Is your business ready for the holiday season?
As we approach the holiday season and bring in thoughts of good cheers, many companies are faced with an elevated risk of cyber-attacks. What makes the holidays such an enticing time for hackers is the combination of an increase in traffic volume due to an uptick in eCommerce that helps disguise hackers from detection, and reduced staff. All of which makes this time of year too attractive for cyber-criminals to pass up.
In fact, security firms report a 150 percent increase in DDoS attacks in the months between summer and the end of the year. DDoS is becoming an unfortunate and inevitable addition to the holidays.
DDoS is an ever-growing problem, and the types of attacks are getting increasingly sophisticated. More importantly, DDoS attacks are often used as a “smokescreen,” masking more malicious and harmful infiltration of your resources. The technology to create DDoS attacks continues to increase in sophistication while the cost and ability to instigate these attacks get more and more accessible. Therefore, driving up the frequency and ease at which criminals can wreak havoc on businesses and users.
Readily available DDoS toolkits, botnet-for-hire services and an explosion of inadequately secured IoT devices, make every organization a potential target. No online network, application, service, or website is immune to the DDoS threat.
Azure offers solutions to protect your valuable digital assets from these cyber-attacks during the holidays and throughout the year. Azure DDoS Protection provides countermeasures against the most sophisticated DDoS threats. The service provides enhanced DDoS mitigation capabilities for your application and resources deployed in your virtual networks. Additionally, customers using Azure DDoS Protection has access to DDoS Rapid Response support to engage DDoS experts during an active attack. You can easily enable DDoS Protection for your resources to proactively protect against DDoS attacks!
Protect your applications against DDoS attacks in three steps:
1. Evaluate risks for your Azure applications. This is the time to understand the scope of your risk from a DDoS attack if you haven’t done so already.
a. If there are virtual networks with applications exposed over the public Internet, we strongly recommend enabling DDoS Protection on those virtual networks. Resources in a virtual network that requires protection against DDoS attacks are Application Gateway/WAF, Load Balancer, virtual machines, and Azure Firewall. Review “DDos Protection reference architectures” to get more details on reference architectures to protect resources in virtual networks against DDoS attacks.
i. This PowerShell script will iterate all VNets overall subscriptions to which a user has access, and will output two tables, VNets with DDoS Protection enabled and VNets with DDoS Protection disabled.
b. You must ensure your applications don’t have a single point of failure and can auto-scale as the traffic volume increases during the peak period. Refer to the fundamental best practices for building DDoS-resilient services in Azure for more details.
c. Use network security groups (NSGs) to block unwanted ports minimizing attack footprint of your applications.
2. Validate your assumptions. Planning and preparation are crucial to understanding how a system will perform during a DDoS attack. You should be proactive to defend against DDoS attacks and not wait for an attack to happen and then act.
a. It is essential that you understand the normal behavior of an application and prepare to act if the application is not behaving as expected during a DDoS attack. Have monitors configured for your business-critical applications that mimic client behavior, and notify you when relevant anomalies are detected. Refer to monitoring and diagnostics best practices to gain insights on the health of your application.
b. Azure Application Insights is an extensible application performance management (APM) service for web developers on multiple platforms. Use Application Insights to monitor your live web application. It automatically detects performance anomalies. It includes analytics tools to help you diagnose issues and to understand what users do with your app. It’s designed to help you continuously improve performance and usability.
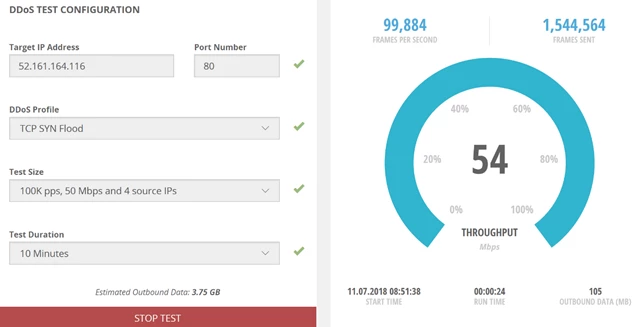
c. Finally, test your assumptions about how your services will respond to an attack by generating traffic against your applications to simulate DDoS attack. Don’t wait for an actual attack to happen! We have partnered with Ixia, a Keysight company, to provide a self-service traffic generator (BreakingPoint Cloud) that allows Azure DDoS Protection customers to simulate DDoS test traffic against their Azure public endpoints.
