Microsoft Defender for Azure Cosmos DB in preview.
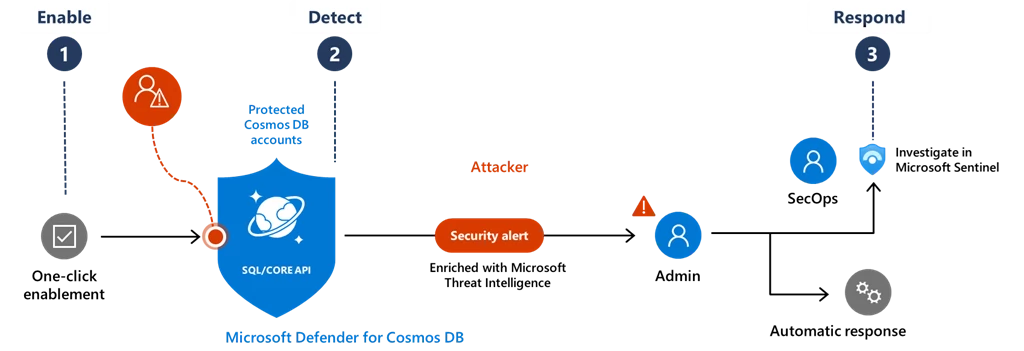
The new cloud workload protection capabilities are designed as an Azure-native layer of security, that detect attempts to exploit databases in your Azure Cosmos DB accounts based on the most common attack techniques and known bad actors—enabling security teams to detect and respond to these threats more effectively, using the Microsoft Defender for Cloud toolset.
These detections are delivered based on Microsoft Threat Intelligence, the Microsoft Defender SQL query analysis engine, and Microsoft Defender behavioral models.
Detect the most critical threats targeting Azure Cosmos DB
Defender for Azure Cosmos DB monitors your Azure Cosmos DB accounts and protects them from various attack vectors, such as attacks originating from the application layer, SQL injections, suspicious access patterns, compromised identities, malicious insiders, and direct attacks on the database. Below is an overview of the key threat techniques that affect Azure Cosmos DB and are supported alert types in Microsoft Defender for Cloud.
- SQL injections: It is not commonly known that one of the most popular attack techniques—SQL injection—can be executed against a database in Azure Cosmos DB. This technique allows the attacker to hide behind the application’s credentials and behaviors, so they can carry out an attack without the need to get their own credentials in order to exploit the database. Attackers can use SQL injection techniques to bypass the application’s access controls and extract sensitive data. Defender for Azure Cosmos DB detects these attempts early, as well as helps with recommendations and policies to harden your applications to help prevent these exploits in the first place.
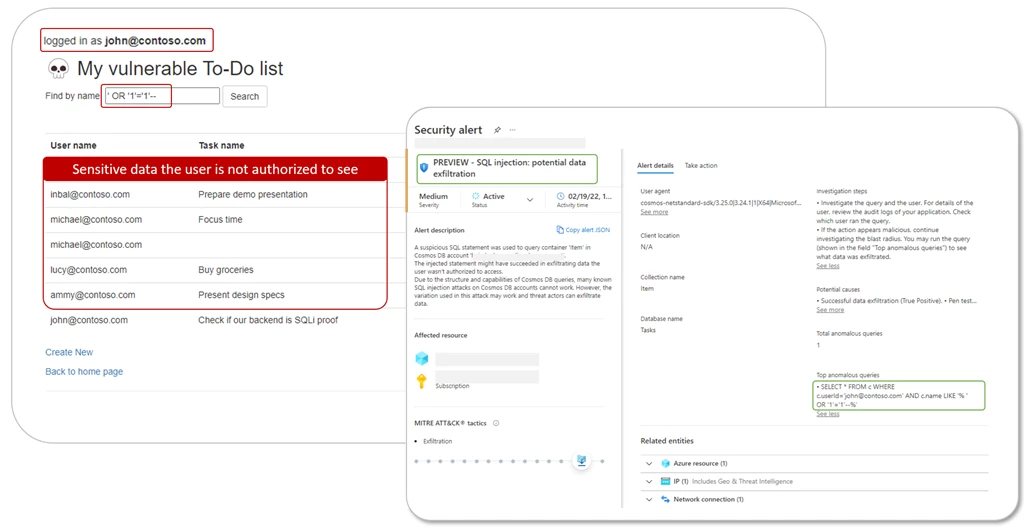
- Key extraction: This is an indicative pattern of a compromised identity looking for ways to access the crown jewels of your organization—your data. The most common way for compromised identities and malicious insiders to exploit an Azure Cosmos DB database is to extract the access keys to the account. These keys allow full access to all data in the Azure Cosmos DB account. In these cases, where an attacker manages to get hold of a compromised identity, it’s critical to detect a breach early and ensure they’re not able to scan your Azure Cosmos DB account and extract critical data. Defender for Azure Cosmos DB detects these compromises early and allows you to set up automation to block bad actors and mitigate the threat.
