This blog post was co-authored by Sonia Cuff, Senior Cloud Advocate Azure
With an increasingly complex security landscape and an ever-growing service partner portfolio, how do you stay on top of industry-standard best practices? As your business needs grow, you employ more and more partners to support your infrastructure, network, apps, and employees, but with that support comes a required level of access—how do you keep track of who has access to what and what exactly they’re doing to your resources?
Typically, when working with a Managed Service Provider (MSP) to manage your Azure estate, you would provision guest identities for the service partner within the Azure tenant, where the resources live. While this gives you full control over the service partner’s footprint on your environment, this option often involves significant overhead on your end.
For example, you need to ensure timely deprovisioning of service partner identities when that identity is no longer associated with an engagement in your estate. Many customers often overcome some of the associated overhead by giving named accounts from the service partner a higher level of role-based access control over a larger scope than required—sometimes to their entire Azure tenant. While contributor or privileged access is critical for service partners to deliver certain services, not every operator at the service partner needs this level of standing access. However, the associated overhead of managing tens or hundreds of service partner identities, sometimes for multiple service partners, is expensive and laborious for many customers.
You need a solution to give you peace of mind that your partners can efficiently support your organization without compromising security—something that enables zero-trust security and least-privileged access principles with just enough and just-in-time access to granular scopes.
Azure Lighthouse helps you take control, stay secure, and be informed. Let’s take a look at the top four reasons why our customers are asking their service partners for Azure Lighthouse.
1. Securely onboard a service provider with Azure Lighthouse
Customers can access service partner offers in the marketplace or through deployed Azure Resource Manager (ARM) templates. These offers specify which users, groups, and automation accounts need authorization in order to deliver the managed service. For example, you may see an offer that grants all service partner support agents Reader access to your Azure subscription with only certain members gaining Backup Contributor access.
You can review these offers with service partners before deploying them, selecting only the scopes (subscriptions and resource groups) you want the partner to manage, giving you more control and granularity over who can do what in your environment.
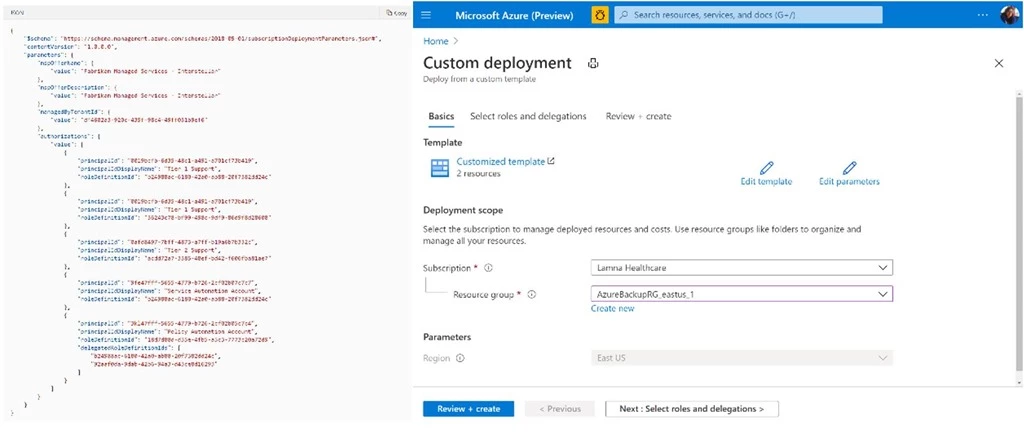
Figure 1: An example of an Azure Lighthouse ARM template offer and customer ARM template deployment workflow from the Azure Portal
2. View and manage your service partners in a centralized control plane
The Azure Lighthouse Service Providers experience in the Azure portal provides details about your service partners and their related Azure Lighthouse offers, allowing you to delegate specific resources and update to the latest versions of the offers, and discover other service partner offers. At any time, you can remove a service partner’s access by deleting the delegation from within your Azure portal. This also means reduced overhead —for example, you do not have to keep up to date with any changes made to employees that aren’t your staff. If the service partner is using groups in their Azure Lighthouse offers, they can manage the group membership on their own tenant. If the service provider is using individual named users or automation accounts, then you can view and update to the latest Azure Lighthouse offer from the service partner.
