A network virtual appliance (NVA) is a virtual appliance primarily focused on network functions virtualization. A typical network virtual appliance involves various layers four to seven functions like firewall, WAN optimizer, application delivery controllers, routers, load balancers, IDS/IPS, proxies, SD-WAN edge, and more. While the public cloud may provide some of these functionalities natively, it is quite common to see customers deploying network virtual appliances from independent software vendors (ISV). These capabilities in the public cloud enable hybrid solutions and are generally available through the Azure Marketplace.
What exactly is the network virtual appliance in the cloud?
A network virtual appliance is often a full Linux virtual machine (VM) image consisting of a Linux kernel and includes user level applications and services. When a VM is created, it first boots the Linux kernel to initialize the system and then starts up any application or management services needed to make the network virtual appliance functional. The cloud provider is responsible for the compute resources, while the ISV provides the image that represents the software stack of the virtual appliance.
Similar to a standard Linux distribution, the Linux kernel is integral to the NVA’s image and is provided by the ISV often customized. The kernel itself includes the drivers needed for all network and disk devices available to the virtual machine. The version and customizations made to the NVA’s kernel will often impact the performance and functionality of the virtual machine, for more information about Linux and accelerated networking see our documentation, “Create a Linux virtual machine with Accelerated Networking.” As new networking enhancements are made to the Azure platform such as performance improvements or even entirely new networking features, the ISV may need to update the software image to provide support for those enhancements. Often, this entails updating their version of the Linux kernel from the upstream Linux project. For the latest updates, see the Linux Kernel Archives website.
All NVA images published in the Azure Marketplace go through rigorous testing and onboarding workflows. As part of Azure’s continuous integration and deployment life cycle, NVA images are deployed and tested in a pre-production environment for any regression or issues. ISVs are responsible for publishing deployment guidelines and GithHub published Azure Resource Manager (ARM) templates for their specific products. Technical and performance specifications of the appliance are owned by the ISVs, while Microsoft owns the technical and performance specifications of the host environment. Technical support for the customer’s virtual appliance, it’s features, recommended OS version, kernel version, and security updates are provided by the ISV.
Pricing for NVA solutions may vary based on product types and publisher specifications. Software license fees and Microsoft Azure usage costs are charged separately through the Azure subscription. Learn more by visiting our list of Marketplace FAQs related to virtual appliance and Azure marketplace.
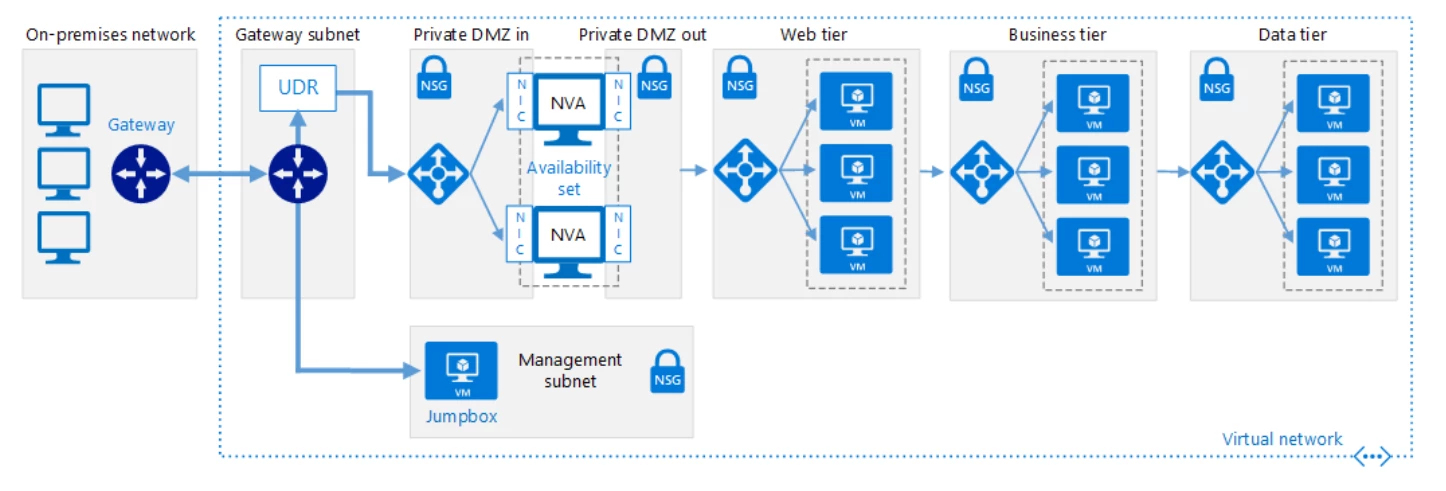
Below is an example of a hybrid network that extends an on-premises network to Azure. Demilitarized zone (DMZ) represents a perimeter network between on-premises and Azure, which includes NVAs.
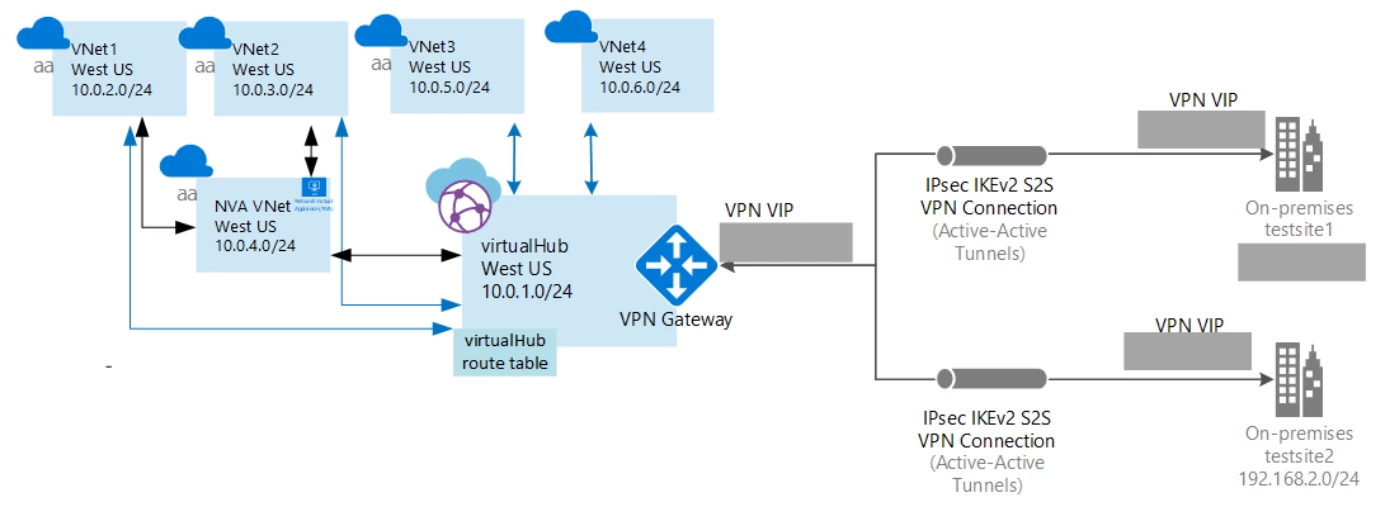
Another example below shows a NVA with Azure Virtual WAN. For more details on how to steer traffic from a Virtual WAN hub to a network virtual appliance please visit our documentation, “Create Virtual Hub route table steer traffic to a Network Virtual Appliance.”
Common best practices
Microsoft continues to collaborate with multiple ISVs to improve cloud experience for Microsoft customers.
- Azure accelerated networking support: Consider a virtual appliance that is available on one of the supported VM types with Azure’s accelerated networking capability. Accelerated networking enables single root I/O virtualization (SR-IOV) to a VM, greatly improving its networking performance. This high-performance path bypasses the host from the datapath, reducing latency, jitter, and CPU utilization for use with the most demanding network workloads on supported VM types. Accelerated networking is supported on most general purpose and compute-optimized instance sizes with two or more vCPUs. For a list of supported OS and additional information visit our documentation, “Create a Windows virtual machine with Accelerated Networking.”
