Today, we are excited to announce the general availability of Azure Storage Service Encryption with customer managed keys integrated with Azure Key Vault for Azure Blob and File Storage. Azure customers already benefit from Storage Service Encryption for Azure Blob and File Storage using Microsoft managed keys.
Storage Service Encryption with customer managed keys uses Azure Key Vault that provides highly available and scalable secure storage for RSA cryptographic keys backed by FIPS 140-2 Level 2 validated Hardware Security Modules (HSMs). Key Vault streamlines the key management process and enables customers to maintain full control of keys used to encrypt data, manage, and audit their key usage.
This is one of the most requested features by enterprise customers looking to protect sensitive data as part of their regulatory or compliance needs, HIPAA and BAA compliant.
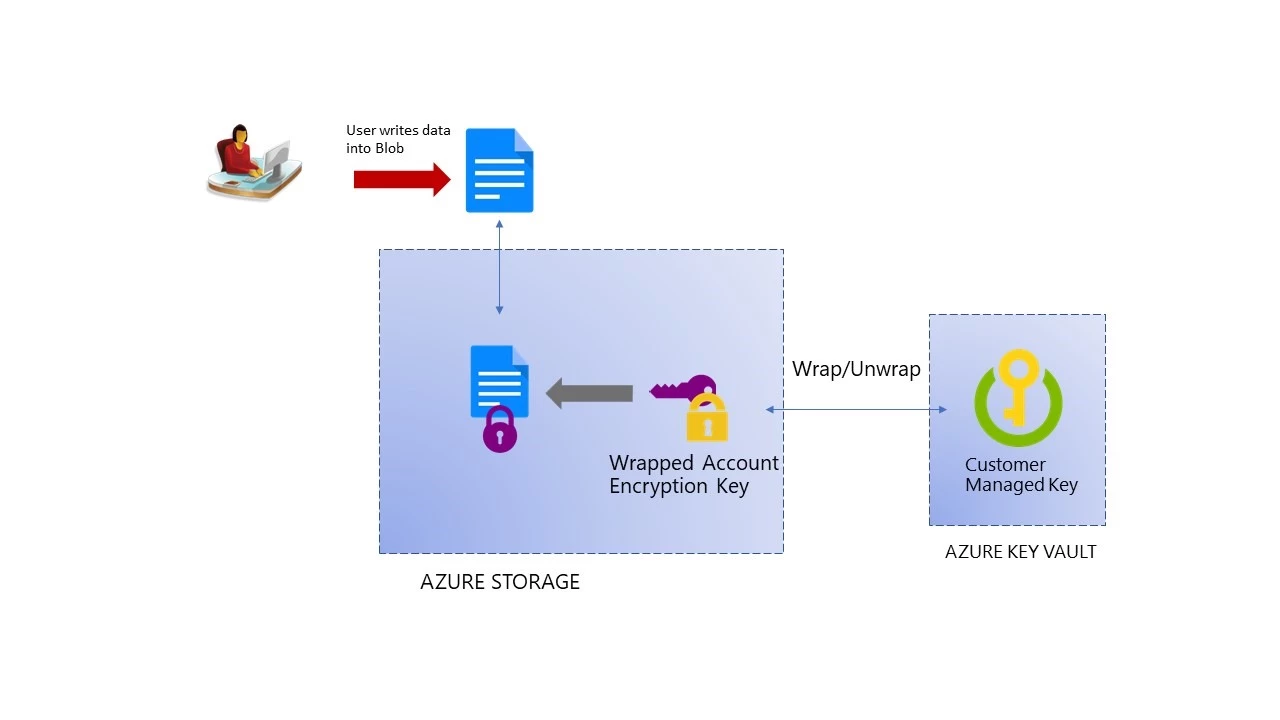
Customers can generate/import their RSA key to Azure Key Vault and use it with Storage Service Encryption. Azure Storage handles the encryption and decryption in a fully transparent fashion using envelope encryption in which data is encrypted using an AES 256 based key, which is in turn protected using the customer managed key stored in Azure Key Vault.
Customers can rotate their key in Azure Key Vault as per their compliance policies. When they rotate their key, Azure Storage re-encrypts the Account Encryption Key for that storage account. This does not result in re-encryption of all data and there is no other action required from the user.
Customers can also revoke access to the storage account by revoking access on their key in Azure Key Vault. There are several ways to revoke access to your keys. Please refer to Azure Key Vault PowerShell and Azure Key Vault CLI for more details. Revoking access will effectively block access to all blobs in the storage account as the Account Encryption Key is inaccessible by Azure Storage.
Customers must enable “Do Not Purge” and “Soft Delete” for customer managed keys that help protect them against ransomware scenarios.
Customers can enable this feature on all available redundancy types of Azure Blob and File storage, including premium storage, and can toggle from using Microsoft managed to using customer managed keys. There is no additional charge for enabling this feature.
You can enable Storage Service Encryption using customer managed keys on any Azure Resource Manager storage account using the Azure portal, Azure PowerShell, Azure CLI, or the Microsoft Azure Storage Resource Provider API.
Find out more about Storage Service Encryption with customer managed keys.