- Known malicious indicators: Microsoft Defender for Cloud uses the extensive threat intelligence of Microsoft’s security platform, allowing security teams to detect and respond to malicious actors trying to access their databases more effectively.
- Suspicious behavior patterns: Using behavioral modeling over time, Microsoft Defender for Cloud detects suspicious behaviors on your Azure Cosmos DB accounts that can indicate compromised identities, leaked keys, or malicious insiders.
You can find a complete list of Defender for Azure Cosmos DB alerts with the Microsoft Defender for Azure Cosmos DB alerts reference guide.
Easily enable protection for all your database types in Microsoft Defender for Cloud
The new threat protection offering for Azure Cosmos DB is now available in Microsoft Defender for Cloud, alongside a newly designed database-centric enablement experience.
To simplify the process of enabling database protection across the different database types in your cloud and hybrid environments, we created a central management experience across SQL databases, MariaDB, and now Azure Cosmos DB. While each database type requires a tailored approach with custom security controls and uniquely optimized threat detection models, we have standardized the security experience in Microsoft Defender for Cloud across them.
You can enable protection for Azure Cosmos DB at either the subscription level or the resource level, or simply enable protection for all your database types with a single click. For detailed step-by-step instructions, check out our introduction to Microsoft Defender for SQL documentation.
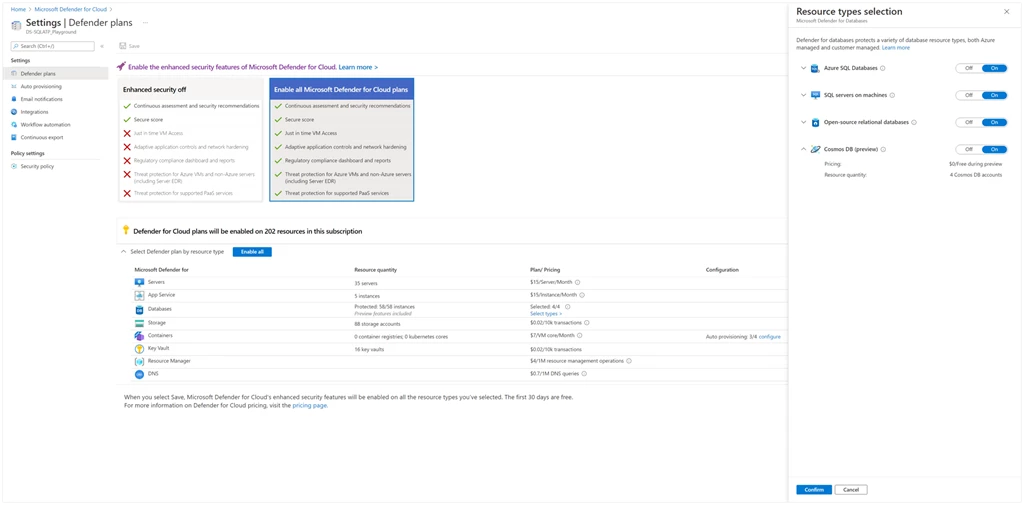
With the addition of support for Azure Cosmos DB, Microsoft Defender for Cloud now provides one of the most comprehensive workload protection offerings for cloud-based databases, giving security teams and database owners a centralized experience to manage database security in their environments.
Microsoft Defender for Cloud is a solution for cloud security posture management (CSPM) and cloud workload protection (CWP) that finds weak spots across your cloud configuration, helps strengthen the overall security posture of your environment, and can protect workloads across multicloud and hybrid environments from evolving threats.
Learn more
- Get started with a free trial.
- Visit our website to learn more about Microsoft Defender for Cloud.
- Check out the product documentation to get started with Microsoft Defender for Azure Cosmos DB.
- Subscribe to our YouTube series for product deep dives!
- Follow us at @MSThreatProtect for the latest news and updates on cybersecurity.
