Today, we are excited to announce the general availability of Transparent Data Encryption (TDE) with Bring Your Own Key (BYOK) support for Azure SQL Database and Azure SQL Data Warehouse. This is one of the most frequently requested features by enterprise customers looking to protect sensitive data and meet regulatory or compliance obligations that require implementation of specific key management controls. TDE with BYOK support is offered in addition to TDE with service managed keys, which is enabled by default on all new Azure SQL Databases.
TDE with BYOK support uses Azure Key Vault, which provides highly available and scalable secure storage for RSA cryptographic keys backed by FIPS 140-2 Level 2 validated Hardware Security Modules (HSMs). Key Vault streamlines the key management process and enables customers to maintain full control of encryption keys and allows them to manage and audit key access.
Customers can generate and import their RSA key to Azure Key Vault and use it with Azure SQL Database and Azure SQL Data Warehouse TDE with BYOK support. Azure SQL Database handles the encryption and decryption of data stored in databases, log files, and backups in a fully transparent fashion by using a symmetric Database Encryption Key (DEK), which is in turn protected using the customer managed key called TDE Protector stored in Azure Key Vault.
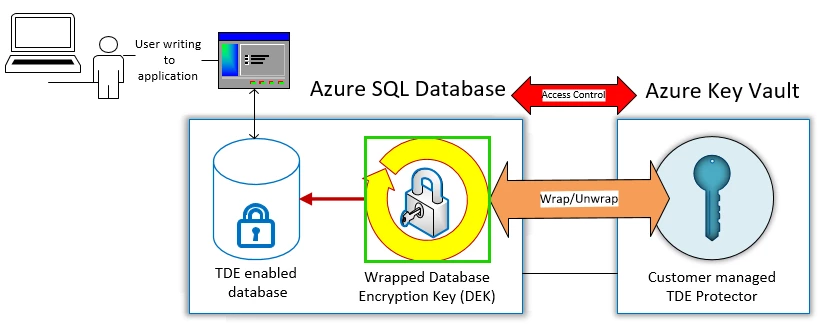
Customers can rotate the TDE Protector in Azure Key Vault to meet their particular security requirements and meet industry specific compliance obligations. When the TDE Protector is rotated, Azure SQL Database detects the new key version within minutes and re-encrypts the DEK used to encrypt data stored in databases. This does not result in re-encryption of the actual data and there is no other action required from the user.
Customers can also revoke access to encrypted databases by revoking access to the databases’ TDE Protector stored in Azure Key Vault. There are several ways to revoke access to keys stored in Azure Key Vault. Please refer to the Azure Key Vault PowerShell and Azure Key Vault CLI documentation for more details. Revoking access in Azure Key Vault will effectively block access to all databases when the TDE Protector is inaccessible by Azure SQL Database.
Azure SQL Database requires “Do Not Purge” and “Soft Delete” to be enabled in Azure Key Vault to protect the TDE Protector against accidental deletion and ransomware scenarios.
Customers can enable TDE with BYOK support on the logical SQL Server level for all available database service tiers, including premium, and can toggle from using TDE with service managed to using customer managed keys. There is no additional charge for enabling this feature.
You can get started today by visiting the Azure portal, REST API documentation, and how-to guide using PowerShell or CLI documentation. To learn more about the feature including best practices and to review our configuration checklist see our Transparent Data Encryption with Bring Your Own Key support documentation.