We heard from several customers that you need a way to view your Azure Security Center alerts in your SIEM solution for a centralized view of your security posture across your organization. Today, we are excited to announce the public preview of a new feature called SIEM Export that allows you to export Azure Security Center alerts into popular SIEM solutions such as Splunk and IBM QRadar. We are continuing to invest in the number of partners we support. This feature is part of our on-going commitment to provide unified security management and protection for your cloud and on-premises workloads.
Security Center uses a variety of detection capabilities to alert you of potential threats to your environment. The alerts can tell you what triggered the alert, what in your environment was targeted, the source of the attack, and if necessary, remediation steps. You also have the flexibility to set up custom alerts to address specific needs in your environment.
Now you can take these alerts from Security Center and integrate them into your own SIEM solutions, so you can quickly view what needs your attention from one management place and take action.
To move your Azure Security Center alerts to a partner SIEM solution, you first need to complete a few steps of using Azure Monitor and then Event Hub. Azure Security Center alerts are published to the Azure Monitor Activity log, one of the log types available through Azure Monitor. From Azure Monitor, you export your logs using the Azure Monitoring single pipeline to an Event Hub. Finally, on the SIEM server, you need to install a partner SIEM connector. Then you can stream from the Event Hub your logs into the SIEM solution.
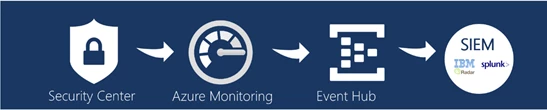
Figure 1 : High-level pipeline overview
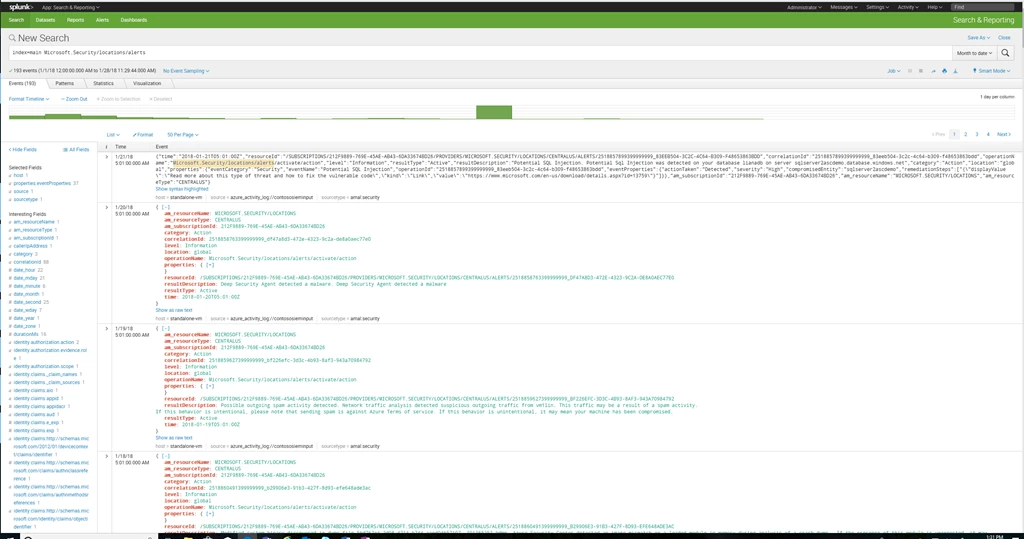
Figure 2: Azure Security Center alerts in Splunk
In this public preview version, due to customer feedback, we prioritized releasing security alerts. In upcoming releases, we will enrich the data set with security recommendations.
To get started with the integration of Azure Security Center alerts with your SIEM solutions, follow the detailed steps in our documentation.
For any feedback/additional information contact: ASC_SIEM@microsoft.com.
This feature is available for the standard Azure Security Center tier. Try Azure Security Center alerts for your SIEM solutions today.
