Over the past few months, we added several new capabilities to Azure Virtual WAN which customers can embrace to significantly simplify routing design and management in Azure, and secure traffic flows. Before we introduce these new capabilities, let us revisit what Azure Virtual WAN is.
Azure Virtual WAN is a unified hub and spoke-based architecture providing Network-as-a-Service (NaaS) for connectivity, security, and routing using the Microsoft Global Backbone. Customers transforming their networks by migrating to Azure cloud or utilizing hybrid deployments shared between Azure and their traditional data center or on-premises networks, take advantage of Azure Virtual WAN for scalability, ease of deployment, reduced IT costs, low latency, transit functionalities, high performance, and advanced routing.
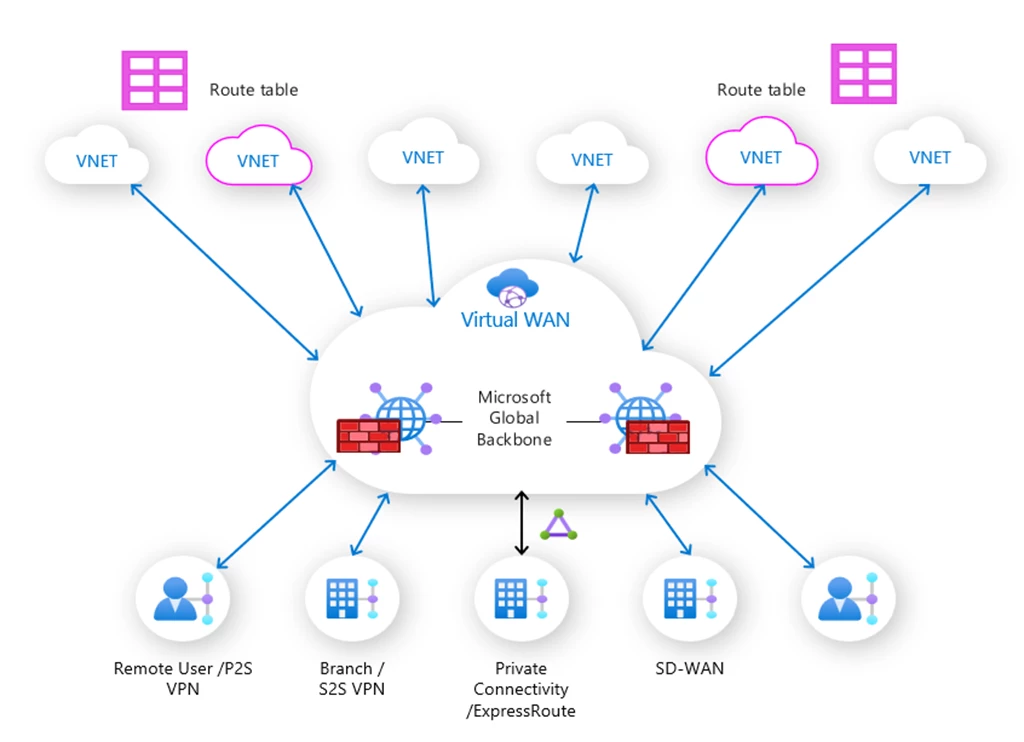
Customers architect networks for their services by defining the requirements along with three design aspects—connectivity, security, and routing, and then adopting key capabilities Azure Virtual WAN brings together, as shown in the figure below.
