Microsoft spends one billion dollars per year on cybersecurity and much of that goes to making Microsoft Azure the most trusted cloud platform. From strict physical datacenter security, ensuring data privacy, encrypting data at rest and in transit, novel uses of machine learning for threat detection, and the use of stringent operational software development lifecycle controls, Azure represents the cutting edge of cloud security and privacy.
Today, I’m excited to announce that Microsoft Azure is the first cloud to offer new data security capabilities with a collection of features and services called Azure confidential computing. Put simply, confidential computing offers a protection that to date has been missing from public clouds, encryption of data while in use. This means that data can be processed in the cloud with the assurance that it is always under customer control. The Azure team, along with Microsoft Research, Intel, Windows, and our Developer Tools group, have been working on confidential computing software and hardware technologies for over four years. The bottom of this post includes a list of Microsoft Research papers related to confidential computing. Today we take that cutting edge one step further by now making it available to customers via an Early Access program.
Data breaches are virtually daily news events, with attackers gaining access to personally identifiable information (PII), financial data, and corporate intellectual property. While many breaches are the result of poorly configured access control, most can be traced to data that is accessed while in use, either through administrative accounts, or by leveraging compromised keys to access encrypted data. Despite advanced cybersecurity controls and mitigations, some customers are reluctant to move their most sensitive data to the cloud for fear of attacks against their data when it is in-use. With confidential computing, they can move the data to Azure knowing that it is safe not only at rest, but also in use from the following threats:
- Malicious insiders with administrative privilege or direct access to hardware on which it is being processed
- Hackers and malware that exploit bugs in the operating system, application, or hypervisor
- Third parties accessing it without their consent
Confidential computing ensures that when data is “in the clear,” which is required for efficient processing, the data is protected inside a Trusted Execution Environment (TEE – also known as an enclave), an example of which is shown in the figure below. TEEs ensure there is no way to view data or the operations inside from the outside, even with a debugger. They even ensure that only authorized code is permitted to access data. If the code is altered or tampered, the operations are denied and the environment disabled. The TEE enforces these protections throughout the execution of code within it.
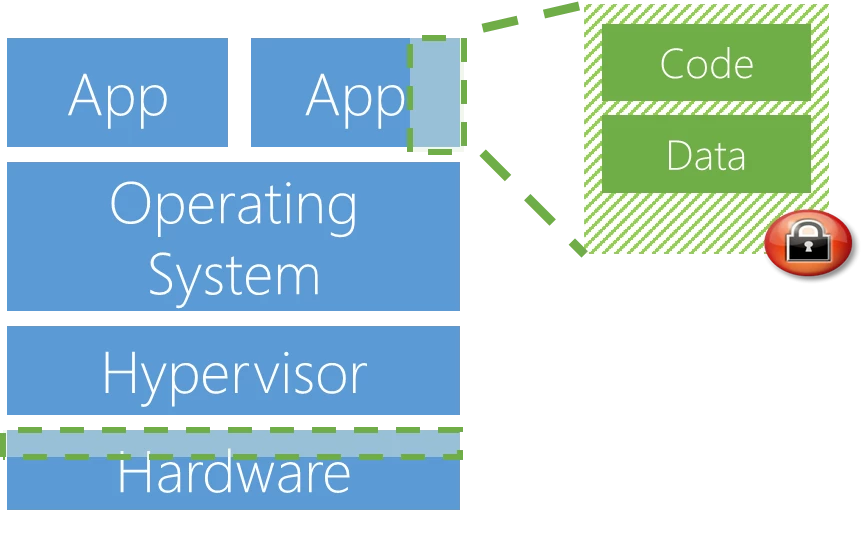
With Azure confidential computing, we’re developing a platform that enable developers to take advantage of different TEEs without having to change their code. Initially we support two TEEs, Virtual Secure Mode and Intel SGX. Virtual Secure Mode (VSM) is a software-based TEE that’s implemented by Hyper-V in Windows 10 and Windows Server 2016. Hyper-V prevents administrator code running on the computer or server, as well as local administrators and cloud service administrators from viewing the contents of the VSM enclave or modifying its execution. We’re also offering hardware-based Intel SGX TEE with the first SGX-capable servers in the public cloud. Customers that want their trust model to not include Azure or Microsoft at all can leverage SGX TEEs. We’re working with Intel and other hardware and software partners to develop additional TEEs and will support them as they become available.
Microsoft already uses enclaves to protect everything from blockchain financial operations, to data stored in SQL Server, and our own infrastructure within Azure. While we’ve previously spoken about our confidential computing blockchain efforts, known as the Coco Framework, today we are announcing the use of the same technology to implement encryption-in-use for Azure SQL Database and SQL Server. This is an enhancement of our Always Encrypted capability, which ensures that sensitive data within a SQL database can be encrypted at all times without compromising the functionality of SQL queries. Always Encrypted achieves this by delegating computations on sensitive data to an enclave, where the data is safely decrypted and processed. We continue to use enclaves inside Microsoft products and services to ensure that wherever sensitive information needs to be processed, it can be secured while in use.
In addition to SQL Server, we see broad application of Azure confidential computing across many industries including finance, healthcare, AI, and beyond. In finance, for example, personal portfolio data and wealth management strategies would no longer be visible outside of a TEE. Healthcare organizations can collaborate by sharing their private patient data, like genomic sequences, to gain deeper insights from machine learning across multiple data sets without risk of data being leaked to other organizations. In oil and gas, and IoT scenarios, sensitive seismic data that represents the core intellectual property of a corporation can be moved to the cloud for processing, but with the protections of encrypted-in-use technology.
Customers can try out Azure confidential computing through our Early Access program, which includes access to Azure VSM and SGX-enabled virtual machines, as well as tools, SDKs, and Windows and Linux support to enable any application in the cloud to protect its data while in use.
Sign up for the Azure confidential computing Early Access program.
I look forward to seeing you at Ignite, where I’ll demonstrate enclaves in Azure. There’s so many opportunities and use cases we can secure together using the Azure cloud, Intel hardware, along with Microsoft technologies, services, and products.
Today is the exciting beginning of a new era of secure computing. Join us in Azure as we create this future.
– Mark
See how confidential computing fits within Microsoft’s broader cloud security strategy in the Microsoft Story Labs feature: Securing the Cloud.
