This post was co-authored by Eliran Azulai, Principal Program Manager, Azure Networking.
Today, we are announcing new Azure Firewall capabilities as well as updates for August 2021.
- Azure Firewall supports US West 3, Jio India West, and Brazil Southeast.
- Auto-generated self-signed certificates for Azure Firewall Premium SKU.
- Secure Hub now supports Availability Zones.
- Deploy Azure Firewall without public IP in Forced Tunnel mode.
- Configure pre-existing Azure Firewalls in Force Tunnel mode using stop or start commands.
Azure Firewall regional expansion
We expanded Azure Firewall service to three new public regions including US West 3, Jio India West, and Brazil Southeast. Both Standard and Premium Firewall SKUs are available in the new public regions. Firewall Policy support is planned to release shortly.
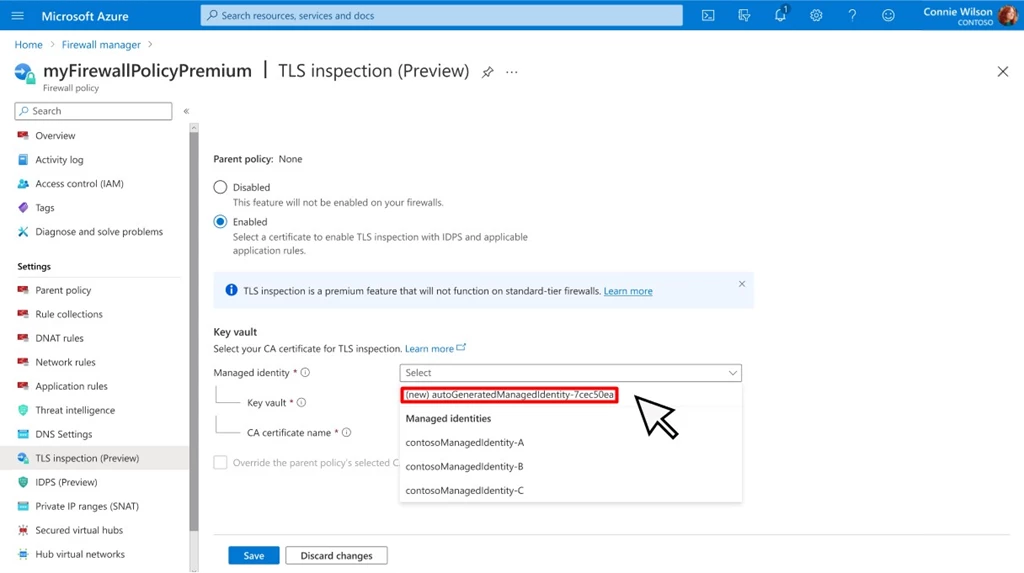
Azure Firewall Premium SKU support for self-signed certificates
For non-production deployments, you can use the Azure Firewall Premium certification auto-generation mechanism, which automatically creates for you the following three resources, ties them together, and sets up transport layer security (TLS) inspection with a single click of a button:
- Managed Identity.
- Key Vault.
- Self-signed intermediate CA certificate.
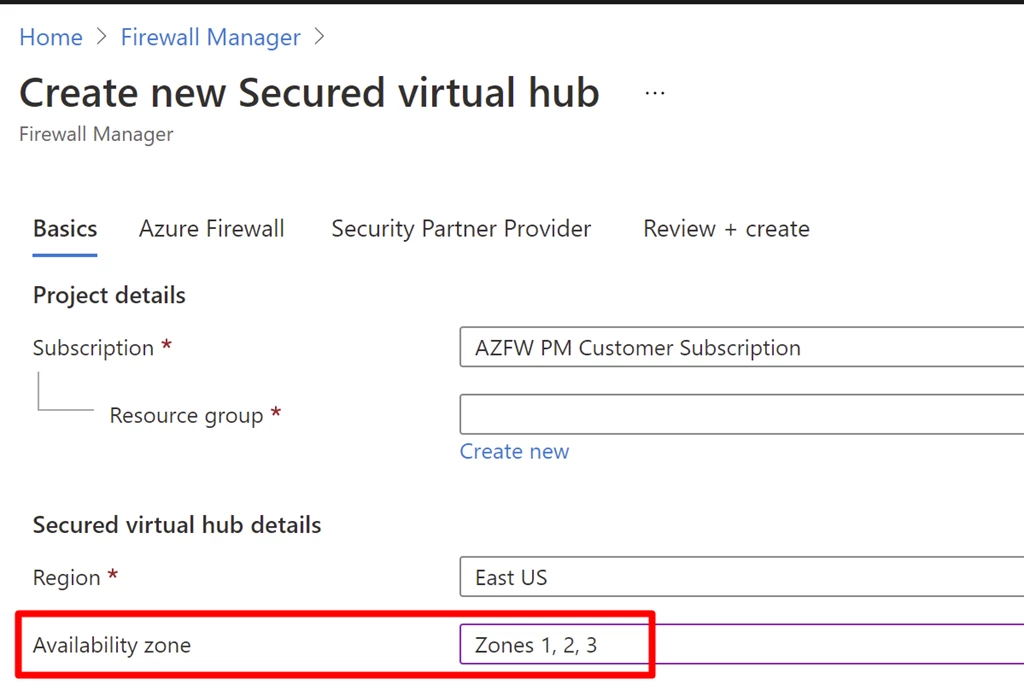
Secure Hub now supports Availability Zones
With Availability Zones, your availability increases to 99.99 percent uptime. A secured virtual hub can now be configured during deployment to span multiple Availability Zones for increased availability.
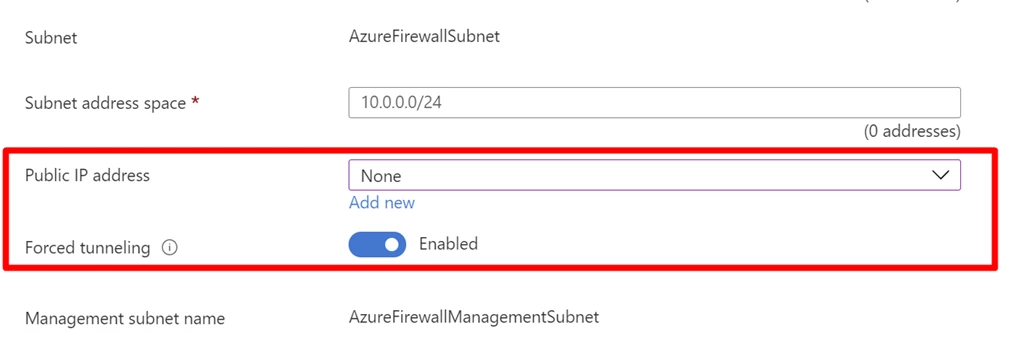
Deploy Azure Firewall without public IP in Forced Tunnel mode
Azure Firewall service requires public IP for its operational purposes. While secure, some deployments don’t prefer exposing public IP directly to the internet. In such cases, customers can deploy Azure Firewall in Forced Tunnel mode. This configuration creates a management NIC which is used by Azure Firewall for its operations. The Tenant Datapath network can be configured without a public IP, and internet traffic can be forced tunneled to another Firewall or completely blocked.
Note that Forced Tunnel mode cannot be configured at Run Time. You can either redeploy the Firewall or use the stop and start facility to reconfigure existing Azure Firewalls in Forced Tunnel mode. Secure Hub Firewalls are always deployed in Forced Tunnel mode.
Next steps
For more information on everything we covered above, see the following documentation:
