With special thanks to Pete Bryan, Principal Security Research Manager, Microsoft Security.
The SQL injection attack remains one of the critical attacks in the OWASP Top 10, and it involves injecting a SQL query via the input data field into a web application without input validation. According to Microsoft Digital Defense Report 2022, 67 percent of web application exploits include SQL injections.
Azure Web Application Firewall (Azure WAF) provides centralized protection of your web applications from exploits and vulnerabilities. It protects against OWASP Top 10 attacks, bot attacks, application layer Distributed Denial of Service (DDoS) attacks, and other web attacks.
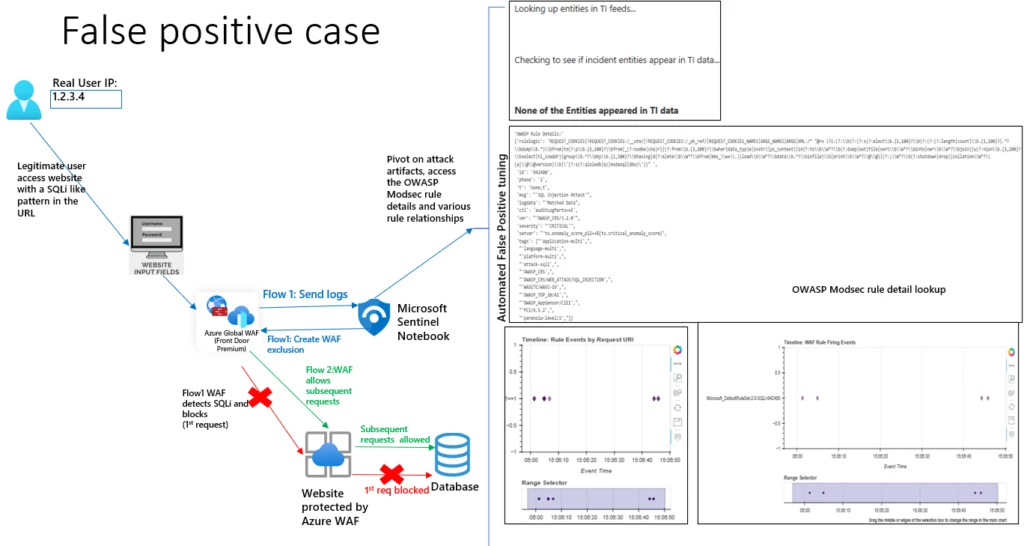
Azure WAF detects SQL injection attacks and blocks them by default. In certain instances, this could be a false positive that requires investigation and creation of Azure WAF exclusions. To complete a successful investigation, full context about the attack is needed and a process that guides you through the investigation is required.
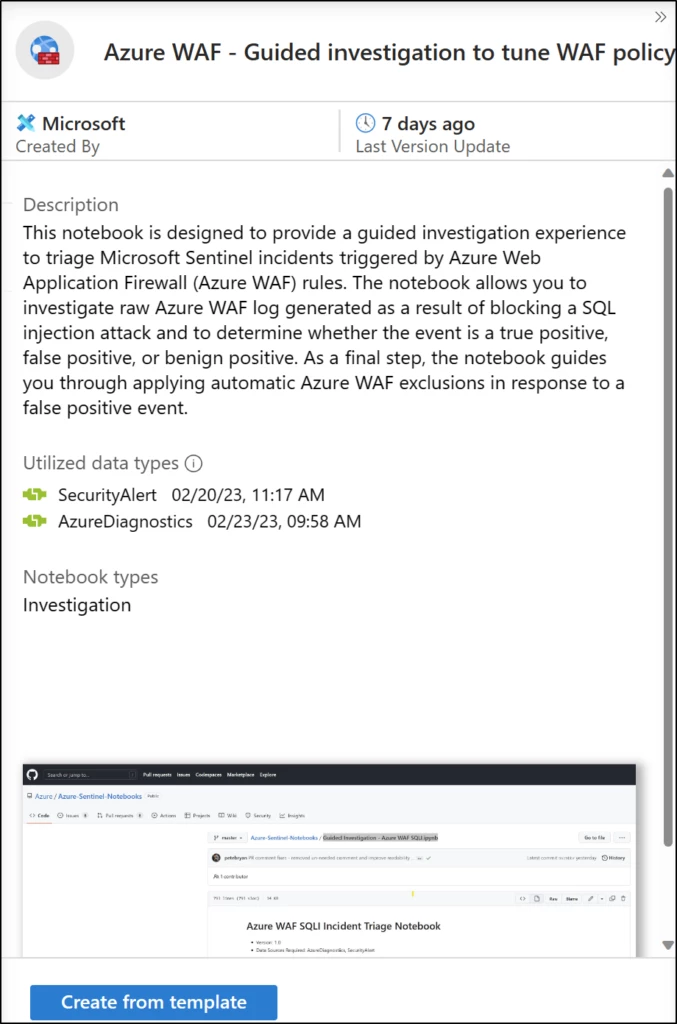
We are pleased to announce a new Azure WAF guided investigation to tune WAF policy Notebook in preview. It guides you through an investigation experience to understand the Azure WAF incidents in Microsoft Sentinel, identify false positives, and automatically apply exclusions to WAF rules to address the false positives. This Notebook allows you to understand the WAF alert and pivot on key entities of the WAF event such as the request URI, client IP, hostname, and correlate with Threat Intelligence feeds to get a holistic view of the attack surface.
