When someone mentions the words “Internet of Things,” often the first picture that comes to mind is some sort of device with the Internet “built-in.” However, a built-in design involves months or years of design work and applies only to devices that have yet to come to market. How do businesses leverage IoT for the billions of devices already in the field without creating a large security risk? Within the Azure Sphere team, we have a term for those scenarios that is called “brownfield” deployments. Josh Nash, our product planner, is guest blogging today to tell you more about brownfield IoT and how Azure Sphere can safely connect devices already deployed in the field.
Happy reading!
– Ed Nightingale
As a product planner, I have spent thousands of hours meeting with partners and customers to understand their needs to ensure that our product is not only secured, but also practical and useful. Our first focus is often on new devices, which are devices that have Azure Sphere deeply integrated into the product platform. We refer to these devices as “greenfield” scenarios. These scenarios shine as Azure Sphere’s value proposition resonates soundly, and the implementation is comparatively more straightforward due to the flexibility before a design is considered final. OEMs can focus on how to integrate Azure Sphere within a device’s internal design to meet power, performance, and functionality goals. Devices already in service without connectivity represent a “brownfield” opportunity to create meaningful, new connected experiences across a wide range of equipment. This blog post outlines the challenges of these brownfield devices and how Azure Sphere can help.
The problem
The act of connecting enterprise equipment represents an opportunity to enable markedly better outcomes by enabling scenarios and innovative business models for the enterprise such as preventive maintenance, just-in-time reporting, and even role-based access to equipment and data. But there are millions of devices in enterprises around the world that were either put into service before connectivity for non-IT devices was considered feasible or were intentionally not connected because they were deemed too mission critical to be subjected to the unsafe world of the Internet.
While connecting these unconnected devices creates positive outcomes and opportunities for the enterprise, in either case, there are risks associated with connecting these devices. Whether the devices predated connectivity or were deemed too important to connect, the outcome is the same – their lack of connectedness is their security model, a concept known as air-gap security. However, as capabilities improve to solve optimization and other resourcing decisions with the cloud, the value of connectedness increases. At the same time, the risk of connecting air-gap devices is at least as high as before. Businesses need a mechanism to balance the equation, mitigating risk by infusing a new security model into the system design. As the value of connectedness increases, enterprises need a mechanism to securely connect these devices that are already in service.
Securing existing equipment and devices with a guardian module
Microsoft announced Azure Sphere at RSA last year to enable secure, connected, microcontroller- (MCU-) based devices. Azure Sphere unlocks IoT by establishing a foundation on which an enterprise can trust a device to run securely in any environment. Based on the Microsoft whitepaper, “The 7 Properties of Highly Secure Devices,” Azure Sphere delivers device security by combining hardware, operating system software, and cloud services that has been purpose-built for secure IoT applications. Azure Sphere is raising the bar for manufacturers and enterprises to enable secure connectivity in new devices by delivering the seven properties, but it can do more.
Azure Sphere can also deliver secured connectivity to established devices already in service. By utilizing existing ports on an unconnected device, Azure Sphere can be built into a “guardian module” that can be paired with existing equipment to enable secured connectivity that rebalances the opportunity versus risk debate in favor of device connectivity. The key to security in these scenarios is that Azure Sphere, not the device, communicates with the cloud. By separating the device from the network, a guardian module enabled by Azure Sphere can protect the equipment from attack, ensure data is only transmitted between trusted cloud and device communications partners, and ensure the software of the module and the equipment remains intact and secured.
