Enabling Open Enclave SDK for the intelligent edge and simplifying the development of trusted applications across operating systems and hardware platforms.
Today we are excited to announce the cross-platform availability of the Open Enclave SDK for devices at the intelligent edge, as well as the preview of integration of Open Enclave and the Azure IoT Edge security manager. Together with our partners, we help organizations solve a very challenging security problem in the Internet of Things (IoT) – protecting code and data while in use at the edge. This includes securing compute workloads within the confines of Trusted Execution Environments (TEE) or simply enclaves, a concept called Confidential Computing. We offer a platform for developing applications that execute in enclaves, also known as trusted applications (TA), in a way that simplifies TA development for all audiences from hardcore hardware security experts to edge and cloud software applications developers.
With today’s announcement, Azure IoT Edge application developers can write TAs that root trust in any secure silicon TEE built on such enclaving technologies like ARM TrustZone®, Intel SGX, and embedded Secure Elements using Windows or Linux operating systems. This broad applicability across different enclave technologies and integration with IoT Edge greatly simplifies the work developers must do to protect data and devices at the edge. With accessibility by all security expertise as topmost goal, this integration is laden with features to truly simplify and shorten the journey from idea to at-scale production deployment of secure intelligent edge applications.
Allow me to provide some context.
The need for security at the intelligent edge
The intelligent edge extends cloud intelligence and analytics to edge devices. Azure IoT Edge is a fully managed service that delivers cloud intelligence locally by deploying Azure AI, Azure services, and custom logic directly on edge devices, such as gateway class devices. IoT Edge lets organizations bring AI and cloud analytics to the edge in cases where poor/no connectivity, high latency, or high costs would have prevented connection to the cloud.
Security is crucial for trust and integrity at the edge because by their very nature, IoT devices may not always be in trusted custody. More so, intelligent edge devices are much “smarter” than most IoT devices; in contrast to the common sensors and actuators class of IoT devices, they process highly sensitive workloads to generate equally sensitive results, thereby requiring strong protection for security goals like integrity, privacy, and confidentiality. Prior to the intelligent edge and edge-class IoT devices, these sensitive workloads existed only within the safety of the cloud. As these organizations move these sensitive workloads to the intelligent edge, they face increased risk from threats like tampering and forgery because the devices are often easily physically accessible. To reduce that risk, we created Azure Sphere, a solution for building highly-secured microcontroller devices, to help organizations build trustworthy devices for edge applications.
We recognize, however, that that IoT devices derive from a wide variety of hardware to allow for optimal solutions to the problems IoT targets; not all edge devices can be built on a microcontroller, meaning organizations need a greater variety of devices than they can build with Azure Sphere. With that variety, unfortunately, comes an expanded threat surface. For security to be effective, the solution must be uniform across devices to enable safe operation at scale. The heterogeneous nature of hardware in edge devices at the edge, more than its cloud counterpart, calls for very strong diligence. Just like the cloud, the intelligent edge requires a strong stance on security that addresses all threats, including emerging threats specific to operating at the edge.
With security in forethought, we designed Azure IoT Edge with a solid foundation of security principles for the intelligent edge. One year ago together with partners, we proved these principles thereby paving the way for all the possibilities towards achieving the highest security at the edge, but we did not stop there. We needed to scale this model by tapping into the domain expertise of the manufacturers who produce hardware root of trust modules. We also needed to isolate the IoT and cloud application developer from the complexity and nuances of working with secure silicon hardware. We achieved both goals with Azure IoT Edge security manager, a well-bounded trusted computing base whose sole mission is to protect the Azure IoT Edge device and its components by rooting the identity and sensitive workloads of the device in secure silicon also commonly known as a hardware security module (HSM). Azure IoT Edge security manager spurred the availability of secured edge devices from various Original Equipment Manufacturers (OEMs) as standard commercial off-the-shelf offerings. Although we’re happy with more availability of secured edge devices for our customers, we’re not done with our plan to increase the security of the intelligent edge.