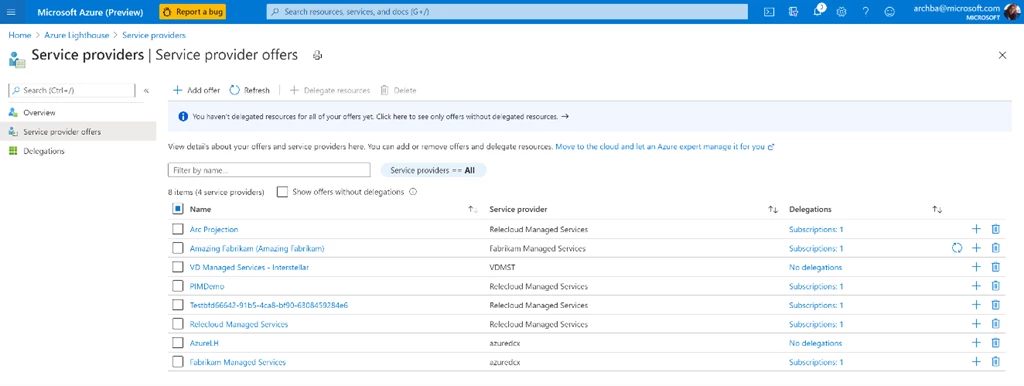
Figure 2: An example of a customer using Azure Lighthouse to manage multiple service providers
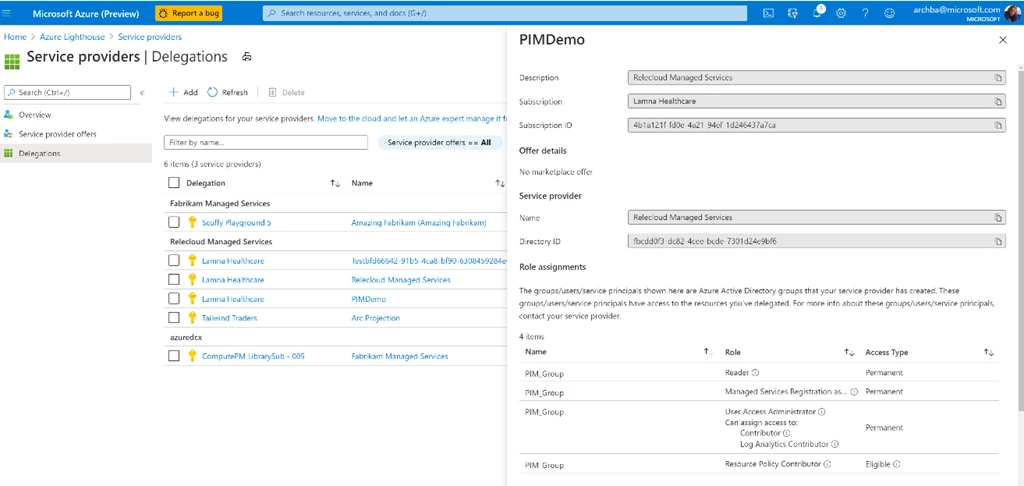
Figure 3: An example of a customer using Azure Lighthouse to view delegation details for a specific subscription managed by the service provider
3. Gain full visibility into changes made by the service partner in your Azure environment
With Azure Lighthouse, you can view Azure Activity Logs from your Azure Tenant, filter to scopes delegated to a service partner, and view all create, read, update, and delete (CRUD) actions taken against these Azure resources (for example, creating, updating, or deleting resources). If any individual or service principal from the service partner acts against a customer resource, the associated contact email will be logged against that action in your activity log, giving you full visibility into any changes made by the service partner on delegated scopes. Additionally, actions against this service partner’s activity are still governed—for example, Azure policies that you might have specified at a higher-scope, such as a management group, will still be enforced against service partner activity.
4. Enable further granularity and security with privileged identity management and MFA private preview
At Microsoft Inspire 2020, Azure Lighthouse announced an integration with Azure Privileged Identity Management (PIM) in private preview. The integration allows Azure Lighthouse offers to now be authored to require service partner operators to elevate to a privileged role and/or use Azure Multi-factor Authentication (MFA) before performing privileged operations on your scopes. (Currently, the Azure AD P2 or E5 license is only required on the service partner’s tenant, irrespective of the Azure AD SKU the customer may have.)
Customers can review the access type (permanent or eligible) and MFA enforcement (Azure MFA or none) within the Azure Lighthouse offers at the point of onboarding to the service partner and view details within the Azure Lighthouse Service Providers on the Azure Portal at any time. Once onboarded, the service partner operators can elevate to the privileged role for the agreed duration without any additional approvals from you. This enables the service partner to use a least-privileged approach to daily tasks, only raising their level to a role when needed to perform certain operations, while still maintaining visibility into all changes the service partner operator is performing on your scopes.
Announcing a new web experience for customers
Recently, the Azure Lighthouse product page on azure.com was redesigned to showcase the benefits of working with an Azure Lighthouse-enabled partner, including resources, videos, and customer testimonials for customers. To learn more, head to our Azure Lighthouse homepage and the Azure Lighthouse page for partners.
Azure Lighthouse was designed to enhance the professional services relationship between a service provider and a customer, maintaining transparency and customer control while reducing security exposures. If you have any feedback on this capability, the product group would love to hear from you via the Azure Lighthouse Product feedback channel or email us on azurelighthouse@microsoft.com.
Take control of your Azure estate. Ask for Azure Lighthouse.
