Azure DDoS Protection, Networking
Azure Networking May 2018 announcements
Posted on
6 min read
This week is Microsoft Build 2018, our premiere event of the year for our gifted developer audience. With a strong appetite for technology and a desire to learn and immerse themselves in new ways to build and create cloud applications, thousands of software professionals and coders are coming to Seattle this week. We’d like to take this opportunity to let you know about new networking services we have launched as well as enhancements we have made.
As businesses of all sizes increasingly move their mission-critical workloads to Azure, new opportunities arise to simplify the overall network experience, from security and management over monitoring to key areas such as reliability and performance. Launching new services such as DDoS, VNet access to Azure services, zone-aware Application Gateways, a new global scale CDN offering, along with a new and super-fast Load Balancer, we continue to enhance the networking capabilities of Azure and more importantly develop new services and technologies to help customers run, manage, and achieve more when running their most demanding workloads.
Azure DDoS Protection
Last month we announced the general availability (GA) of the Azure DDoS Protection Standard service that provides enhanced DDoS mitigation capabilities for your application and resources deployed in virtual networks (VNets). DDoS Protection can be simply enabled with no application or resource changes so that your services benefit from the same DDoS technologies we use to protect Microsoft. With dedicated monitoring and machine learning that automatically configures DDoS protection policies continuously tuned to your application’s traffic profiles, your services are fully protected.

Please watch our getting started video. More details are in the Azure DDoS Protection service documentation.
VNet Service Endpoints
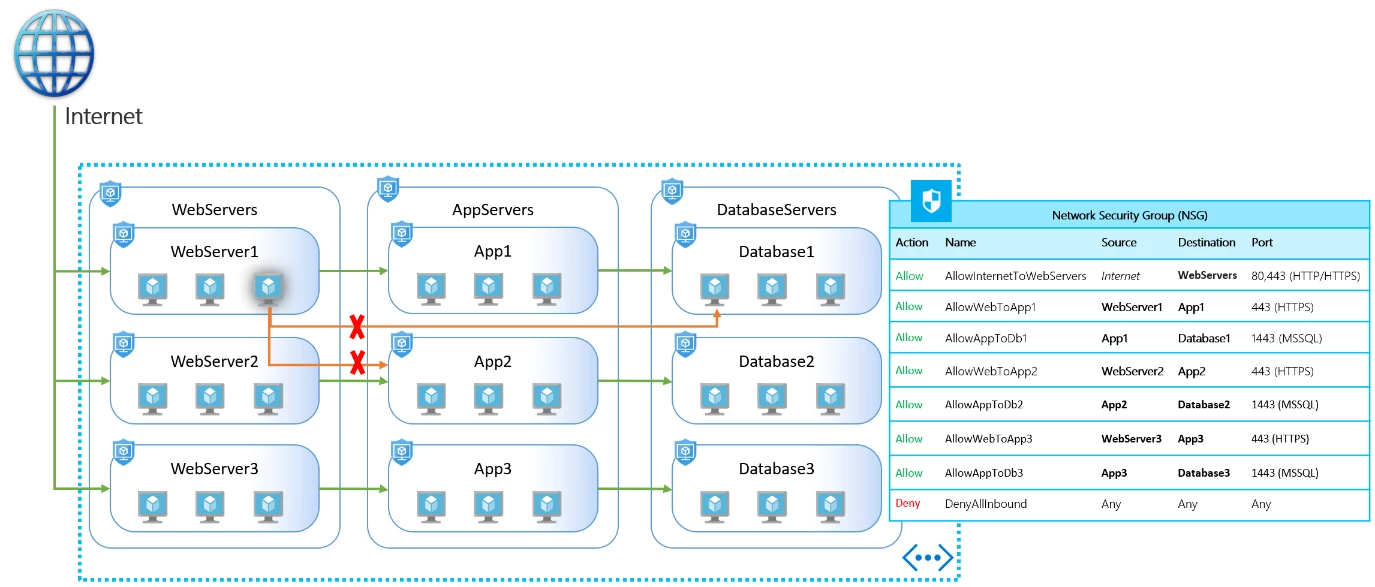
VNet Service Endpoints extend your VNet private address space to Azure services. This allows you to limit access to business-critical Azure resources to only your VNets, fully removing Internet access. All traffic through a service endpoint stays in Azure.