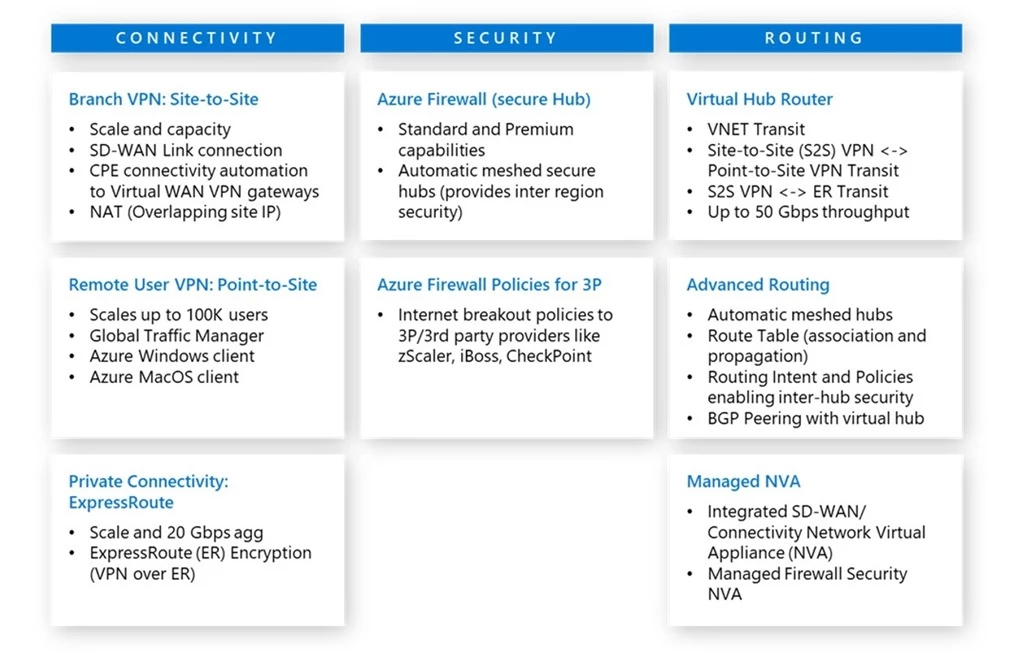
Today, we are announcing new features that customers can utilize when they are applicable to their scenarios.
New partner solutions integrated with Azure Virtual WAN
We are excited to announce that two new partners are integrated with Azure Virtual WAN.


Fortinet FortiGate is the first dual-role SD-WAN and security-enabled Network Virtual Appliance (NVA) to be integrated natively with the Azure Virtual WAN hub, greatly improving the end-to-end experience and life-cycle management of using FortiGate NVAs in Azure.Customers can select from a carefully curated menu of configurations and throughputs, and with a few simple clicks, can easily deploy and configure FortiGate in Azure. No more do you have to worry about setting up load balancers, user-defined routing and choosing the right virtual machine configurations and networking settings. With a few clicks in a managed application and a few quick configurations in the Azure Virtual WAN portal to configure our new routing model (Routing Intent and Routing Policies), you can easily configure your on-premises and virtual networks to send traffic to an Azure Virtual WAN hub hosted FortiGate next-generation firewall (NGFW) for inspection.Customers can also rest assured that Azure Virtual WAN and FortiGate are built with high availability and resiliency in mind, allowing you to focus on running your business. Read more about the Fortinet FortiGate integration.
- Versa SASE integration with Azure Virtual WAN hub allows customers to take advantage of its top-notch SD-WAN capabilities with Azure Virtual WAN’s signature any-to-any routing, all in one place for easy configuration and deployment. With this integration, customers can now deploy the Versa in the virtual hub for a central connectivity point into Azure and utilize Microsoft’s backbone while blending network, security, and application awareness from Versa. Read more about the Versa SASE integration.
Branch connectivity (Site-to-Site VPN)
The following features are now available for configuring connectivity from on-premises (also referred to as branches) to Site-to-Site VPN gateway in a virtual hub.
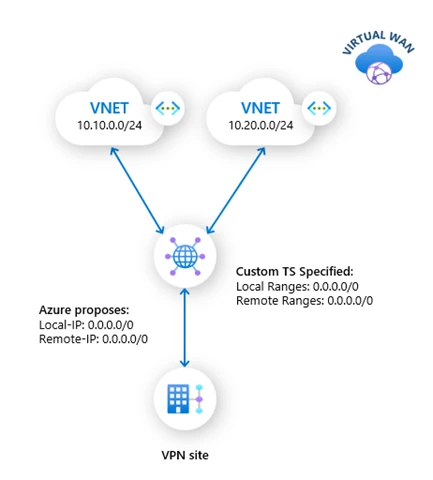
Custom traffic selectors
Customers using policy-based VPN may now specify custom traffic selectors on the VPN gateways in virtual hub, to assure pre-defined and consistent routing across site-to-site connections. Custom traffic selectors allow for specifying exact, wide, or narrow traffic selectors that the VPN gateway proposes or accepts during internet key exchange (IKE) negotiations.