Our next mission for securing the intelligent edge is to simplify access to security best practices for experts and non-experts for all security challenges, especially the big challenges. Until now, the ability to secure data at rest and data in transit has remained the sole province of security experts; on the other hand, it is generally considered a “solved problem,” meaning that non-experts can take advantage of the work experts have done and technology vendors have adopted. Emerging with the intelligent edge, however, is the need to protect data in use at the edge, and this is a tall challenge even to the experts. Confidential computing at the edge is today’s immediate, big security challenge. The solution is never to lower the bar for security, but to rise above the challenge and empower every application developer, security experts and non-experts alike, with the right tools.
Two months ago, Microsoft launched the Open Enclave SDK, an open source consistent API surface across enclave technologies and platforms from cloud to edge. This means that developers can use the same APIs across multiple enclaves, greatly reducing the complexity of following best practices and encouraging organizations to integrate applications with enclaves. Available with this version was the ability to write enclave applications for cloud workloads targeting TEE technology based on Intel Software Extension Guard (SGX) hardware technology and the Linux Operating System.
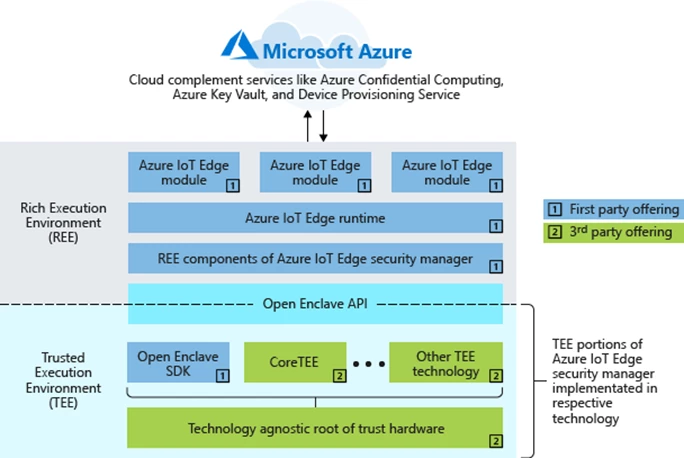
Figure 1. Architecture of cloud-edge consistent confidential computing framework showing where the Open Enclave API and abstraction fits in intelligent edge scenarios based on Azure IoT Edge. Open Enclave API offers the interface between TEE and a non-TEE environment commonly known as the Rich Execution Environment (REE). Underneath the Open Enclave API, adopters have the option of choosing Open Enclave SDK or an equivalent implementation from a third party offering.
Features
Secure silicon hardware abstraction
Open Enclave abstracts the developer experience away from the complexity and nuances of secure hardware, meaning that its easier for developers to learn to integrate their apps with secure hardware and easier for developers to write consistently secure software across devices.
Tooled for familiarity
Support for Visual Studio for Windows and GDB for Linux is available now so that developers can engage in already familiar development environments of choice.
Trusted Execution Environment (TEE) emulation for richer Trusted Application (TA) development
Until now, development of enclave applications or TA, especially for edge scenarios, has been the sole domain of a few experts with extensive experience in the specific TEE hardware offering. Development required access to the hardware, and debugging was extremely challenging given enclaving is about protecting data. We’re changing that by providing TEE emulation so that any developer, not just TEE hardware experts, can develop and debug trusted applications using familiar tools and with no need for the hardware. Developers can develop once and compile for multiple TEE hardware technology targets.
Designed for cloud-edge consistent confidential computing
Confidential compute resources are different for cloud and edge but the development experience for confidential compute workloads targeting the cloud and edge need not be different. In a single development environment, developers can create trusted applications for deployment in cloud enclaves like Azure Confidential Computing and in TEE enabled IoT Edge devices. Developers can create holistic security for applications where code and data are protected at rest, in flight, and while in use at the edge and in the cloud. In the very near future, they’ll be able to leverage Azure Device Provisioning Service (DPS), an at scale global provision service to provision and manage the lifecycle of confidential compute workloads and trusted applications consistently across cloud and edge.