We announced GA of VNet service endpoints for Azure Storage and Azure SQL Database earlier this year. We continue to expand the services accessible via service endpoints and now announce GA for “Azure Cosmos DB service endpoints”. Azure Cosmos DB is the first service to allow cross region access control support where customers can restrict access to globally distributed Azure Cosmos DB accounts from subnets located in multiple regions. For more information, please see VNet Service Endpoints documentation.
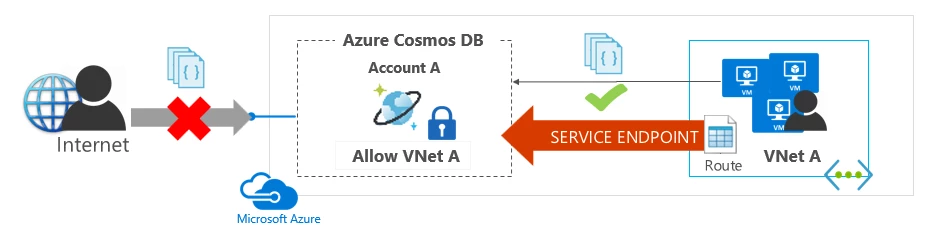
VNet Service Endpoints restricts Azure services to be accessed only from a VNet
Azure DNS enhancements
Azure DNS Private Zones is now in public preview, providing secure and reliable name resolution for your VNets without needing custom DNS servers. You can bring DNS zones to your VNet. You also have the flexibility to use custom domain names, such as your company’s domain name. Private zones provide name resolution both within a VNet and across VNets. You can have private zones span across VNets in the same region as well as across regions and subscriptions.
You can configure zones with a split-horizon view allowing for a private and a public DNS zone to share the same name. This is a common scenario when you want to validate your workloads in a local test environment, before rolling out in production. Since name resolution is confined to configured VNets, you can prevent DNS exfiltration.
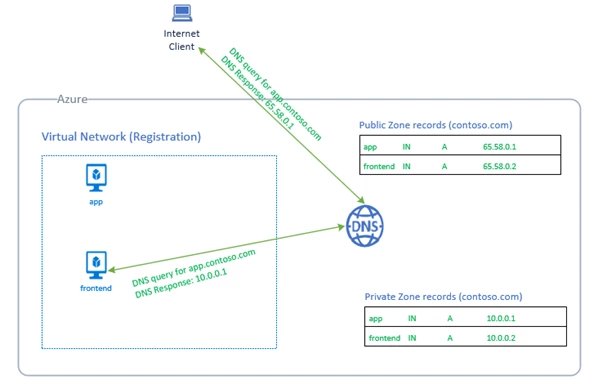
When you designate a VNet as a Registration VNet, Azure dynamically registers DNS and records in the private zone for the all virtual machines (VMs) in this VNet. For more details on Private Zones please see this overview as well as common scenarios.
Azure DNS now provides metrics via the Azure Monitor to enable customers to configure and receive alerts. For details, please see our documentation.
Connection Monitoring
Network Watcher Connection Monitor, now generally available, helps you easily monitor and alert on connectivity and latency from a VM to another VM, FQDN, URI, or IPv4 address with per minute granularity. This reduces the time to detect connectivity problems. You get insights into whether a connectivity issue is due to a platform or a user configuration problem to quickly pinpoint and rectify the problem.
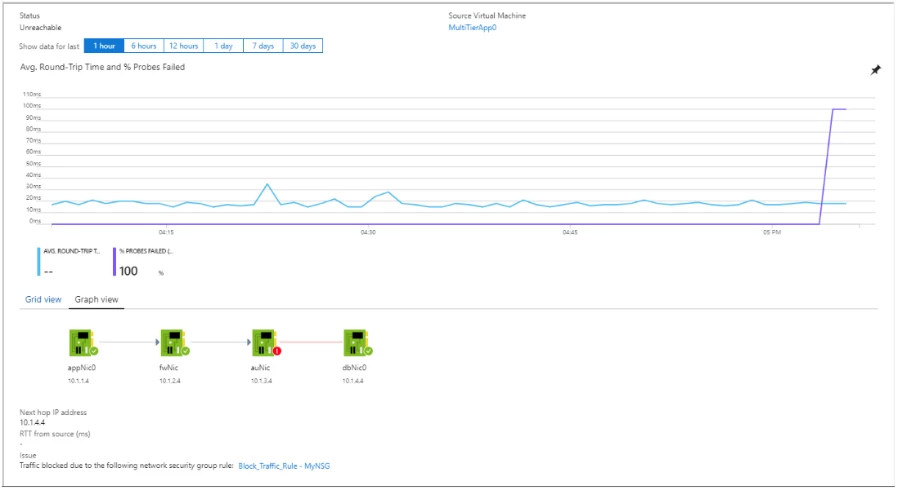
To learn more please visit the Network Watcher Connection Monitor documentation.