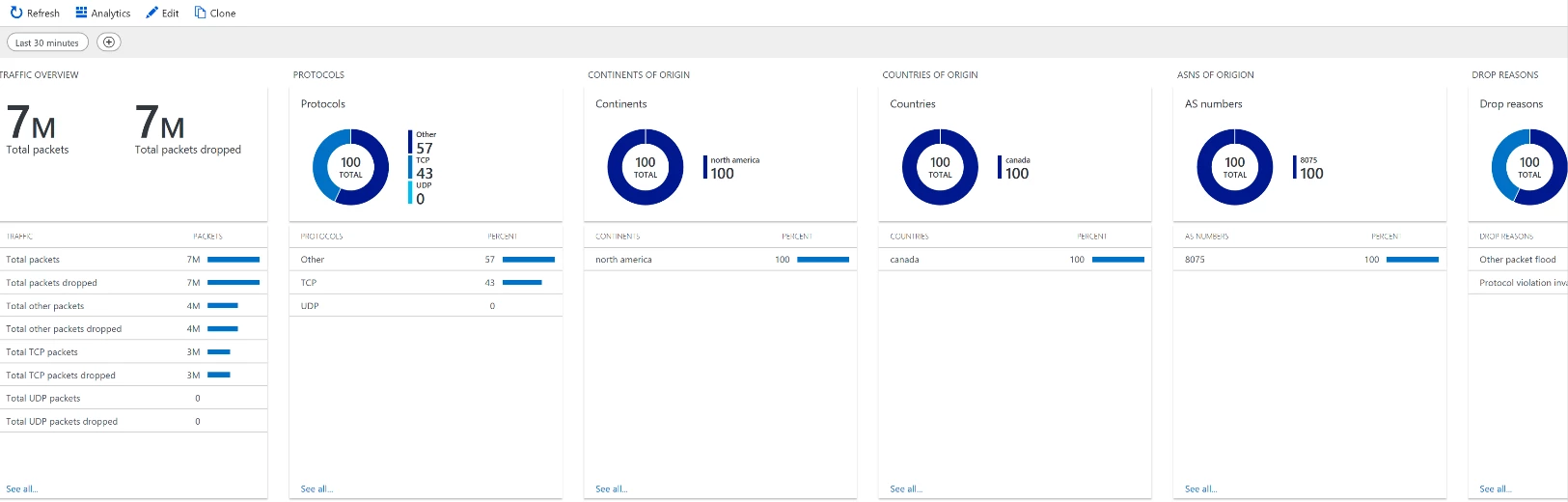
3. Configure Alerts and Attack Analytics. Azure DDoS Protection identifies and mitigates DDoS attacks without any user intervention.
a. To get notified when there’s an active mitigation for a protected public IP, we recommend configuring an alert on the metric Under DDoS attack or not.
b. You can additionally choose to create alerts for the other DDoS metrics and configure attack analytics to understand the scale of the attack, traffic being dropped, and other details.
When to contact Microsoft support
- During a DDoS attack if you find that the performance of the protected resource is severely degraded, or the resource is not available. Review step 2 above on configuring monitors to detect resource availability and performance issues.
- You think your resource is under DDoS attack, but DDoS Protection service is not mitigating the attack effectively.
- You’re planning a viral event that will significantly increase your network traffic.
For attacks that have a critical business impact, create a severity-A support ticket to engage DDoS Rapid Response team.
