This blog post was co-authored by Anupam Vij, Principal PM Manager, and Syed Pasha, Principal Network Engineer, Azure Networking
In the second half of 2021, the world experienced an unprecedented level of Distributed Denial-of-Service (DDoS) activity in both complexity and frequency. The gaming industry was perhaps the hardest hit, with DDoS attacks disrupting gameplay of Blizzard games1, Titanfall2, Escape from Tarkov3, Dead by Daylight4, and Final Fantasy 145 among many others. Voice over IP (VoIP) service providers such as Bandwidth.com6, VoIP Unlimited7, and VoIP.ms8 suffered outages following ransom DDoS attacks. In India, we saw a 30-fold increase of DDoS attacks during the nation’s festive season in October9 with multiple broadband providers targeted, which shows that the holidays are indeed an attractive time for cybercriminals. As we highlighted in the 2021 Microsoft Digital Defense Report, the availability of DDoS for-hire services as well as the cheap costs—at only approximately $300 USD per month—make it extremely easy for anyone to conduct targeted DDoS attacks.
At Microsoft, despite the evolving challenges in the cyber landscape, the Azure DDoS Protection team was able to successfully mitigate some of the largest DDoS attacks ever, both in Azure and in the course of history. In this review, we share trends and insights into DDoS attacks we observed and mitigated throughout the second half of 2021.
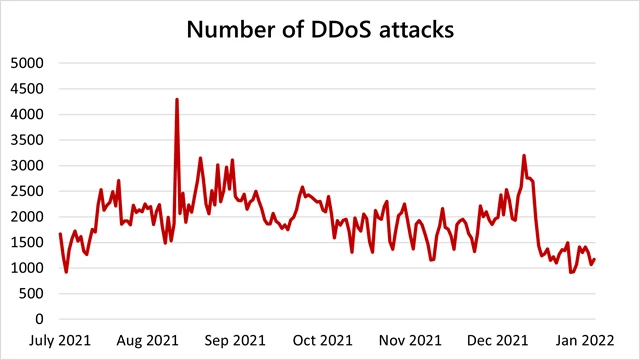
August recorded the highest number of attacks
Microsoft mitigated an average of 1,955 attacks per day, a 40 percent increase from the first half of 2021. The maximum number of attacks in a day recorded was 4,296 attacks on August 10, 2021. In total, we mitigated upwards of 359,713 unique attacks against our global infrastructure during the second half of 2021, a 43 percent increase from the first half of 2021.
Interestingly, there was not as much of a concentration of attacks during the end-of-year holiday season compared to previous years. We saw more attacks in Q3 than in Q4, with the most occurring in August, which may indicate a shift towards attackers acting all year round—no longer is holiday season the proverbial DDoS season! This highlights the importance of DDoS protection all year round, and not just during peak traffic seasons.
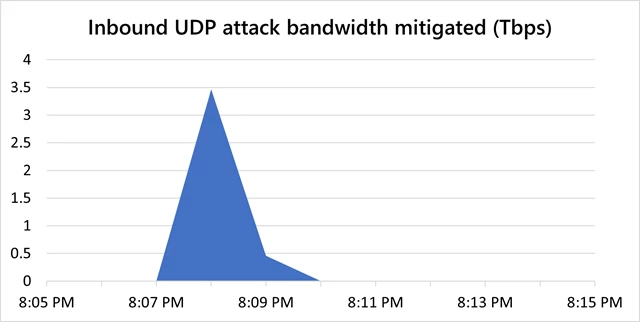
Microsoft mitigated a 3.47 Tbps attack, and two more attacks above 2.5 Tbps
Last October, Microsoft reported on a 2.4 terabit per second (Tbps) DDoS attack in Azure that we successfully mitigated. Since then, we have mitigated three larger attacks.
In November, Microsoft mitigated a DDoS attack with a throughput of 3.47 Tbps and a packet rate of 340 million packets per second (pps), targeting an Azure customer in Asia. We believe this to be the largest attack ever reported in history.
This was a distributed attack originating from approximately 10,000 sources and from multiple countries across the globe, including the United States, China, South Korea, Russia, Thailand, India, Vietnam, Iran, Indonesia, and Taiwan. Attack vectors were UDP reflection on port 80 using Simple Service Discovery Protocol (SSDP), Connection-less Lightweight Directory Access Protocol (CLDAP), Domain Name System (DNS), and Network Time Protocol (NTP) comprising one single peak, and the overall attack lasted approximately 15 minutes.