Traffic View: Improving performance
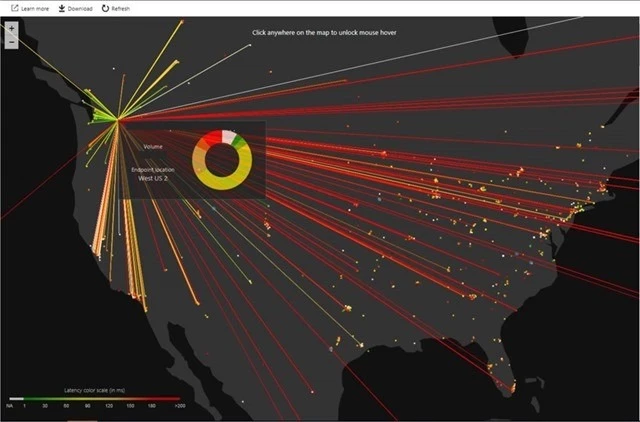
In March we announced the general availability of Traffic View which provides information such as geographic location of your user base, latency experienced from these locations, and traffic volume. The visualizations provided through the Azure portal or analytics tools such as Power BI allows you to optimize the placement of your workloads and learn about your users’ network experience. For more details, please see the Traffic View documentation.
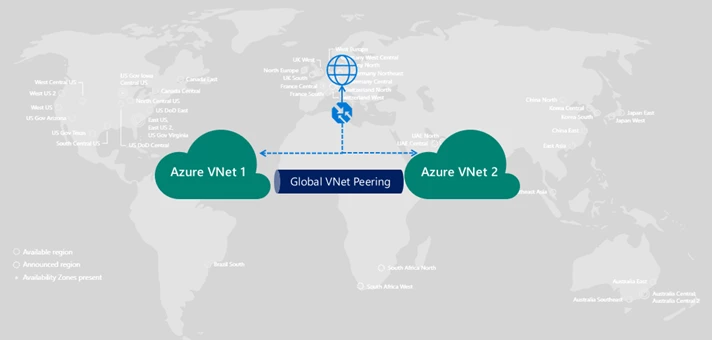
Global VNet Peering
Global VNet Peering, which seamlessly connects your VNets across Azure regions, is now generally available. You can peer your VNets from across the world. Global VNet peering can be configured in under a minute. Once peered, the VNets, appear as one global VNet from a connectivity perspective. Resources within the peered VNets can directly communicate with each other via Microsoft’s global network. Global VNet Peering enables data replication across your VNets so that you can copy data from one location to another for better disaster recovery. To learn more please visit VNet Peering documentation.
Application Security Groups
Application Security Groups (ASG) are now generally available. ASGs enable you to centralize policy configuration and simplify your security management. With ASGs you can define fine-grained network security policies based on workloads, applications, or environments using monikers assigned to virtual machines. This enables you to implement a zero-trust model, limiting access to the application flows that are explicitly permitted. To learn more please see the Application Security Group documentation.
Azure Application Gateway and WAF enhancements
Application Gateway and Web Application Firewall (WAF) provides Application Delivery Controller as a service. HTTP/2 support and enhanced metrics are now available. HTTP/2 aware clients benefit from connection multiplexing and related security and performance enhancements. Communication from Application Gateway to the backend remains over HTTP 1.1.
Enhanced metrics include performance counters such as total connections, total requests, failed requests, summarized response status code distribution, healthy/unhealthy host count, and throughput. These enhancements enable customers to build dashboards and set alerting to better monitor application workloads.