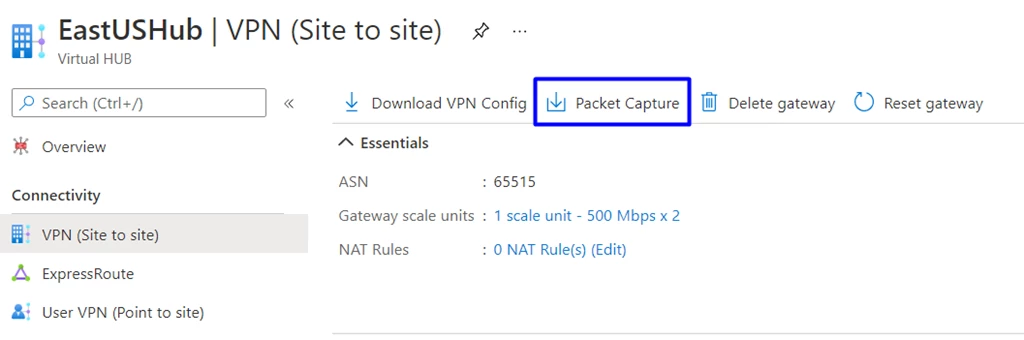
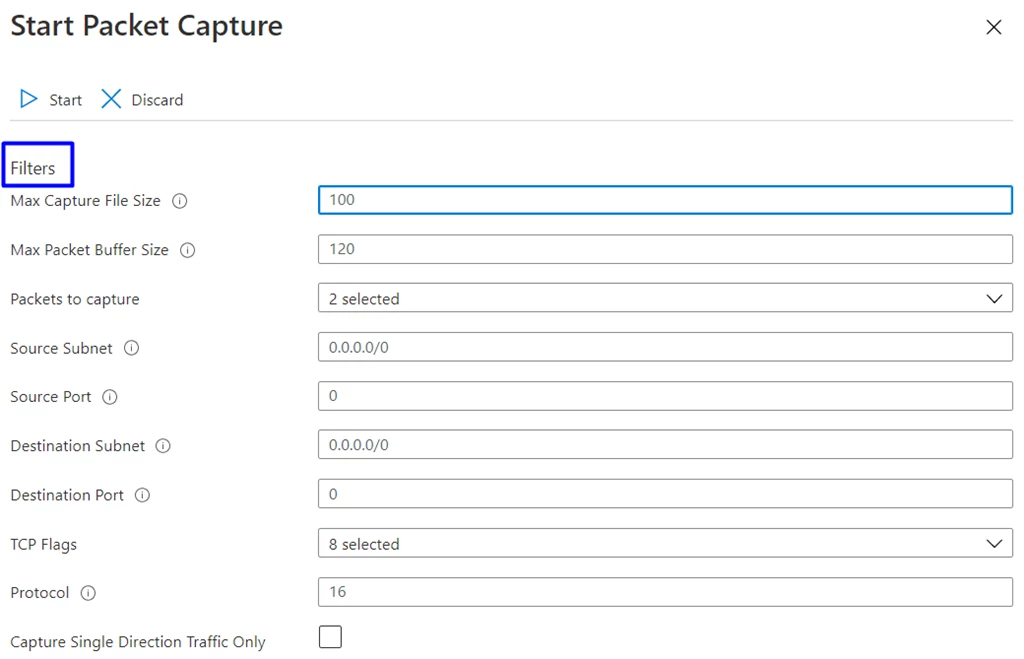
Packet Capture
Connectivity and performance-related problems are often complex. It can take significant time and effort just to narrow down the cause of the problem. Packet capture on Azure Virtual WAN VPN gateway captures all packets across all connections for a holistic view. This can help you determine whether the problem is within the on-premises network or Azure, or somewhere in between. The niche filtering capability allows the user to focus on specific behaviors, packet types, source and destination subnets, and more to efficiently debug the issue.