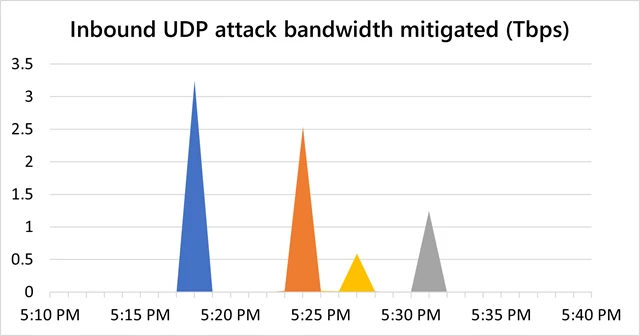
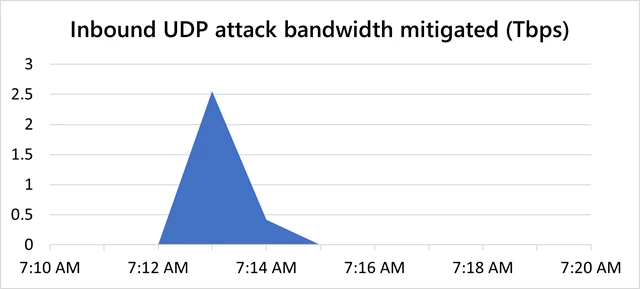
In December, we mitigated two more attacks that surpassed 2.5 Tbps, both of which were again in Asia. One was a 3.25 Tbps UDP attack in Asia on ports 80 and 443, spanning more than 15 minutes with four main peaks, the first at 3.25 Tbps, the second at 2.54 Tbps, the third at 0.59 Tbps, and the fourth at 1.25 Tbps. The other attack was a 2.55 Tbps UDP flood on port 443 with one single peak, and the overall attack lasted just a bit over five minutes.
In these cases, our customers do not have to worry about how to protect their workloads in Azure, as opposed to running them on-premises. Azure’s DDoS protection platform, built on distributed DDoS detection and mitigation pipelines, can scale enormously to absorb the highest volume of DDoS attacks, providing our customers the level of protection they need. The service employs fast detection and mitigation of large attacks by continuously monitoring our infrastructure at many points across the Microsoft global network. Traffic is scrubbed at the Azure network edge before it can impact the availability of services. If we identify that the attack volume is significant, we leverage the global scale of Azure to defend the attack from where it is originating.
Short burst and multi-vector attacks remain prevalent, although more attacks are lasting longer
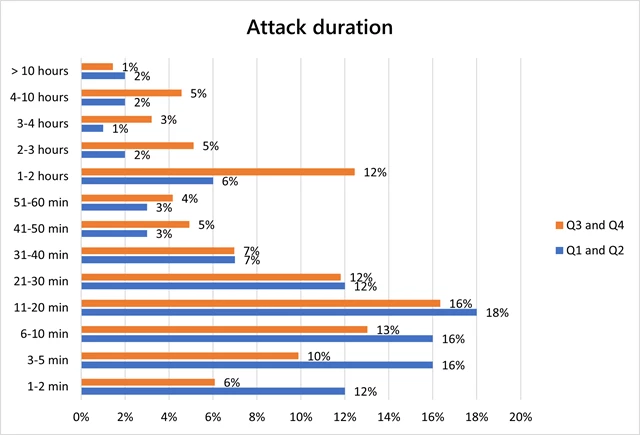
As with the first half of 2021, most attacks were short-lived, although, in the second half of 2021, the proportion of attacks that were 30 minutes or less dropped from 74 percent to 57 percent. We saw a rise in attacks that lasted longer than an hour, with the composition more than doubling from 13 percent to 27 percent. Multi-vector attacks continue to remain prevalent.
It’s important to note that for longer attacks, each attack is typically experienced by customers as a sequence of multiple short, repeated burst attacks. One such example would be the 3.25 Tbps attack mitigated, which was the aggregation of four consecutive short-lived bursts that each ramped up in seconds to terabit volumes.