We are also announcing the managed preview for zone redundant Application Gateways and Static VIP. Zone redundant Application Gateways allow you to choose the availability zone or zones where Application Gateway instances are deployed. Static VIP is guaranteed not to change even if the Application Gateway is shut down or restarted. This managed preview also includes infrastructure improvements reducing provisioning time, faster updates, and better SSL connections per second per core. The preview is available in US East 2 with more regions coming soon. Please refer to our preview announcement for updates. Customers can sign up for this preview by following the steps in the preview documentation.
Azure CDN by Microsoft
During Build, we are announcing the public preview of Microsoft as a provider of Azure CDN. You can now use and deliver content from Microsoft’s own global CDN network for all your web facing content. Running at the edge of Microsoft’s Global Network, this new native option is being added alongside existing provider options from Verizon and Akamai and gives you access to the same CDN platform used by Bing and Office 365.
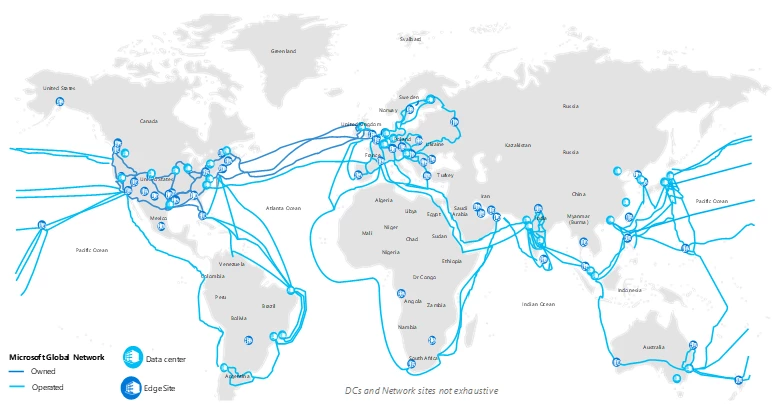
Figure X. Microsoft global network
Azure CDN from Microsoft provides access to 54 global Edge POPs in 33 countries and 16 Regional Cache POPs at network hubs across our fast and reliable anycast network. This translates into 50 ms on average RTT from users to a CDN POP in more than 60 countries.
Standard Load Balancer
Azure Standard Load Balancer is now generally available with increased scale, access to all VMs in the VNet, availability zone support, and private IP load balancing within the VNet. Standard Load Balancer can distribute application traffic to up 1,000 VMs in the backend pool, 10x more than the Basic Load Balancer.
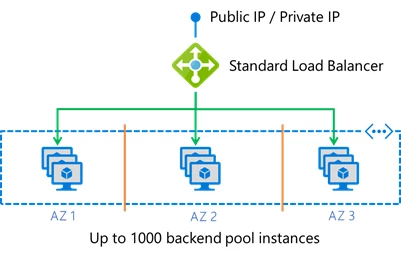
Any VM in the VNet can now be configured to join the backend pool. Customers can combine multiple scale sets, availability sets, and individual VMs in a single backend pool. Multiple frontends can be used simultaneously for outbound flows, increasing the possible number of concurrent outbound connections. We also provide controls over which frontends are chosen when multiple frontends are present. For more information please see the Load Balancer and Outbound Connections documentation.
Standard Load Balancer is designed for use with Availability Zones. Customers can enable zone-redundant frontends for public and internal Load Balancers with a single IP address or align their frontends with IP addresses in specific zones. Cross-zone load balancing delivers traffic to VMs anywhere within the region. The zone-redundant frontend is served simultaneously from all zones. More details can be found in the Standard Load Balancer and Availability Zones documentation.
A new type of load balancing rule for internal Standard Load Balancers provides per flow load balancing across all ports of a private IP address. You can create n-active configurations for network virtual appliances and other scenarios requiring the distribution of traffic across a large number of ports. More details can be found in the HA Ports documentation.
Standard Load Balancer has new telemetry and alerting fully integrated into Azure Monitor providing insights into traffic volumes, inbound connection attempts, outbound connection volume, active in-band data path measurements, and health probes. All of this can be consumed by Azure’s Operations Management Suite and others. For more details, please visit the Standard Load Balancer diagnostics and monitoring documentation.
Summary
As enterprises deploy more workloads into the cloud, the need for better manageability, monitoring, availability, and network security increase. We will continue to provide new, easy to use, and more comprehensive networking services. Stay tuned for more Azure networking services in the coming months! As always, we are very interested in your feedback.