Remote user connectivity (Point-to-Site VPN)
The resources that customers host in Azure or on-premises are made available to their remote users through Azure Virtual WAN by enabling Internet Protocol Security (IPsec) or Internet Key Exchange version 2 (IKEv2) or OpenVPN-based VPN connectivity to Point-to-Site VPN gateway in virtual hub. The design for managing authentication for users is now more flexible with the new feature below.
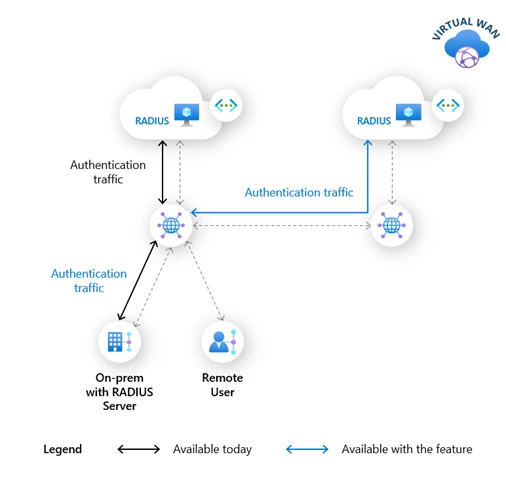
Remote or on-premises RADIUS servers
Users connecting to virtual hub can now be authenticated during VPN connection set up, using RADIUS servers located on-premises or in a remote spoke virtual network. Until today, only those RADIUS servers deployed in a virtual network connected to a virtual hub, could be used to authenticate users connected to that virtual hub.
This capability simplifies RADIUS deployments, reduces management overhead, and provides high-availability design options by using RADIUS servers across Azure regions or across Azure and on-premises. This capability will be available in early 2022.
Advanced Routing
Below are the new routing capabilities of a virtual hub.
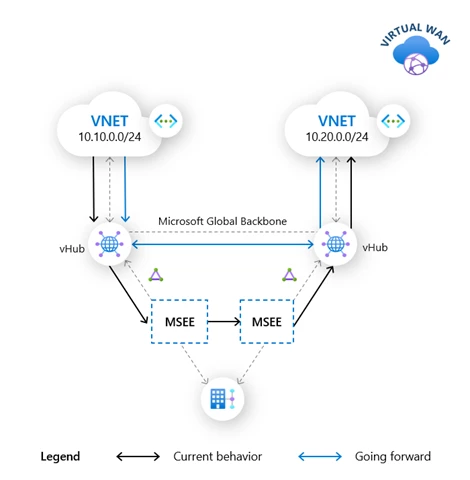
Hub to hub preference over ExpressRoute (in gated preview)
In some Azure Virtual WAN scenarios, customers choose to connect their on-premises to Azure using one ExpressRoute circuit connection to multiple hubs. When there is a VNET-to-VNET traffic flow between virtual networks connected to different hubs, the traffic flow traverses the multi-tenant routers, called MSEE, in Microsoft points-of-presence (POPs) where the ExpressRoute circuit terminates.
When customers enable the new feature for their Virtual WAN, the same traffic would then take an optimal path directly between the hubs, and therefore experience improved latencies. The new path is shown in the diagram using blue arrows. This will become the default behavior once the feature is generally available.
To access the preview, contact previewpreferh2h@microsoft.com with your Virtual WAN ID, Subscription ID, and Azure Region.
