This blog has been co-authored by Eliran Azulai, Principal Program Manager.
With the accelerated pace of digital transformation since the COVID-19 pandemic breakthrough, organizations continuously look to migrate their workloads to the cloud and to ensure their workloads are secure. Moreover, organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the hybrid workplace, and protects applications and data regardless of where they are.
Microsoft’s Zero Trust Framework protects assets anywhere by adhering to three principles:
- Verify explicitly: Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least privileged access: Limit user access with just-in-time and just-enough-access (JIT and JEA), risk-based adaptive policies, and data protection to help secure both data and productivity.
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
In this blog, we will describe some Azure network security services that help organizations to address Zero Trust, focusing on the third principle—assume breach.
Network firewalling
Network firewalls are typically deployed at the edge networks, filtering traffic between trusted and untrusted zones. The Zero Trust approach extends this model and recommends filtering traffic between internal networks, hosts, and applications.
The Zero Trust approach assumes breach and accepts the reality that bad actors are everywhere. Rather than building a wall between trusted and untrusted zones, it recommends we verify all access attempts, limit user access to JIT and JEA, and harden the resources themselves. However, this doesn’t preclude us from maintaining security zones. In fact, network firewalling provides a type of checks and balances for network communications, by segmenting the network into smaller zones and controlling what traffic is allowed to flow between them. This security-in-depth practice forces us to consider whether a particular connection should cross a sensitive boundary.
Where should firewalling take place in Zero Trust networks? Since your network is vulnerable by nature, one should implement firewalling at the host level and outside of it. In Azure, we provide filtering and firewalling services that are deployed at different network locations: at the host and between virtual networks or subnets. Let’s discuss how Azure’s firewalling services support Zero Trust.
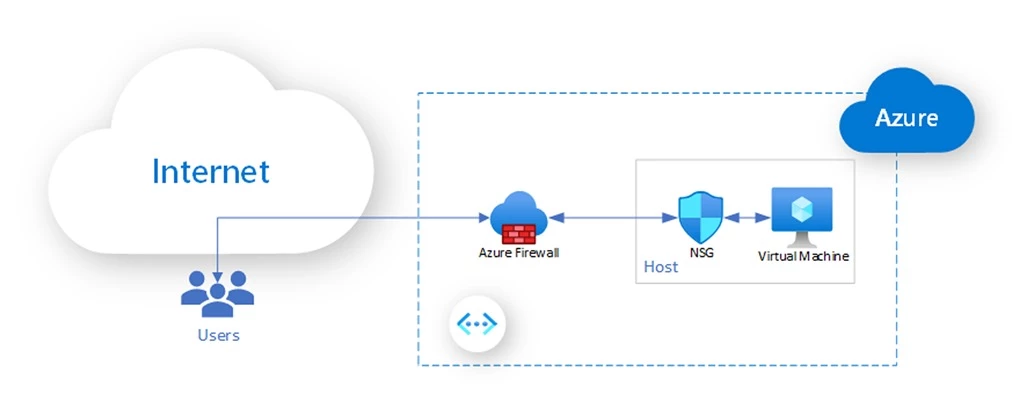
Azure network security group (NSG)
You can use Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. NSG is implemented at the host level, outside of the virtual machines (VMs). In terms of user configuration, NSG can be associated with a subnet or VM NIC. Associating an NSG with a subnet is a form of perimeter filtering that we’ll discuss later. The more relevant application of NSG in the context of Zero Trust networks is associated with a specific VM (such as by means of assigning an NSG to a VM NIC). It supports filtering policy per VM, making the VM a participant in its own security. It serves the goal of ensuring that every VM filters its own network traffic, rather than delegating all firewalling to a centralized firewall.
While host firewalling can be implemented at the guest OS level, Azure NSG safeguards against a VM that becomes compromised. An attacker who gains access to the VM and elevates its privilege could remove the on-host firewall. NSG is implemented outside of the VM, isolating host-level filtering, which provides strong guarantees against attacks on the firewalling system.
Inbound and outbound filtering
NSG provides for both inbound filtering (regulate traffic entering a VM) and outbound filtering (regulate traffic leaving a VM). Outbound filtering, especially between resources in the vnet has an important role in Zero Trust networks to further harden the workloads. For example, a misconfiguration in inbound NSG rules can result in a loss of this important inbound filtering layer of defense that is very difficult to discover. Pervasive NSG outbound filtering protects subnets even when such critical misconfiguration takes place.
Simplify NSG configuration with Azure application security groups
Azure application security groups (ASGs) simplify the configuration and management of NSGs, by configuring network security as an extension of an application’s structure. ASGs allow you to group VMs and define network security policies based on these groups. Using ASGs you can reuse network security at scale without manual maintenance of explicit IP addresses. In the simplified example below, we apply an NSG1 on a subnet level and associate two VMs with a WebASG (web application tier ASG), and another VM with a LogicASG (business logic application tier ASG).
