Microsoft has developed a new way to keep customers informed about security vulnerabilities that affect their Azure resources. When a vulnerability is disclosed that affects their resources, customers will be notified through Service Health in the Azure Portal. This Service Health message will include information about the vulnerability’s common vulnerabilities and exposures number (CVE), severity, and steps customers can take to safeguard against it. In most cases, it will also include a list of the specific resources in their subscription that customers need to take action on.
Our goal is to provide a more consistent and reliable experience for customers. Recent innovations in Azure Service Health now allow us to deliver communications with impacted resources and target messaging at tenant admins. With these new innovations, we can leverage existing work done by the Microsoft Security Response Center (MSRC) in vulnerability reporting to bring actionable information to customers that is tailored to their unique environment.
Below is an overview of how Microsoft discloses new vulnerabilities, where to find messages regarding CVEs in Azure Service Health, and how to understand the content in a Service Health message.
About vulnerabilities at Microsoft
Microsoft discloses a range of vulnerabilities every month across the spectrum of Microsoft product groups, including Windows, Microsoft 365, and Azure. When these vulnerabilities are publicly disclosed and require customer action, they are assigned a CVE number and published in the Security Update Guide by the Microsoft Security Response Center (MSRC).
Customers can learn more about how Microsoft collaborates with the security research community to identify and mitigate vulnerabilities in the Anatomy of a Cloud-Service Security Update blog from MSRC.
A CVE indicates that action is needed from customers in order to remain secure. Whenever a vulnerability is disclosed that affects an Azure product or service, the Azure communications team collaborates with MSRC and product engineering to ensure that vulnerable customers are notified of any actions they need to take to mitigate the vulnerability. Like communications regarding ongoing outages or upcoming maintenance, these notifications are published to Service Health in the Azure Portal.
Note that, even if we message customers regarding a CVE, this does not indicate any abuse, exploitation, or hacking has occurred. While vulnerabilities are common, these are often reported and fixed before any threat actor can exploit them or manipulate customer data.
Service Health messages for Azure CVEs
Where to find messages for Azure CVEs
Advisories for newly disclosed CVEs will appear under the Security advisories blade in Service Health in the Azure Portal. The title of these communications will typically lead with “[Action Required]” and include the CVE number. From here, customers can click the title of the message and drill down into the message contents.
We will only send communications to customers that either have resources that are vulnerable to the CVE or who otherwise need to take some sort of action to remediate. If a given CVE affects Azure App Service ASP.NET deployments, for example, you won’t receive a message if you don’t have any App Service resources or if your App Service resources only consist of Python web apps. On rare occasions, it may be more difficult for us to determine which specific resources are vulnerable to a given CVE. In such cases, we may send a CVE notification to an approximate set of customers. If we publish messaging to an approximate set of customers, we aim to include guidance that customers can follow to validate whether they have resources deployed that are vulnerable to the CVE.
How to read messages for Azure CVEs
Service Health messages for Azure CVEs typically consist of three parts:
- An overview of the CVE.
- A summary of the action required from customers.
- Links to additional support.
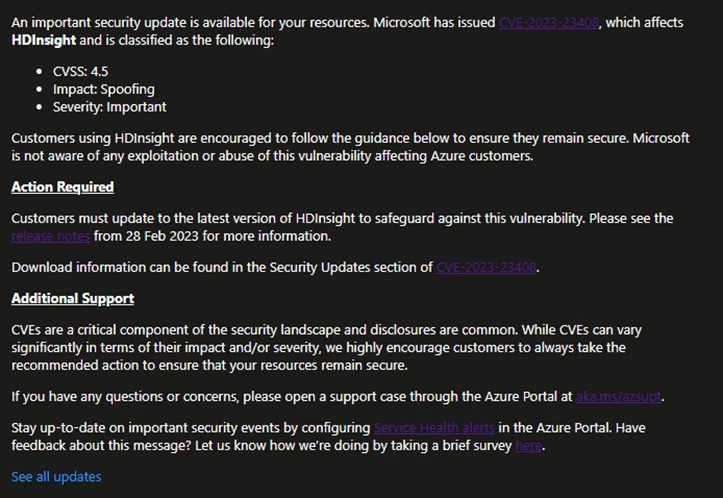
The opening portion of the message will give customers a high-level overview of the vulnerability, common vulnerability scoring system (CVSS) score, impact, and severity as outlined in the CVE itself. This section will also explain which Azure services or features are vulnerable to this CVE and include a link to the CVE in the Security Update Guide.
The Action Required section dives into the guidance for customers to safeguard against the specific vulnerability. In the Service Health message, we may provide a summarized version of the mitigation steps for quick reference, but customers are encouraged to refer to the Security Update Guide for links to the appropriate resources needed to mitigate, including documentation and update packages.
Lastly, the Additional Support section includes links to resources that customers can refer to in order to open a support case and configure alerting in Service Health. Customers who have questions regarding a CVE beyond the information provided in the Service Health message, or need further assistance in applying mitigation steps, are encouraged to open a support case through the Azure Portal.