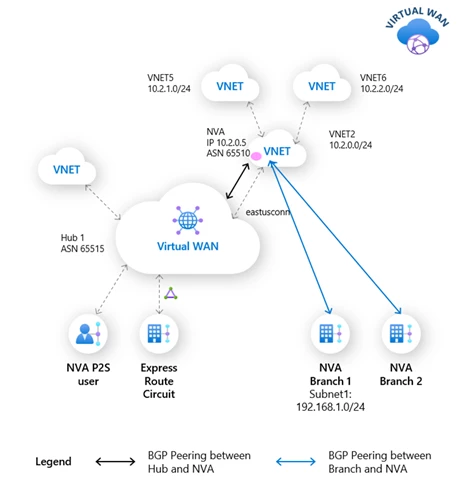
BGP peering with Azure Virtual WAN hub (in gated preview)
Enterprises using Azure in hybrid infrastructure model often have SD-WAN appliances in their on-premises that connect to compatible Network Virtual Appliances (NVAs) in spoke virtual networks of a virtual WAN. In such scenarios, the NVAs serve as the gateways to Azure for their on-premises networks and routing information exchange between them is configured using Border Gateway Protocol (BGP). Customers establish connectivity between NVA and virtual hub using static routes, to access services deployed in virtual networks connected to hub, and to reach their on-premises connected to hub through ExpressRoute, until today.
With the BGP endpoint in virtual hub, the routing information from NVA to virtual hub can now be exchanged using BGP. This eliminates the need for complex static route configuration between NVA and virtual hub. In addition, all network changes within the on-premises networks that resulted in manual updates to such static routes in the past can now be dynamically advertised from NVA to hub through BGP, which further simplifies maintenance.
Routing Intent and Policies enabling inter-hub security (in gated preview)
Customers securing traffic using Azure Firewall manager are required to set up policies manually to identify the flows. This applies to all traffic which is internet-bound or private—that is, between on-premises to virtual networks across Point-to-Site, Site-to-Site, and ExpressRoute connections and virtual hub. Using Routing Intent, customers can achieve this without complex manual configuration by simply specifying whether the virtual hub forwards internet-bound, private, or inter-hub traffic flow route through Azure Firewall or not. Furthermore, customers can configure their deployments to inspect all flows (East-West, North-South, and Azure as internet edge) using an Azure Firewall or Network Virtual Appliance (such as Fortinet) deployed in the Azure Virtual WAN hub.
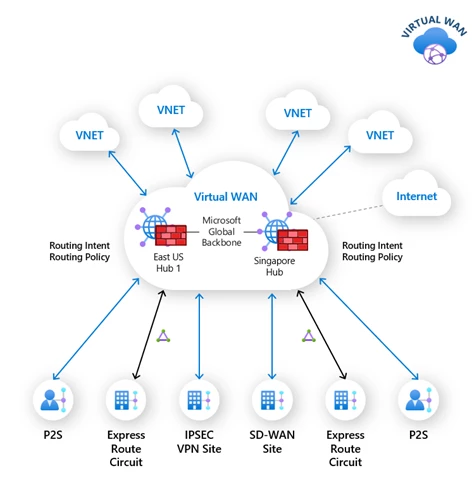
In conclusion, the needs of every organization are unique and as their networks are migrated from traditional data centers or on-premises to cloud-only, or hybrid model, the journey involves complex design decisions. Azure Virtual WAN aims at making this journey smooth with NaaS services that are simple to use and efficient. Each new capability discussed so far makes Azure Virtual WAN more beneficial to our customers.
Learn more
To get started with Azure Virtual WAN or try the new features, please refer to the resources below. For features in gated preview, please look at the corresponding documentation to learn more about enabling the preview for your subscription.
- Azure Virtual WAN Global Transit Architecture.
- SD-WAN Connectivity Architecture with Azure Virtual WAN.
- Azure Virtual WAN Monitoring (metrics and logs).
- BGP Peering with virtual hub.
- Configure Routing Intent and Policies.
- Perform a packet capture.
- Azure Virtual WAN pricing.
- Azure Virtual WAN FAQ.
- Azure Virtual WAN Documentation.
- Azure Virtual WAN videos.
