Network security solutions can be delivered as appliances on premises, as network virtual appliances (NVAs) that run in the cloud or as a cloud native offering (known as firewall-as-a-service).
Customers often ask us how Azure Firewall is different from Network Virtual Appliances, whether it can coexist with these solutions, where it excels, what’s missing, and the TCO benefits expected. We answer these questions in this blog post.
Network virtual appliances (NVAs)
Third party networking offerings play a critical role in Azure, allowing you to use brands and solutions you already know, trust and have skills to manage. Most third-party networking offerings are delivered as NVAs today and provide a diverse set of capabilities such as firewalls, WAN optimizers, application delivery controllers, routers, load balancers, proxies, and more. These third party capabilities enable many hybrid solutions and are generally available through the Azure Marketplace. For best practices to consider before deploying a NVA, see Best practices to consider before deploying a network virtual appliance.
Cloud native network security
A cloud native network security service (known as firewall-as-a-service) is highly available by design. It auto scales with usage, and you pay as you use it. Support is included at some level, and it has a published and committed SLA. It fits into DevOps model for deployment and uses cloud native monitoring tools.
What is Azure Firewall?
Azure Firewall is a cloud native network security service. It offers fully stateful network and application level traffic filtering for VNet resources, with built-in high availability and cloud scalability delivered as a service. You can protect your VNets by filtering outbound, inbound, spoke-to-spoke, VPN, and ExpressRoute traffic. Connectivity policy enforcement is supported across multiple VNets and Azure subscriptions. You can use Azure Monitor to centrally log all events. You can archive the logs to a storage account, stream events to your Event Hub, or send them to Log Analytics or your security information and event management (SIEM) product of your choice.
Is Azure Firewall a good fit for your organization security architecture?
Organizations have diverse security needs. In certain cases, even the same organization may have different security requirements for different environments. As mentioned above, third party offerings play a critical role in Azure. Today, most next-generation firewalls are offered as Network Virtual Appliances (NVA) and they provide a richer next-generation firewall feature set which is a must-have for specific environments/organizations. In the future, we intend to enable chaining scenarios to allow you to use Azure Firewall for specific traffic types, with an option to send all or some traffic to a third party offering for further inspection. This third-party offering can be either a NVA or a cloud native solution.
Many Azure customers find the Azure Firewall feature set is a good fit and it provides some key advantages as a cloud native managed service:
- DevOps integration – easily deployed using Azure Portal, Templates, PowerShell, CLI, or REST.
- Built in HA with cloud scale.
- Zero maintenance service model – no updates or upgrades.
- Azure specialization— for example, service tags, and FQDN tags.
- Significant total cost of ownership saving for most customers.
But for some customers third party solutions are a better fit.
The following table provides a high-level feature comparison for Azure Firewall vs. NVAs:
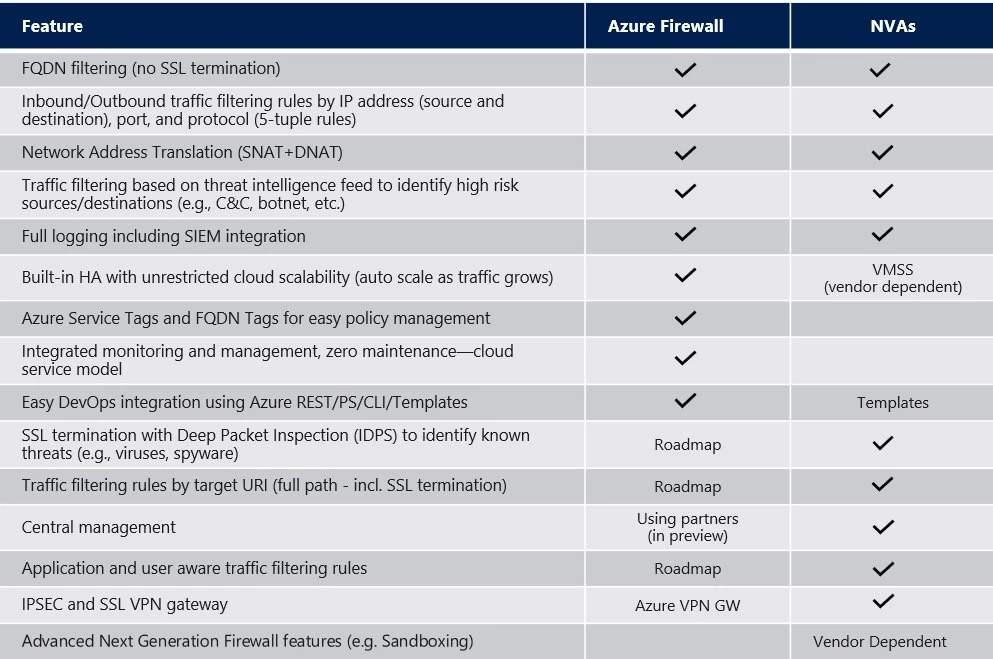
Figure 1: Azure Firewall versus Network Virtual Appliances – Feature comparison
Why Azure Firewall is cost effective
Azure Firewall pricing includes a fixed hourly cost ($1.25/firewall/hour) and a variable per GB processed cost to support auto scaling. Based on our observation, most customers save 30 percent – 50 percent in comparison to an NVA deployment model. We are announcing a price reduction, effective May 1, 2019, for the firewall per GB cost to $0.016/GB (-46.6 percent) to ensure that high throughput customers maintain cost effectiveness. There is no change to the fixed hourly cost. For the most up-to-date pricing information, please go to the Azure Firewall pricing page.
The following table provides a conceptual TCO view for a NVA with full HA (active/active) deployment:
|
Cost |
Azure Firewall |
NVAs |
Compute | $1.25/firewall/hour $0.016/GB processed (30%-50% cost saving) | Two plus VMs to meet peak requirements |
Licensing | Per NVA vendor billing model | |
Standard Public Load Balancer | First five rules: $0.025/hour | |
Standard Internal Load Balancer | First five rules: $0.025/hour | |
Ongoing/Maintenance | Included | Customer responsibility |
Support | Included in your Azure Support plan | Per NVA vendor billing model |
Figure 2: Azure Firewall versus Network Virtual Appliances – Cost comparison
Next steps
- Azure Firewall Documentation
- March blog: Announcing new capabilities in Azure Firewall
- Pricing
- Azure Firewall management partners:
