Almost two years ago, the National Defense Science Board invited me to participate in the Summer Study 2020 Panel, “Protecting the Global Information Infrastructure.” They requested that I brief them on the evolution of the global communications infrastructure connecting all nations. The U.S., like other nations, both cooperates and competes in the commercial telecom market, while prioritizing national security.
This study group was interested in the implementation of 5G and its evolution to 6G. They understood that softwarization of the core communication technologies and the inclusion of edge and cloud computing as core infrastructure components of telecommunications services is inevitable. Because of my expertise in these areas, they invited me to share my thoughts on how we might secure and protect the emerging networks and systems of the future. I prepared for the meeting by looking at how Microsoft, as a major cloud vendor, had worked to secure our global networks.
My conclusion was simple. It is clear that attacks on the national communications infrastructure will occur with much greater sophistication than ever before. Because of this, we continue to develop our networks and systems with security as our first principle and we stay constantly vigilant. To these ends, Microsoft has adopted a zero-trust security architecture in all our platforms, services, and network functions.
Specialized hardware replaced by disaggregated software
One challenge for the panel was to understand precisely what the emerging connectivity infrastructure will be, and what security attributes must be assured with respect to that infrastructure.
Classical networks (the ones before the recent 5G networks), were deployed as hub-and-spoke architecture. Packets came to a specialized hardware-software package developed by a single vendor. From there, they were sent to the Internet. But 5G (and beyond) networks are different. In many ways, the specialized hardware has been “busted open.”
Functionality is now disaggregated into multi-vendor software components that run on different interconnected servers. As a result, the attack surface area has increased dramatically. Network architects have to protect each of these components along their interconnects—both independently and together. Furthermore, packets are now processed by multiple servers, any of which could be compromised. 5G brings the promise of a significant number of connected Internet-of-Things (IoT) devices that, once compromised, could also be turned into an army of attackers.
The power of cloud lies in its scale
In a word, Microsoft Azure is big: 62 regions in 140 countries worldwide host millions of networked servers, with regions connected by over 180,000 miles of fiber. Some of our brightest and most experienced engineers have used their knowledge to make this infrastructure safe and secure for customers, which includes companies and people working in healthcare, government services, finance, energy, manufacturing, retail, and more.
As of today, Microsoft tracks more than 250 unique nation-states, cybercriminals, and other threat actors. Our cloud processes and analyzes more than 43 trillion security signals every single day. Nearly 600,000 organizations worldwide use our security offering. With all this, Microsoft’s infrastructure is secure, and we have earned the trust of our customers. Many of the world’s largest companies with vital and complex security needs have offloaded much of their network and compute workloads to Azure. Microsoft Azure has become part of their critical infrastructure.
Securing Open RAN architecture
The cloud’s massive and unprecedented scale is unique, and precisely what makes the large investments in sophisticated defense and security economically possible. Microsoft Azure’s ground-up design includes strict security measures to withstand any type of attack imaginable. Conversely, the scale required to defend against sophisticated threats is not logical or feasible for smaller-scale, on-premises systems.
The report, “Why 5G requires new approaches to cybersecurity”1 articulates several good reasons why we need to think about how to protect our infrastructure. Many of us in research and engineering have also been thinking about these issues, as evidenced by Microsoft’s recently published white paper, Bringing Cloud Security to the Open RAN, which describes how we can defend and mitigate against malicious attacks against O-RANs, beginning with security as the first principle.
With respect to O-RAN and Azure for Operators Distributed Services (AODS), we explain how they inherit and benefit from the cloud’s robust security principles applied in the development of the far-edge and the near-edge. The inherently modular nature of Open RAN, alongside recent advancements in Software Defined Networking (SDN) and network functions virtualization (NFV), enables Microsoft to deploy security capabilities and features at scale across the O-RAN ecosystem.
We encapsulate code into secure containers and enable more granular control of sensitive data and workloads than prior generations of networking technologies. Additionally, our computing framework makes it easy to add sophisticated security features in real-time, including AI/ML and advanced cloud security capabilities to promptly detect and actively mitigate malicious activities.
Microsoft is actively working on delivering the most resilient platform in the industry, backed by our proven security capabilities, trustworthy guarantees, and a well-established secure development lifecycle. This platform is being integrated with Microsoft security defense services to prevent, detect, and respond to attacks. It includes AI/ML technologies to allow creation of logic to automate and create actionable intelligence to improve security, fault analyses, and operational efficiency.
We are also leveraging Azure services such as Active Directory, Azure Container Registry, Azure Arc, and Azure Network Function Manager to provide a foundation for secure and verifiable deployment of RAN components. Additional technologies include secure RAN deployment and management processes on top of these, which will eliminate significant upfront cost otherwise incurred by RAN vendors when building these technologies themselves.
