The Azure Container Registry team is sharing the preview of customer-managed keys for data encryption at rest. Azure Container Registry already encrypts data at rest using service-managed keys. With the introduction of customer-managed keys you can supplement default encryption with an additional encryption layer using keys that you create and manage in Azure Key Vault. This additional encryption should help you meet your company’s regulatory or compliance needs.
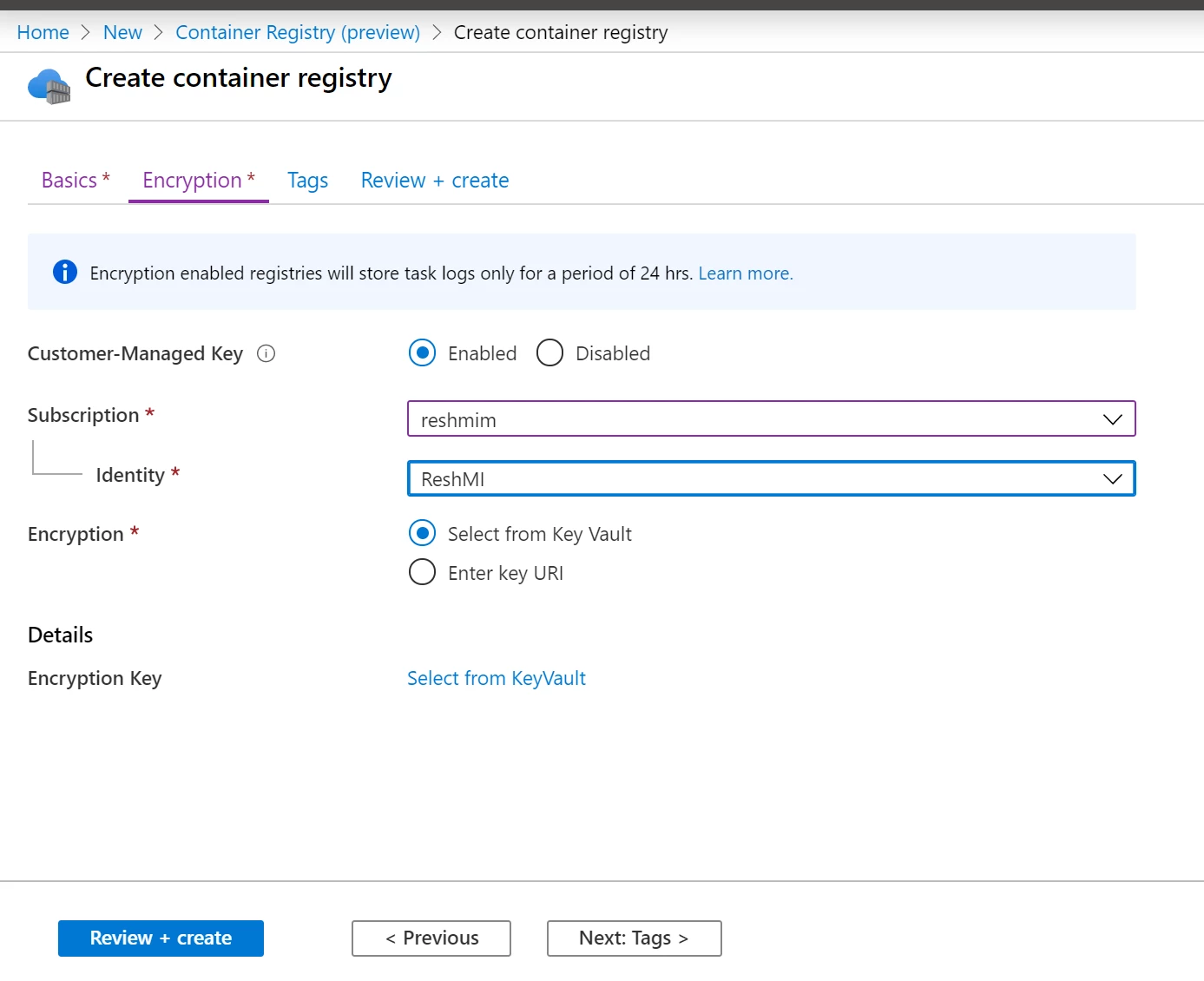
Azure Container Registry encryption is supported through integration with Azure Key Vault. You can create your own encryption keys and store them in a Key Vault, or you can use Azure Key Vault API to generate encryption keys. With Azure Key Vault, you can also audit key usage.
During preview, customer-managed keys can only be enabled while creating a new registry in the Premium SKU. Enabling and disabling the feature on an existing registry will be available in an upcoming release.
With this release, you can try out the following scenarios on a customer-managed keys enabled registry:
- Rotate the encryption keys using the Azure portal or the Azure command-line interface (CLI).
- Geo-replicated registries and Virtual Network integration are supported.
- You can enforce encryption for your registries through the built-in Azure Policy.
You can try out this feature using Azure Portal or the Azure CLI. For details, please see the documentation.
Availability and feedback
The Azure portal and CLI experience for customer-managed keys in Azure Container Registry are now in preview. As always, we love to hear your feedback on existing features as well as ideas for our product roadmap.
Roadmap: For visibility into our planned work.
UserVoice: To vote for existing requests or create a new request.
Issues: To view existing bugs and issues or log new ones.
ACR documents: For Azure Container Registry tutorials and documentation.