- Multi-NIC support: A network interface (NIC) is the interconnection between a VM and a virtual network (VNet). A VM must have at least one NIC, but can have more than one depending on the size of the VM you create. Learn about how many NICs each VM size supports for Windows and Linux in our documentation, “Sizes for Windows virtual machines in Azure” or “Sizes for Linux virtual machines in Azure.” Many network virtual appliances require multiple NICs. With multiple NICs you can better manage your network traffic by isolating various types of traffic across the different NICs. A good example would be separating data plane traffic from the management plane and hence the VM supporting at least two NICs. A VM can only have as many network interfaces attached to it as the VM size supports. If you are considering adding a NIC after deploying the NVA, be sure to Enable IP forwarding on the NIC. The setting disables Azure’s check of the source and destination for a network interface. Learn more about how to enable IP forwarding for a network interface.
- HA Port with Azure Load Balancer: Azure Standard Load Balancer helps you load-balance TCP and UDP flows on all ports simultaneously when you’re using an internal load balancer. A high availability (HA) port load balancing rule is a variant of a load balancing rule, configured on an internal Standard Load Balancer. You would want your NVA to be reliable and highly available, to achieve these goals simply by adding NVA instances to the back-end pool of your internal load balancer and configuring a HA ports load-balancer rule. For more information on HA port overview please visit our documentation, “High availability ports overview.”
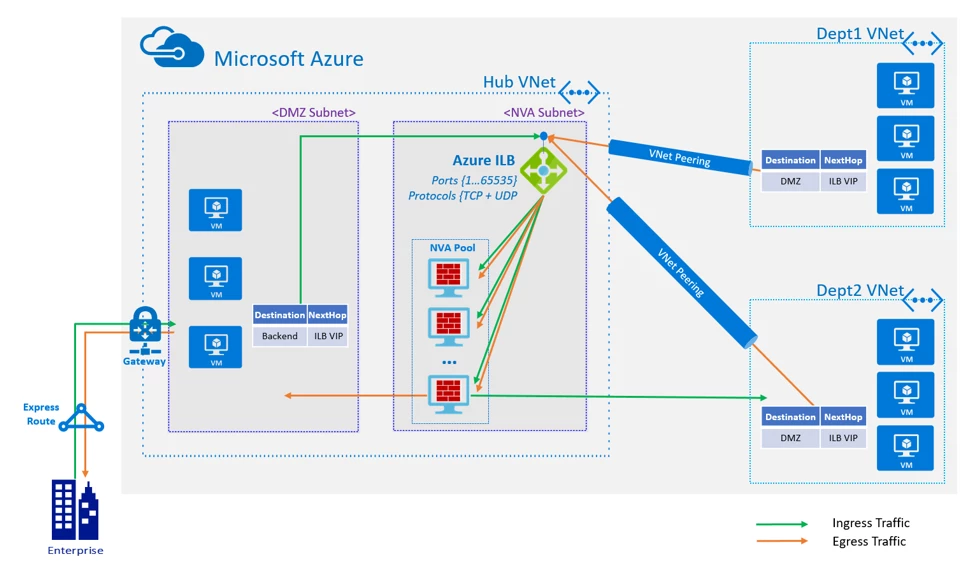
- Support for Virtual Machine Scale Sets (VMSS): Azure Virtual Machine Scale Sets let you create and manage a group of identical, load balanced VMs. The number of VM instances can automatically increase or decrease in response to a demand or a defined schedule. Scale sets provide high availability to your applications, and allow you to centrally manage, configure, and update a large number of VMs. Scale sets are built from virtual machines. With scale sets, the management and automation layers are provided to run and scale your applications. For more information visit our documentation, “What are virtual machine scale sets.”
As enterprises move ever demanding mission-critical workloads to the cloud, it is important to consider comprehensive networking services that are easy to deploy, manage, scale, and monitor. We are fully committed to providing you the best network virtual appliance experience that can provide all the benefits of cloud in conjunction with your network needs. Picking a virtual appliance can be an important decision when you are designing your network. We want to ensure you do so for ease of use, scale, and a better future together.