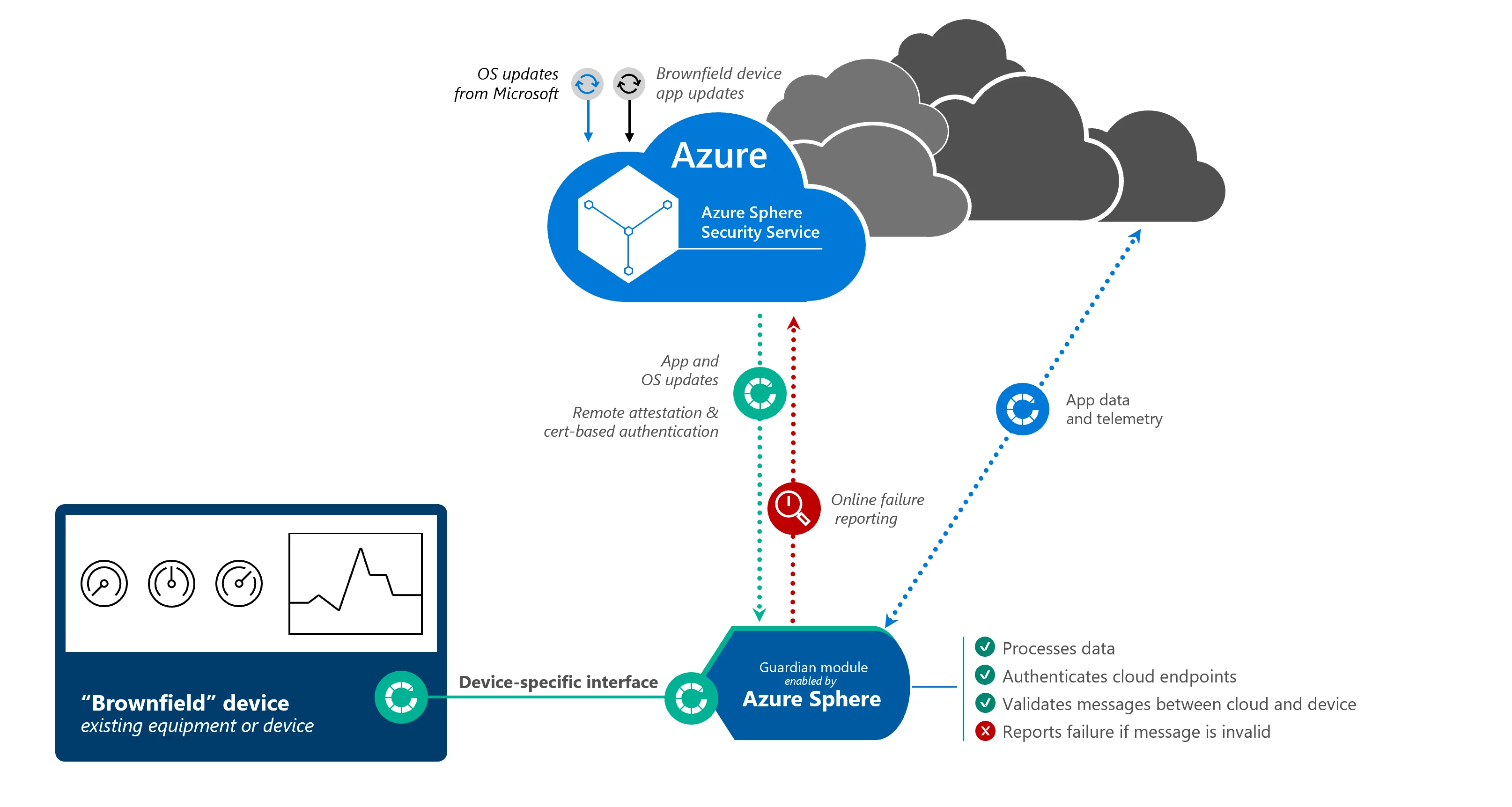
With Azure Sphere in a guardian module, enterprises can enable a variety of secured operations between the device and the cloud. From a device health and security perspective, the device can utilize the Azure Sphere Security Service for certificate-based authentication, failure reporting, and over-the-air software updates. When a guardian module passes authentication, it receives a certificate signed by the Azure Sphere Security Service that can be used to identify the device as genuine in communicating with cloud services. These communications between the guardian module and the cloud could comprise of data coming off the device to signal events or inform decision-making, and they could also represent messages from the cloud to trigger activity from the device itself.
In both directions, applications running on Azure Sphere can be used to validate that messages are properly formed before they are passed to or from the brownfield device and Azure Sphere ensures that the guardian module can only communicate with trusted endpoints. The Azure Sphere Security Service can also be used as a distribution point for software updates not only to the Azure Sphere OS and guardian module manufacturer’s device software, but also for updates to the downstream, previously unconnected device’s software. In this situation, the enterprise can avoid costly truck rolls to update software on their equipment. With a guardian module enabled by Azure Sphere, these brownfield devices can reap most of the benefits of a device that integrated Azure Sphere into its design.
With an Azure Sphere-enabled device, enterprise customers can more confidently connect existing devices to the cloud and unlock scenarios related to preventive maintenance, optimizing utilization, and even role-based access control. Our partner, Avnet, has already designed and built guardian modules that use Azure Sphere, and others are expected in the near future. When linking a multitude of devices together in the cloud, the possibilities are almost endless.
To start the discussion on how Azure Sphere can help your business, please contact us.