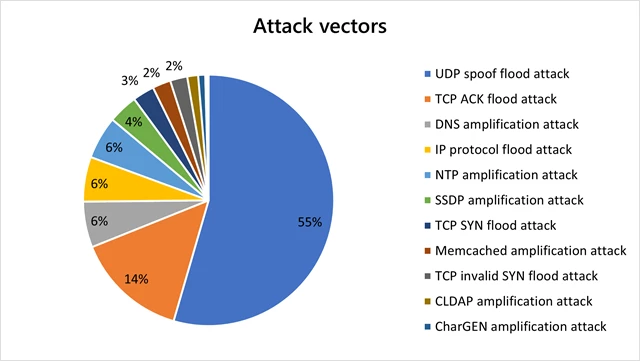
UDP spoof floods dominated, targeting the gaming industry
UDP attacks rose to the top vector in the second half of 2021, comprising 55 percent of all attacks, a 16 percent increase from the first half of 2021. Meanwhile, TCP attacks decreased from 54 percent to just 19 percent. UDP spoof floods was the most common attack type (55 percent), followed by TCP ACK floods (14 percent) and DNS amplification (6 percent).
Gaming continues to be the hardest hit industry. The gaming industry has always been rife with DDoS attacks because players often go to great lengths to win. Nevertheless, we see that a wider range of industries are just as susceptible, as we have observed an increase in attacks in other industries such as financial institutions, media, internet service providers (ISPs), retail, and supply chain. Particularly during the holidays, ISPs provide critical services that power internet phone services, online gaming, and media streaming, which make them an attractive target for attackers.
UDP is commonly used in gaming and streaming applications. The majority of attacks on the gaming industry have been mutations of the Mirai botnet and low-volume UDP protocol attacks. An overwhelming majority were UDP spoof floods, while a small portion were UDP reflection and amplification attacks, mostly SSDP, Memcached, and NTP.
Workloads that are highly sensitive to latency, such as multiplayer game servers, cannot tolerate such short burst UDP attacks. Outages of just a couple seconds can impact competitive matches, and outages lasting more than 10 seconds typically will end a match. For this scenario, Azure recently released the preview of inline DDoS protection, offered through partner network virtual appliances (NVAs) that are deployed with Azure Gateway Load Balancer. This solution can be tuned to the specific shape of the traffic and can mitigate attacks instantaneously without impacting the availability or performance of highly latency-sensitive applications.
Huge increase in DDoS attacks in India, East Asia remains popular with attackers
The United States remains the top attacked destination (54 percent). We saw a sharp uptick in attacks in India, from just 2 percent of all attacks in the first half of 2021 to taking the second position at twenty-three percent of all attacks in the second half of 2021. East Asia (Hong Kong) remains a popular hotspot for attackers (8 percent). Interestingly, relative to other regions, we saw a decrease in DDoS activity in Europe, dropping from 19 percent in the first half of 2021 to 6 percent in the second half.
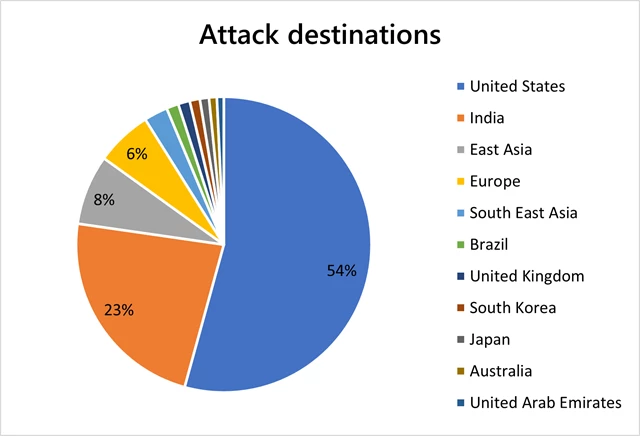
The concentration of attacks in Asia can be largely explained by the huge gaming footprint10, especially in China, Japan, South Korea, Hong Kong, and India, which will continue to grow as the increasing smartphone penetration drives the popularity of mobile gaming in Asia. In India, another driving factor may be that the acceleration of digital transformation, for example, the “Digital India” initiative11, has increased the region’s overall exposure to cyber risks.
Defended against new attack vectors
During the October-to-December holiday season, we defended against new TCP PUSH-ACK flood attacks that were dominant in the East Asia region, namely in Hong Kong, South Korea, and Japan. We observed a new TCP option manipulation technique used by attackers to dump large payloads, whereby in this attack variation, the TCP option length is longer than the option header itself.