Azure WAF investigations powered by Microsoft Sentinel
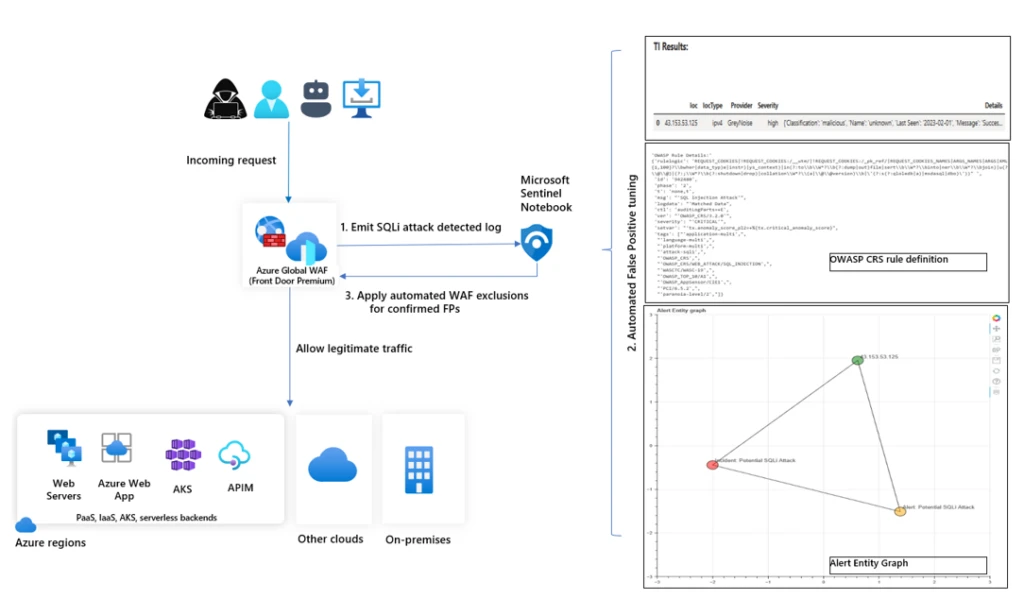
Azure WAF is deeply integrated with Microsoft Sentinel, Microsoft’s Security Information and Event Management (SIEM) solution. Using the existing Azure WAF data connector, WAF logs are ingested and later analyzed for a variety of web application attacks and powerful visualizations pivoting on the full attack pattern are presented to you. This Notebook is built using Microsoft Threat Intelligence Center’s MSTICpy packages. With this Notebook, you can access rich historical contextual information using Microsoft Sentinel’s capabilities like incident generation, entity graph, and threat intelligence correlation, in conjunction with Azure WAF’s SQL injection detections based on OWASP rules and Microsoft Threat Intelligence rules.
Automated investigation and mitigation of web application attacks
Our new Azure WAF guided investigation to tune WAF policy Notebook provides an automated guided investigation for triaging Sentinel incidents triggered by Azure WAF SQL injection rules.
The solution includes the following components:
- Azure WAF data connector in Microsoft Sentinel.
- Microsoft Sentinel incidents that are generated due to SQL injection attack detected by the Microsoft Sentinel analytic rules.
- Azure WAF Notebook that helps investigate Azure WAF logs and automatically applies WAF exclusions to the WAF policy.