It is noteworthy that across the entire project lifecycle—from planning to sunsetting—we integrate security practices. All software deliverables are developed in a “secure by default” manner, going through a pipeline that leverages Microsoft Azure’s security analysis tools that perform static analysis, credential scanning, regression, and functionality testing.
We are taking steps to integrate our RAN analytics engine with Microsoft Sentinel. This enables telecom operators to manage vulnerability and security issues, and to deploy secure capabilities for their data and assets. We expect Microsoft Sentinel, Azure Monitor, and other Azure services will incorporate our RAN analytics to support telecommunications customers. With this, we will deliver intelligent security analytics and threat intelligence for alert detection, threat visibility, proactive hunting, and threat response. We also expect that Azure AI Gallery will host sophisticated 3rd party ML models for RAN optimization and threat detection, running on the data streams we collect.
Mitigating the impact of compromised systems
We have built many great tools to keep the “bad guys” out, but building secure telecommunication platforms requires dealing with the unfortunate reality that sometimes systems can still be compromised. As a result, we are aggressively conducting research and building technologies, including fast detection and recovery from compromised systems.
Take the case of ransomware. Traditional ransomware attacks encrypt a victim’s data and ask for a ransom in exchange for decrypting it. However, modern ransomware attacks do not limit themselves to encrypting data. Instead, they remove the enterprise’s ability to control its platforms and critical infrastructure. The RAN constitutes critical infrastructure and can suffer from ransomware attacks.
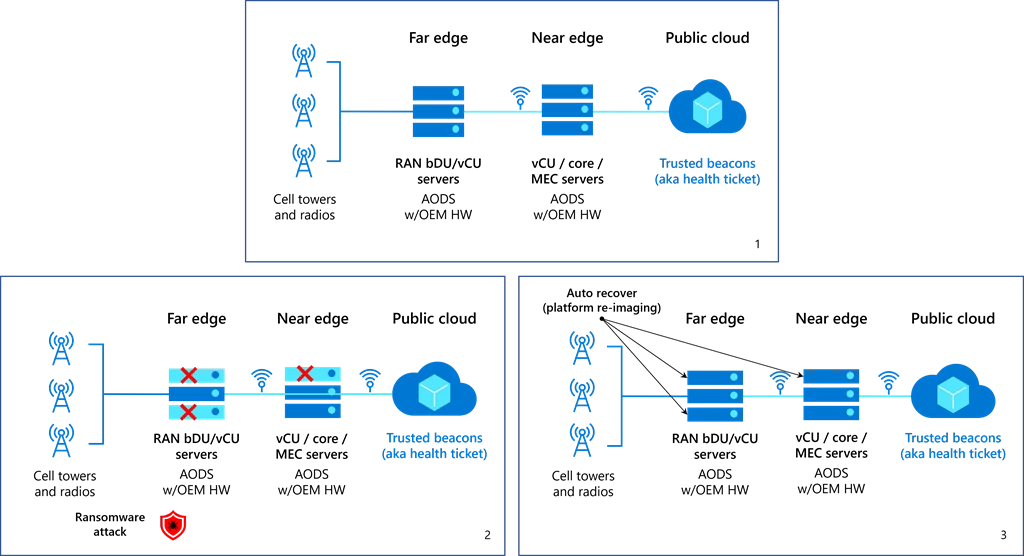
Specifically, we have developed technology that prepares us for the unfortunate time when systems may be compromised. Our latest technology makes it easier to recover as quickly as possible, and with minimal manual effort. This is especially important in telco far-edge scenarios, where the large number of sites makes it prohibitively expensive to send technicians into the field for recovery. Our solution, which leverages a concept called trusted beacons, automatically recovers a far-edge node from a compromise or failure. When trusted beacons are absent, the platform automatically reboots and re-installs an original, unmodified, and uncompromised software image.
Looking into the future
We have developed mechanisms for monitoring and analyzing data as we look for threats. Our best-in-class verification technology checks every configuration before lighting it up. Our researchers are constantly adding new AI techniques that use the compute power of the cloud to protect our infrastructure better than ever before. Our end-to-end zero-trust solutions spanning identity, security, compliance, and device management, across cloud, edge, and all connected platforms will protect the telecommunications infrastructure. We continue to invest billions to improve cybersecurity outcomes.
Microsoft will continue to update you on developments that impact the security of our network, including many of the technologies noted within this article. Microsoft knows that while we need to continue to be vigilant, the telecommunications industry ultimately benefits by making Microsoft Azure part of their critical infrastructure.
1 Tom Wheeler and David Simpson, “Why 5G requires new approaches to cybersecurity.” The Brookings Institution.
