Four operational practices Microsoft uses to secure the Azure platform
Posted on
4 min read
This is the fourth blog in a 4-part blog post series on how Microsoft Azure provides a secure foundation.
Microsoft provides you with a secure foundation to host your infrastructure and applications. In the last blog in this series on infrastructure security, I shared top customer concerns about high investment without clear ROI and challenges of retaining security experts. In this blog, I discuss how Microsoft Azure can help you gain security expertise without additional investment through our operational best practices and a global team of over 3,500 cybersecurity experts. Today, we are going to look at the different operational practices our security experts follow to help ensure your data is secure.
1. Secure deployment practices
The Security Development Lifecycle (SDL) is a collection of industry-recognized best practices that address the seven-phases of software development. It helps our developers build more secure software and meet security compliance requirements.
Our developers follow the SDL to ensure they are meeting core security principles throughout development, resolving security issues before their code is deployed, and adhering to the security standards used by all software developed for the Azure platform.
The SDL is a repeatable process that all software development teams within Azure use to help ensure that code is secure during and after deployment. This process has helped us drastically reduce the number of vulnerabilities in our code.
In addition, the SDL helps improve compliance by putting privacy and compliance at the beginning of the development processes. This forces developers to address challenges with encryption, data location, personally identifiable information (PII), logging, auditing, or other security issues before anything is deployed.
We also encourage you, as you develop your code in Azure, to follow the SDL to help ensure your code is secure and compliant.
2. Restricted and just-in-time administrator access and secure access workstations
In addition to securing your code, Azure operations and security professionals also work to protect your data from unauthorized access. This includes implementing controls that restrict unauthorized access from Microsoft personnel and contractors.
For a rare security issue where a Microsoft employee needs to access your Azure infrastructure or your data in solving the security issue, strong security controls, such as Customer Lockbox for Azure, help ensure you stay in control of your data and the Azure platform remains secure.
One of those controls is just-in-time administrative access. If Microsoft employees needs access to customer data to resolve an issue, they need to request permission from the customer.
If permission is granted, the ability to carry out the requested activities is limited to a short period of time. Everything the Microsoft employee does during this time is logged, recorded and made available for future audit. When the authorization period expires, the Microsoft employee no longer has administrative access. Just-in-time administrative access helps make sure that Azure infrastructure and security operations personnel access only what they need to access and for a predefined amount of time.
In addition to just-in-time administrative access, another control used is the Secure Access Workstation (SAW). All Azure infrastructure and security operators are required to use a SAW when accessing the Azure infrastructure. The SAW is also used in those rare scenarios where a Microsoft employee needs access to customer data to resolve the security issue. These secure workstations are hardened and provide a safe environment from Internet-based attacks for sensitive tasks. These devices provide strong protection from phishing attacks, application and OS vulnerabilities, various impersonation attacks, or credential theft attacks that could put your data and systems at risk.
3. Fast and expert responses to threats
Microsoft Azure has a global security incident management team that detects and responds to a wide array of security threats 24/7/365.
The team follows a five-step incident response process that includes detect, assess, diagnose, stabilize, and close, when managing security incidents for the Azure platform.
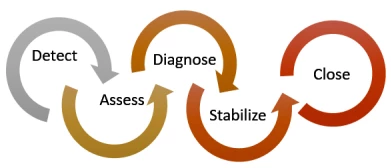
If Microsoft becomes aware that customer data has been accessed by an unauthorized party, the security incident manager will begin the execution of the Customer Security Incident Notification Process.
The goal of the customer security incident notification process is to provide impacted customers with accurate, actionable, and timely notice of when their customer data was potentially breached. The notices can also help you meet specific legal requirements.
In order to address security incidents quickly and accurately, the security incident response teams are required to complete technical security and security-awareness training. The technical training is focused on technical software issues that could create a security issue and how to avoid those problems. The security-awareness training is focused on teaching security response professionals how to avoid social and behavioral exploits such as phishing.
4. Cyber security experts
Microsoft has more than 3,500 cybersecurity experts that work across teams such as the Cyber Defense Operations Center (CDOC), the Microsoft Digital Criminal Response Center (MDCU) and the Microsoft Security Response Center (MSRC). These security experts act as human intelligence while working with sophisticated, automated processes to detect, respond, and remediate threats.
The CDOC brings together security response experts across Microsoft to help protect, detect, and respond to security threats against our infrastructure and services 24/7/365. Informed by trillions of data points across an extensive network of sensors, devices, authentication events, and communications, this team employs automated software, machine learning, behavioral analysis, and forensic techniques to create an Intelligent Security Graph. This graph enables us to interpret and act on possible security issues that would have been impossible prior to these advanced technologies.
The Microsoft Digital Crimes Unit (DCU) fights global malware and reduces digital risk for people all over the world. Our international team of attorneys, investigators, data scientists, engineers, analysts, and business professionals based in 30 countries continuously work together to fight digital crime and help secure your data and applications in Azure. To do this, this team combines big data analytics, cutting-edge forensics, and legal strategies to protect your data and keep you in control of your personal information.
The MSRC focuses on preventing harm, delivering protection from attacks, and building trust. This team has been engaged with security researchers for more than 20 years to protect customers and the broader partner ecosystem from being harmed from security vulnerabilities, and rapidly repulsing any attack against Microsoft Cloud.
From the development of software to the thousands of security experts on staff, Microsoft uses a variety of controls to protect your data in Azure.
To see some of the security teams that work on your behalf in action, watch our latest Microsoft Mechanics video. Start building your infrastructure and applications on the secure foundation Microsoft provides today for free.