A high-level diagram explaining the data flow is given below:
Let us look at two use case scenarios for using this Notebook:
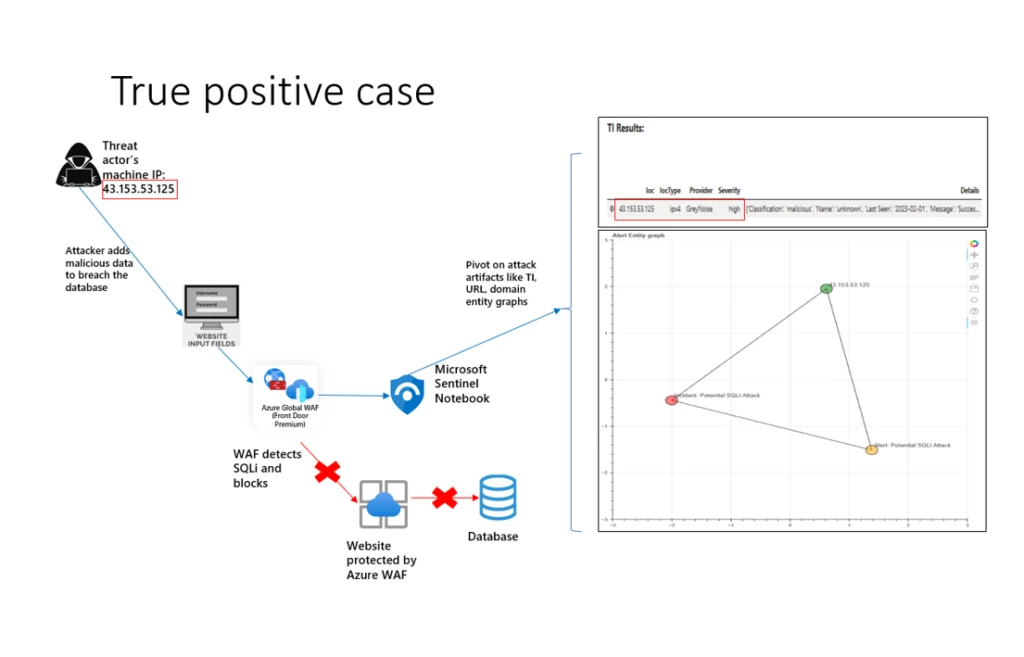
Understanding the attack landscape when there is a true positive
Using the Notebook, you can pivot on various attack artifacts such as IP, URL, or domain threat intelligence, and understand the entity graph. This Notebook retrieves the WAF SQLi rule that generated the detection and looks up related SQLi rule events within the pre-selected time. Based on the above details, if you decide that the SQL injection attack is valid then you can update the incident severity and priority. In this scenario, the web application remains protected by Azure WAF.
Understand the attack pattern and create exclusions if there is a false positive
Using the Notebook, you can pivot on various attack artifacts such as IP, URL, or domain threat intelligence, and understand the entity graph. This Notebook retrieves the WAF SQLi rule that generated the detection and looks up related rule events. It also retrieves raw WAF logs to understand the relations between the request URI, client Ips, hostname entities and allows you to dynamically access the OWASP rule set in GitHub to understand the rule match pattern. Based on the investigations, if you decide this incident is a false positive, the process to automatically create granular exclusions is presented to you and the exclusions are applied to the Azure WAF policy using Azure WAF APIs.
The following personas would benefit from this Notebook:
Persona: Developer at SomeUnionFlight.com
Understanding SQL injection detection logic
Chris is a developer at SomeUnionFlight.com. His company hosts a website for users to search for flights and make flight reservations. They have hosted their website behind WAF with Azure Front Door (AFD) where AFD accepts user requests to search their website. SomeUnionFlight.com has an SQL backend where they store flight information. He notices that when users try to access the website, their access is getting blocked because the URL has “Union” keyword which is triggering the SQL injection rule. This detection is considered as a false positive because the “Union” keyword is used to mention a website name and not an SQL injection attack. He would like an investigation experience that helps him understand how to analyze this detection using Microsoft Sentinel and determine if it is a false positive. He would also like to automatically create exclusions for false positives for the URL without having to disable the entire rule.
Persona: SecOps analyst at Contoso.com
Understanding collateral attack vectors
Ashley is a Security Operations analyst at Contoso.com. Her company has purchased both Azure WAF and Microsoft Sentinel. She oversees analyzing WAF logs and identifying attack patterns. She would like to understand if the client IP or the request URI associated with the WAF rule that triggered the SQL injection are Indicators of Compromise (IoC). By understanding related Threat Intelligence Indicators of Compromises, she can prevent future attacks on her organization.
Get started today
SQL injection attacks are getting more prevalent by the day and Azure WAF protects web applications from these attacks. To enable a high-quality investigation experience for Azure WAF customers, we have created this new Azure WAF guided investigation Notebook that enables you quickly understand full attack surface and take actions on the incidents. You can follow our step-by-step instructions to learn how to use the Notebook.
This new Azure WAF Notebook can be found in Microsoft Sentinel under the Notebooks in the Threat Management section.