Rich and diverse partner ecosystem
We strongly believe security in IoT is a community play. IoT deployments require trust from the device manufacturer to the solution integrator and solution backend—for this reason we’re aligning with industry leaders in various roles to enable truly end-to-end security for IoT devices, connections, and cloud.
| Technology | Silicon provider | Original design manufacturer (ODM) | Original equipment manufacturer (OEM) | Independent software vendor (ISV) | Mass production & distribution |
 |
 |
||||
 |
|
 |
Application possibilities with confidential computing using Azure IoT Edge
Azure IoT Edge with Open Enclave uses confidential computing to provide solutions to security challenges previously very difficult to surmount. It really comes down to protecting the executable delivering the business function.
TrustBox – One optimal path from evaluation to mass production
As organizations learn about the intelligent edge and begin projects, they often find themselves slowed down by unforeseen security and compliance challenges. In response, we are working with partners to shorten the journey from evaluation of a project to production. Until now, a typical experience entails developers evaluating and experimenting using many commercially available prototyping boards, such as Arduino-based boards or Raspberry Pis. Unfortunately, when the developers move to production, they find they have to switch boards to a solution that can meet the required security and compliance standards for their industry. Rather than switching boards later, developers should begin evaluation with boards that can later serve pilot and production needs while meeting compliance goals.
TrustBox is one option to address this need for prototype to production boards, providing a high-grade secure router and IoT gateway based around NXP Layerscape LS1012A networking processor that integrates hardware root of trust, cryptographic accelerators and network acceleration. Following deep security engineering and careful selection of components, TrustBox is certifiable to the highest levels of industry and security standards. TrustBox is the winner of the award for 2019 CES Best of Innovations: Cybersecurity and Personal Privacy.

Figure 2: TrustBox, a high-grade secure router & IoT gateway based on NXP Layerscape LS1012A, a member of NXP’s Layerscape family of hardware root of trust and cryptographic accelerators. TrustBox is available as is or customizable through Scalys for evaluation, pilot and production runs.
Availability of evaluation boards is just one of many steps to mass production which can be daunting where there is need to customize the boards. To this end we allied with NXP, Scalys, and Arrow Electronics, to provide an example of a complete supply chain from integrated circuit to final distribution.

Figure 3: The supply chain for TrustBox that is available now for all enclave secured device needs to include sourcing for evaluation and pilot runs, hardware customizations, and mass production. This is only one of many possibilities.
Scalys TrustBox is expected to ship in volume from February 2019, and you can pre-order from Scalys now. You can also start evaluating now with Grapeboard, the commercial grade electrical equivalent of TrustBox.
What’s next
One goal of the preview of Open Enclave integration with IoT Edge is to jumpstart hardware centric development by Original Equipment Manufacturers (OEM) towards availing TEE capable devices. Within the next few months we anticipate availability of TEE capable Azure IoT Edge certified devices that will deliver the same platform agnostic developer and deployment experience available today. At that time developers can also expect refined TA lifecycle management capabilities. Until then, the developer preview will include well documented platform specific setup scripts.
Enclaving technology for the edge has been around for many years in niche industries like banking and governments. Until now, access to the technology has been limited to few people with deep expertise on specific TEE hardware and enclaving technology. Today, in collaboration with partners, we’re offering the platform to simplify development of trusted applications at the edge, thereby extending this privilege to edge and cloud application developers of all abilities. Open sourcing of the various components of the newly expanded repository commences today.
- Get an overview on working with enclaves.
- Get started now with Linux on ARM TrustZone® using Grapeboard.
- Get started now with Windows OS on Intel SGX using Intel NUC7i3BNK.
- Learn more about developing intelligent edge applications using Azure IoT Edge.
- Learn more about open enclave at www.openenclave.io.