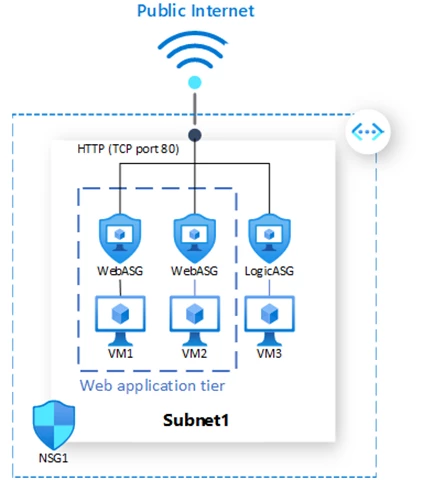
We can apply security rules to ASGs instead of each of the VMs individually. For example, the below rule allows HTTP traffic from the Internet (TCP port 80) to VM1 and VM2 in the web application tier, by specifying WebASG as the destination, instead of creating a separate rule for each VM.
|
Priority |
Source |
Source ports |
Destination |
Destination ports |
Protocol |
Access |
|
100 |
Internet |
* |
WebASG |
80 |
TCP |
Allow |
Azure Firewall
While host-level filtering is ideal in creating micro perimeters, firewalling at the virtual network or subnet level adds another important layer of protection. It protects as much infrastructure as possible against unauthorized traffic and potential attacks from the internet. It also serves to protect east-west traffic to minimize blast radius in case of attacks.
Azure Firewall is a native network security service for firewalling. Implemented alongside NSG, these two services provide important checks and balances in Zero Trust networks. Azure Firewall implements global rules and coarse-grained host policy while NSG sets fine-grained policy. This separation of perimeter versus host filtering can simplify the administration of the firewalling policy.
Zero Trust model best practice is to always encrypt data in transit to achieve end-to-end encryption. However, from an operational perspective, customers would often wish to have visibility into their data as well as to apply additional security services on the unencrypted data.
Azure Firewall Premium with its transport layer security (TLS) inspection can perform full decryption and encryption of the traffic, giving the ability to utilize intrusion detection and prevention systems (IDPS), as well as providing customers with visibility into the data itself.
DDoS Protection
Zero Trust strives to authenticate and authorize just about everything on the network, but it does not provide good mitigation against DDoS attacks, particularly against volumetric attacks. Any system that can receive packets is vulnerable to DDoS attacks, even those employing a Zero Trust architecture. Consequently, it’s imperative that any Zero Trust implementation is fully protected against DDoS attacks.
Azure DDoS Protection Standard provides DDoS mitigation features to defend against DDoS attacks. It is automatically tuned to help protect any internet-facing resource in a virtual network. Protection is simple to enable on any new or existing virtual network and requires no application or resources changes.
Optimize SecOps with Azure Firewall Manager
Azure Firewall Manager is a security management service that provides central security policy and route management for cloud-based security perimeters.
In addition to Azure Firewall policy management, Azure Firewall Manager now allows you to associate your virtual networks with a DDoS protection plan. Under a single-tenant, DDoS protection plans can be applied to virtual networks across multiple subscriptions. You can use the Virtual Networks dashboard to list all virtual networks that don’t have a DDoS Protection Plan and assign new or available protection plans to them.
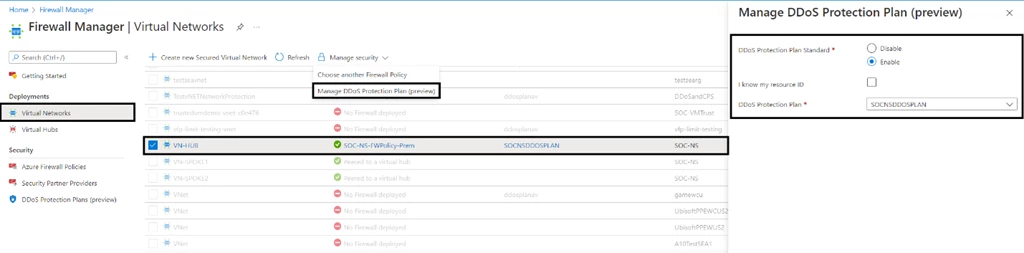
Moreover, Azure Firewall Manager allows you to use your familiar, best-of-breed, third-party security as a service (SECaaS) offerings to protect Internet access for your users.
By seamlessly integrating with Azure core security services, such as Microsoft Defender for Cloud, Microsoft Sentinel, and Azure Log Analytics, you can further optimize your SecOps with a one-stop-shop providing you best-of-breed networking security services, posture management, and workload protection—as well as SIEM and data analytics.
What’s next
Zero Trust is imperative for organizations working to protect everything as it is. It’s an ongoing journey for security professionals but getting started begins with some first steps and continuous iterative improvements. In this blog, we described several Azure security services and how they enable the Zero Trust journey for all organizations.
To learn more about these services, see the following resources:
