UPDATE: This feature is now out of preview, you can read about the latest changes and updates here.
Azure Websites Authentication/Authorization allows you to quickly and easily restrict access to your websites running on Azure Websites by leveraging Azure Active Directory. While this is something you could do today, Websites users will greatly benefit from a simplified and streamlined solution that does not require any complex configuration, code changes, or maintenance. Furthermore, this solution is stack agnostic so it works for all the different stacks supported by Azure Websites today, regardless of your site being coded in .NET, PHP, Node, Java or Python and since this solution is provided as part of the platform it will scale with your application. Azure Websites Authentication/Authorization simplifies the process of restricting access to your site to only three steps:
- Prepare your directory (if necessary)
- Step through the Authentication/Authorization configuration wizard for your website in the Azure Portal
- Select the Directory associated with the Website
- Select or create the Azure Active Directory app for the Website
- Your Website is now restricted so only users in the directory you selected in step 2 will be able to access it.
Configure Azure Website Authentication/Authorization
Step 1 Prepare your Directory
The first step to restricting access to your website using Azure Websites Authentication/Authorization is to get your Azure Active Directory ready. This is only necessary if you don’t already have a Directory ready to use. Azure Active Directory will handle user management and the log-in mechanics for your site. I’m not going to go into details on how setup Azure Active Directory, but here are some helpful resources to get you started:
Step 2 Configure your site
The next step involves linking your Azure Website to the Azure Active Directory that will provide the user management for your site. To do this you will use the Azure Management Portal. Navigate to your site and click on the configure tab. There is a new configuration section in this page called authentication/authorization.
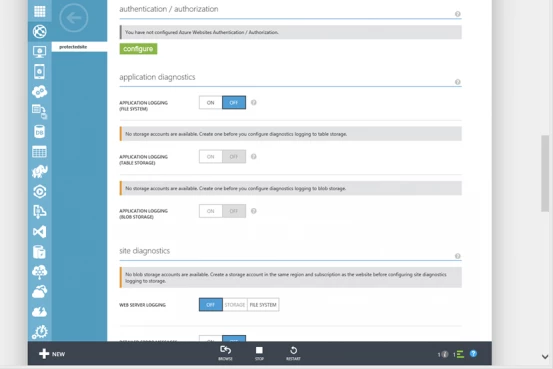
In the authentication/authorization section the configure button launches the wizard that will guide through the configuration
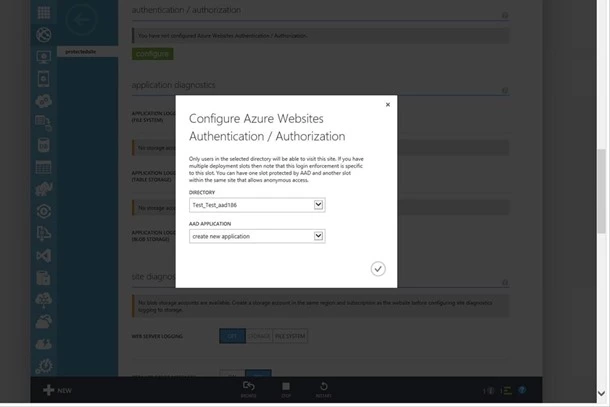
In the wizard you will be able to select a directory if there are more than one configured for your subscription and an AAD Application. From the drop down you can select and existing AAD application or chose to create a new one. The AAD application will represent this website in Azure Active Directory. Once you click OK the necessary configuration will be created in Azure Active Directory and propagated to your site.
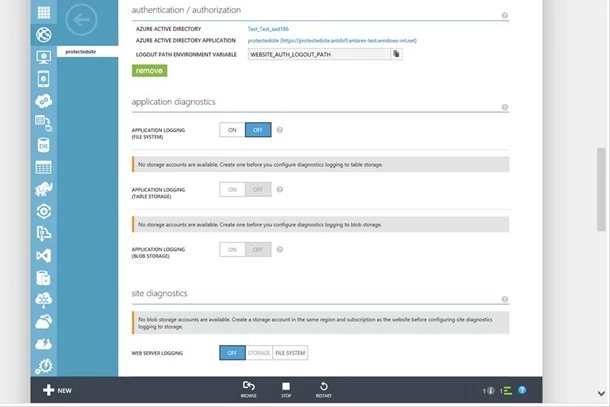
Once the website is configured the authentication/authorization section provides deep links to the Azure Active Directory and Azure Active Directory Application this website is linked to. The Logout Path Environment Variable (WEBSITE_AUTH_LOGOUT_PATH) can be used by the website to direct user’s user to a unique URL that will act as a logout. We have published a very simple asp.net sample application you can use to test this out and see how to read the authenticated users data from the session as well as how to leverage the Log-Out mechanism through the environment Variable. You can find the sample application here
Current Limitations
There are some limitation to the current preview release of this feature:
- With the current release all users in the configured directory will have access the application.
- With the current release the whole site is placed behind login the requirement.
- Head less authentication/authorization for API scenarios or service to service scenarios are not currently supported.
- With the current release there is no distributed log-out so logging the user out will only do so for this application and not all global sessions.