We strive to provide the same level of detail from message to message, regardless of the perceived impact of the vulnerability. A CVSS 8.0 may mean something different for a customer hosting an e-commerce site on a virtual machine (VM) scale set than for a customer using one VM to host a Minecraft server as a sandbox for their friends. As such, our goal is to provide the necessary information for customers to make an informed decision about how to approach their security. We always encourage customers to follow the recommended guidance provided as soon as possible and follow security best practices.
Who can read Service Health messages regarding Azure CVEs?
In most cases, we will target a Service Health message regarding an Azure CVE to the specific subscriptions with resources identified as vulnerable or where customers need to take some action. Any user with reader privileges in the subscription will be able to navigate to Service Health and view the message.
On some occasions, we may target the message to particular tenants if the vulnerability impacts users at the tenant level. In such cases, only tenant admins, or roles with tenant admin access, will be able to view the message after toggling their view for tenant-level events. Communications for tenant-level events are only available in the new Azure Portal experience.
Impacted resources and Service Health alerts
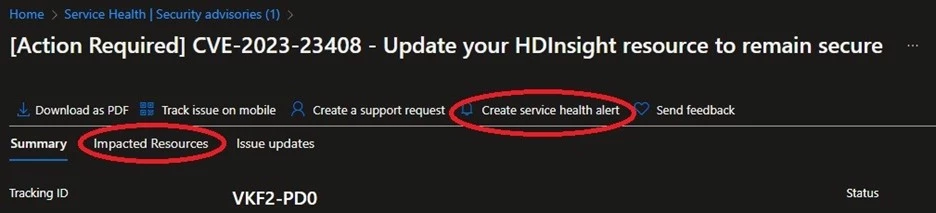
For those cases where we can identify specific resources that may be vulnerable to a given CVE, a new feature of Azure Service Health allows us to provide you with information about the resources in your subscription that may require action. Customers can view this information by clicking the “Impacted Resources” tab towards the top of the message next to the “Summary” tab. The resource information provided can range from a specific resource ID (including resource group and resource name) to the current runtime version and may vary depending on the nature of the vulnerability. For more information about the new Service Health experience, see our documentation about resource impact from Azure security incidents.
Additionally, customers can configure Service Health alerts for their Azure resources. Service Health alerts will notify you through your preferred notification channel such as SMS and email when your resources are affected by a platform event. These alerts can be configured for different types of events, from security events to outages to planned maintenance updates.
What about third-party CVEs that affect Microsoft products?
These cases are rare, but they do happen occasionally. There are two primary situations in which this would happen:
- When a non-Microsoft product contains a vulnerability, but that product is used as an underlying component of a Microsoft offering (ex. certain open-source software).
- When an offering from an Independent Software Vendor (ISV) sold on the Azure Marketplace contains a vulnerability.
In such cases, Microsoft would not release the CVE, but rather the disclosure of the CVE would be done by the 3rd party that owns the vulnerable software. Regardless, Microsoft may publish our own messaging regarding 3rd party CVEs to Azure Service Health.
If a 3rd party CVE has a downstream impact on a Microsoft product or service, we may publish messaging to affected customers to raise awareness and inform them of any action they need to take.
If a CVE is disclosed that affects an offering on the Azure Marketplace, Microsoft may message customers using that offering at the request of the ISV or if we determine there is some imminent risk to our customers. In general, for CVEs affecting offerings on the Azure Marketplace, customers are encouraged to work with the relevant ISV for questions regarding the security of their offering.
Stay updated on security events
To summarize, these are the key things to keep in mind regarding how Microsoft keeps customers informed about vulnerabilities affecting Azure Services:
- Customers identified as vulnerable to a given CVE will be notified through Service Health in the Azure Portal.
- In some cases, we may not be able to identify a precise set of affected customers. In such cases, we may target an approximate set of customers with messaging.
- We aim to include information about the specific resources in a customer’s subscription that may be vulnerable and need to be updated.
- If we are unable to provide information about specific affected resources, we will provide steps that customers can follow to check for vulnerable resources within their subscription.
- Disclosure of a CVE, or receipt of a message in Service Health regarding a CVE, doesn’t entail that any abuse or exploitation has taken place.
- The Security Update Guide from MSRC is where new vulnerabilities are disclosed by Microsoft. CVEs in the Security Update Guide typically include information about its exploitability and links to the necessary security updates to remain safeguarded against it.
Customers are highly encouraged to configure Service Health alerts to be notified when a platform event affects their Azure resources. You can receive alerts through your preferred channel, including SMS, email, and webhook. Microsoft values our ongoing collaboration with the security research community to identify vulnerabilities in our products and services. We encourage all researchers to work with vendors under Coordinated Vulnerability Disclosure (CVD) and abide by the rules of engagement for penetration testing to avoid impacting customer data while conducting security research.