This attack was automatically mitigated by our platform’s advanced packet anomaly detection and mitigation logic, with no intervention required and no customer impact at all.
Protect your workloads from DDoS attacks with Microsoft
As the world moves towards a new era of digitalization with the expansion of 5G and IoT, and with more industries embracing online strategies, the increased online global footprint means that the threat of cyberattacks will continue to grow. As we have witnessed that DDoS attacks are now rampant even during non-festive periods, it is crucial for businesses to develop a robust DDoS response strategy all year round, and not just during the holiday season.
At Microsoft, the Azure DDoS Protection team protects every property in Microsoft and the entire Azure infrastructure. Our vision is to protect all internet-facing workloads in Azure, against all known DDoS attacks across all levels of the network stack.
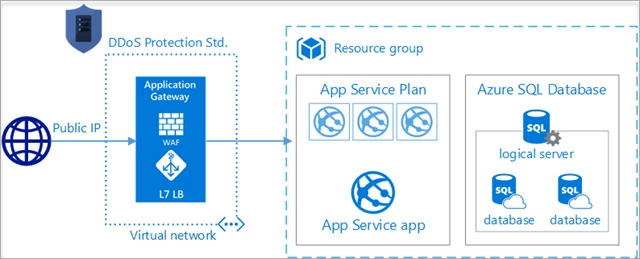
Combine DDoS Protection Standard with Application Gateway Web Application Firewall for comprehensive protection
When combined with DDoS Protection Standard, Application Gateway web application firewall (WAF), or a third-party web application firewall deployed in a virtual network with a public IP, provides comprehensive protection for L3-L7 attacks on web and API assets. This also works if you are using Azure Front Door alongside Application Gateway WAF, or if your backend resources are in your on-premises environment.
If you have PaaS web application services running on Azure App Service or Azure SQL Database, you can host your application behind an Application Gateway and WAF and enable DDoS Protection Standard on the virtual network which contains the Application Gateway and WAF. In this scenario, the web application itself is not directly exposed to the public Internet and is protected by Application Gateway WAF and DDoS Protection Standard. To minimize any potential attack surface area, you should also configure the web application to accept only traffic from the Application Gateway public IP address and block unwanted ports.
Use inline DDoS protection for latency-sensitive workloads
If you have workloads that are highly sensitive to latency and cannot tolerate short burst DDoS attacks, we recently released the preview of inline DDoS protection, offered through partner network virtual appliances (NVAs) that are deployed with Azure Gateway Load Balancer. Inline DDoS protection mitigates even short-burst low-volume DDoS attacks instantaneously without impacting the availability or performance of highly latency-sensitive applications.
Optimize SecOps with Azure Firewall Manager
DDoS Protection Standard is automatically tuned to protect all public IP addresses in virtual networks, such as those attached to an IaaS virtual machine, Load Balancer (Classic and Standard Load Balancers), Application Gateway, and Azure Firewall Manager. In addition to Azure Firewall policy management, Azure Firewall Manager, a network security management service, now supports managing DDoS Protection Standard for your virtual networks. Enabling DDoS Protection Standard on a virtual network will protect the Azure Firewall and any publicly exposed endpoints that reside within the virtual network.
Learn more about Azure DDoS Protection Standard
• Azure DDoS Protection Standard product page.
• Azure DDoS Protection Standard documentation.
• Azure DDoS Protection Standard reference architectures.
• DDoS Protection best practices.
• Azure DDoS Rapid Response.
• DDoS Protection Standard pricing and SLA.
1Overwatch, World of Warcraft Go Down After DDoS | Digital Trends
2After years of struggling against DDoS attacks, Titanfall is being removed from sale | PC Gamer
3‘Escape From Tarkov’ suffers sustained server issues in possible DDoS attacks (nme.com)
4Dead by Daylight streamers are being DDoS attacked
5‘Final Fantasy 14’ EU servers affected by DDoS attack (nme.com)
6Bandwidth CEO confirms outages caused by DDoS attack | ZDNet
7DDoS Attack Hits VoIP and Internet Provider VoIP Unlimited Again UPDATE2 – ISPreview UK
8VoIP company battles massive ransom DDoS attack | ZDNet
930-fold increase in DDoS cyber attacks in India in festive season (ahmedabadmirror.com)
10Gaming industry in Asia Pacific – statistics and facts | Statista
