Hybrid + Multicloud, Microsoft Defender for Cloud, Security
Detecting fileless attacks with Azure Security Center
Posted on
3 min read
As the security solutions get better at detecting attacks, attackers are increasingly employing stealthier methods to avoid detection. In Azure, we regularly see fileless attacks targeting our customers’ endpoints. To avoid detection by traditional antivirus software and other filesystem-based detection mechanisms, attackers inject malicious payloads into memory. Attacker payloads surreptitiously persist within the memory of compromised processes and perform a wide range of malicious activities.
We are excited to announce the general availability of Security Center’s Fileless Attack Detection. With Fileless Attack Detection, automated memory forensic techniques identify fileless attack toolkits, techniques, and behaviors. Fileless Attack Detection periodically scans your machine at runtime and extracts insights directly from the memory of security-critical processes. It finds evidence of exploitation, code injection and execution of malicious payloads. Fileless attack detection generates detailed security alerts to accelerate alert triage, correlation, and downstream response time. This approach complements event-based EDR solutions such as Windows Defender ATP providing greater detection coverage.
In this post, we will dive into the details to see how Security Center’s Fileless Attack Detection discovers different stages of a multi-stage attack, starting with targeted exploit payload, or shellcode. We will also provide a walkthrough of an example alert based on a real-world detection.
Detecting shellcode
After exploiting a vulnerability, attackers typically use a small set of assembly instructions, called shellcode, to retrieve and load more capable payloads. Due to Address Space Layout Randomization (ASLR), shellcode must first locate the addresses of the operating system functions required to retrieve/load additional payloads and transfer execution control to them. A typical shellcode workflow might include: accessing the Process Execution Block (PEB), traversing the in memory order module list to identify OS modules with required capabilities, and parsing PE image headers and image export directories to locate the addresses of specific OS functions.
Additionally, shellcode will often also perform other activities, such as unpacking/decrypting payloads, manipulating permissions and privileges, performing anti-debugging techniques, and hijacking code execution control.
The above patterns can be identified using memory forensic techniques. Fileless Attack Detection reads machine code located in dynamically allocated code segments of commonly targeted processes. Fileless Attack Detection then disassembles the machine code and uses both static analysis and targeted emulation techniques to identify malicious behaviors.
Detecting more complex payloads
Fileless Attack Detection also detects more complex payloads, which can perform any number of malicious activities. Common examples include impersonating the user, escalating privileges through additional software vulnerabilities, stealing account credentials, accessing certificates and private keys, moving laterally to new machines and accessing sensitive data. These capabilities are available in off-the-shelf toolkits which can be reused and modified for the attacker’s purpose. We have seen these types of toolkits used by red teams and attackers.
Fileless Attack Detection identifies such payloads by scanning dynamically allocated code segments for a number of signals, including injected modules, obfuscated modules, references to security sensitive operating system functions, indicators of known fileless attack toolkits, and many others. A classifier analyzes these signals and emits an alert of the appropriate severity. The classifier also filters out signals from legitimate security and management software which often use techniques similar to fileless malware to monitor critical system functions.
Fileless Attack Detection example alert
Below is section-by-section walkthrough of an example alert based on a real world detection.
As you can see in the small red box below, Fileless Attack Detection has identified the toolkit: “Meterpreter.” Below the toolkit name is a list of specific techniques and behaviors present in the memory of the infected process. Even if the attacker uses new or unknown malware, Fileless Attack Detection still generates alerts highlighting the techniques and behaviors detected from the payload.
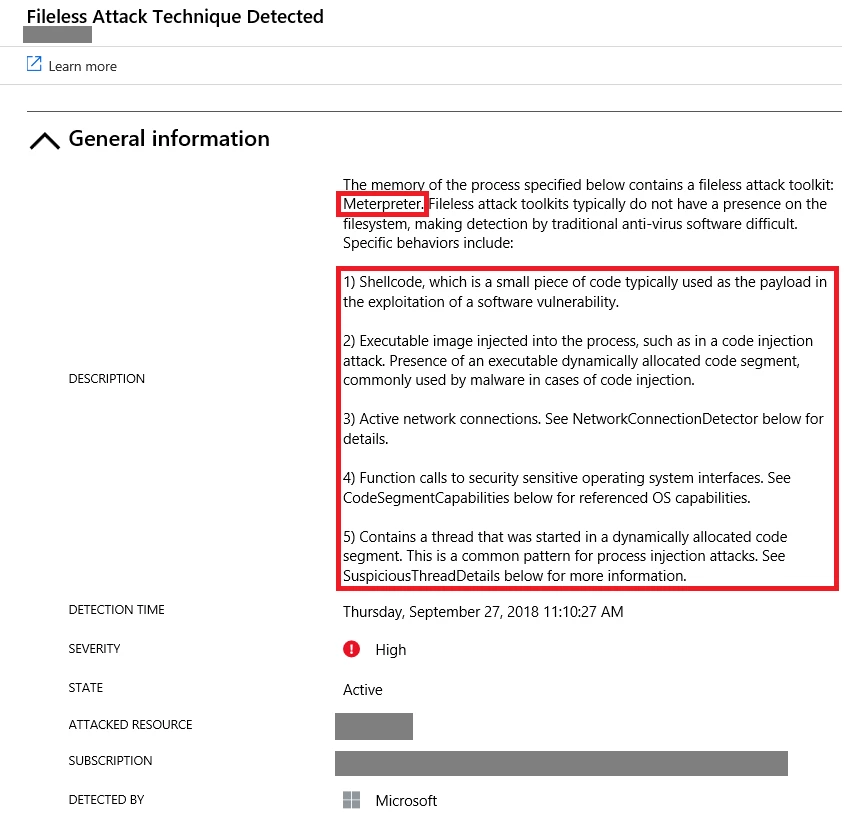
The alert also displays metadata associated with the compromised process. In this case, the infection occurred in winlogon.exe, a long running system process that handles account credentials.

Based only on the above metadata, the process appears to be quite normal. Tools that examine only the process path, command line parameters, or parent/child process relationships will not have sufficient clues to identify the compromise.
However, by using memory forensic techniques, we can determine how many suspicious code segments are present, what capabilities are present in the code segments, find threads executing code from dynamically allocated segments, and emit that information in an alert. Should a process have active network connections, that information will be displayed as well including the remote IP address and start time.
Analysts can also use Log Analytics to create a view of alert data from multiple processes and machines, describing when and where the malicious activity was first detected. Analysts can also use Log Analytics to correlate these alerts with other data sources, such as user logon data, to determine which account credentials may be at risk. This capability is very useful when determining the nature and scope of a compromise.
Getting started with Security Center’s Fileless Attack Detection
Fileless Attack Detection supports both Azure IaaS VMs and virtual machines that run on other clouds or on-premises. Supported operating systems include: Windows Server 2008 R2 and higher, and Windows 7 client and higher.
To learn more about different types of fileless attacks here, visit our documentation.
To start using Fileless Attack Detection, enable the Standard Tier of Security Center for your subscriptions.