This blog post was co-authored with Roy Levin, Senior Data Scientist
With the reality of working from home, more people and devices are now accessing corporate data across home networks. This raises the risks of cyber-attacks and elevates the importance of proper data protection. One of the resources most targeted by attackers is data storage, which can hold critical business data and sensitive information.
To help Azure customers better protect their storage environment, Azure Security Center provides Azure Defender for Storage, which alerts customers upon unusual and potentially harmful attempts to access or exploit their storage accounts.
What’s new in Azure Defender for Storage
As with all Microsoft security products, customers of Azure Defender for Storage benefit from Microsoft threat intelligence to detect and hunt for attacks. Microsoft amasses billions of signals for a holistic view of the security ecosystem. These shared signals and threat intelligence enrich Microsoft products and allow them to offer context, relevance, and priority management to help security teams act more efficiently.
Based on these capabilities, Azure Defender for Storage now alerts customers also upon the detection of malicious activities such as:
- Upload of potential malware (using hash reputation analysis).
- Phishing campaigns hosted on a storage account.
- Access from suspicious IP addresses, such as TOR exit nodes.
In addition, leveraging the advanced capabilities of Microsoft threat intelligence helps us enrich our current Azure Defender for Storage alert and future detections.
To benefit from Azure Defender for Storage, you can easily configure it on your subscription or storage accounts and start your 30-day trial today.
Cyberattacks on cloud data stores are on the rise
Nowadays, more and more organizations place their critical business data assets in the cloud using PaaS data services. Azure Storage is among the most widely used of these services. The amount of data obtained and analyzed by organizations continues to grow at an increasing rate, and data is becoming increasingly vital in guiding critical business decisions.
With this rise in usage, the risks of cyberattacks and data breaches are also growing, especially for business-critical data and sensitive information. Cyber incidents cause organizations to lose money, data, productivity, and consumer trust. The average total cost of a data breach is $3.86 million. On average, it takes 280 days to identify and contain a breach, and 17 percent of cyberattacks involve malware.
It’s clear that organizations worldwide need protection, detection, and rapid-fire response mechanisms to these threats. Yet, on average, more than 99 days pass between infiltration and detection, which is like leaving the front door wide open for over four months. Therefore, proper threat intelligence and detection are needed.
Azure Defender for Storage improved threat detections
1. Detecting upload of malware and malicious content
Storage accounts are widely used for data distribution, thus they may get infected with malware and cause it to spread to additional users and resources. This may make them vulnerable to attacks and exploits, putting sensitive organizational data at risk.
Malware reaching storage accounts was a top concern raised by our customers, and to help address it, Azure Defender for Storage now utilizes advanced hash reputation analysis to detect malware uploaded to storage accounts in Azure. This can help detect ransomware, viruses, spyware, and other malware uploaded to your accounts.
A security alert is automatically triggered upon detection of potential malware uploaded to an Azure Storage account.
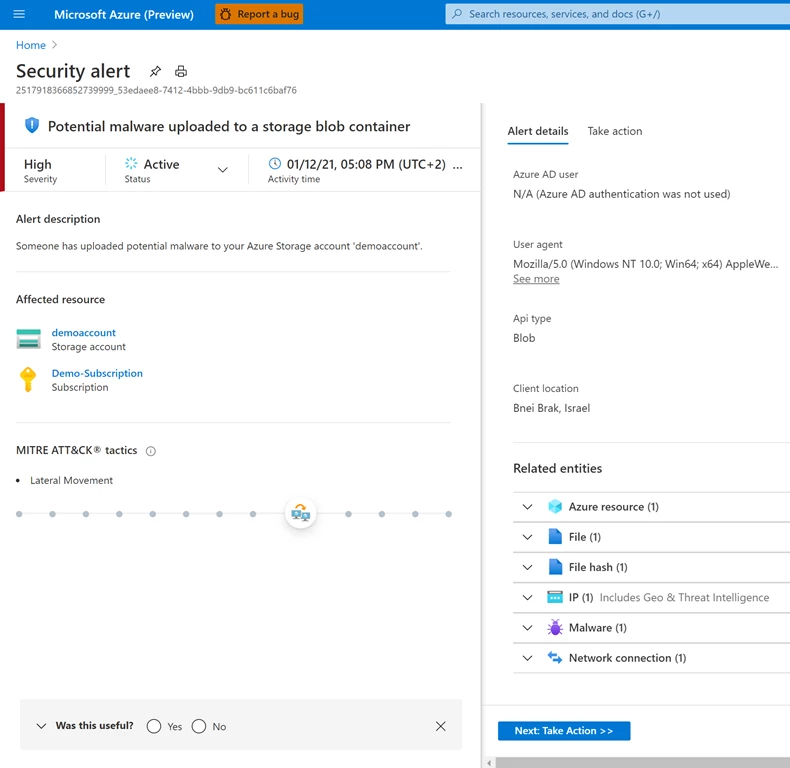
In addition, an email notification is sent to the owner of the storage account:
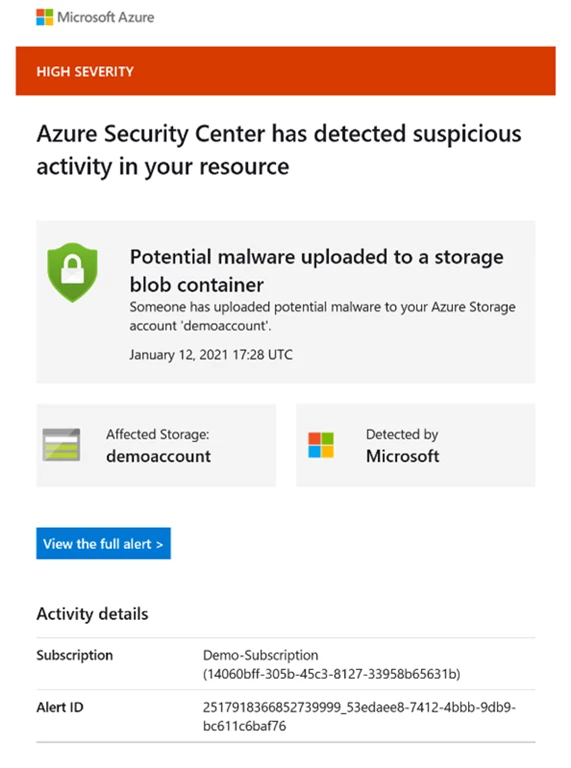
It’s important to notice that, currently, Azure Defender for Storage doesn’t offer malware scanning capabilities. For those interested in malware scanning upon file or blob upload, they might consider using a third-party solution.
Azure Blob Storage is a very powerful and cost-effective storage solution, allowing for fast and cheap storage and retrieval of large amounts of files. We use it on all our systems and often have millions of documents in Blob Storage for a given system. With PaaS solutions, it can, however, be a challenge to check files for malware before they are stored in Blob Storage. It is incredibly easy to enable the new “Malware Reputation Screening” for storage accounts at scale, it offers us a built-in basic level of protection against malware, which is often sufficient, thus saving us the overhead to set up and manage complex malware scanning solutions.”—Frans Lytzen, CTO at NewOrbit
In addition to malware, Azure Defender for Storage also alerts upon unusual upload of executable (.exe) and service package (.cspkg) files which can be used to breach your environment.
2. Detecting phishing campaigns hosted on Azure Storage
Phishing is a type of social engineering attack often used to steal user data, including login credentials, credit card numbers, and other sensitive info. Email phishing attacks are among the most common types of phishing attacks, where cybercriminals spread a high volume of fake emails designed to trick visitors into entering their corporate credentials or financial information into a web form that looks genuine or to download attachments containing malware, such as ransomware.
Email phishing attacks are becoming more sophisticated, making it even harder for users to distinguish between legitimate and malicious messages. One of the ways attackers use to make their phishing webpages look genuine, both to users and security gateways, is to host those pages on certified cloud storage, such as Azure Storage.
Using dedicated storage accounts to host the phishing content makes it easier to detect and block such accounts. So, attackers constantly try to sneak their phishing content and webpages into others’ storage accounts that allow uploading content.
Microsoft threat intelligence amasses and analyzes several signals to help better identify phishing campaigns, and now Azure Defender for Storage can alert when it detects that one of your Azure Storage accounts hosts content used in a phishing attack affecting users of Microsoft 365.
3. Detecting access from suspicious IP addresses
The reputation of client IP addresses that access Azure Storage are continuously monitored. These reputations are based on a threat intelligence feed which contains data from various sources, including first and third-party threat intelligence feeds, curated from honeypots, malicious IP addresses, botnets, malware detonation feeds, and more, also including analyst-based observations and collections.
This provides another layer of protection for Azure Storage as customers are alerted when IP addresses with questionable reputations access their storage accounts. Moreover, existing alerts such as access from unusual locations are enriched with information about the reputation of this anomalous client IP address. Consequently, customers now receive alerts with better explanations, as well as elevated fidelity and severity.
Figure 1 illustrates how access to storage is analyzed by examining the reputation of the client IP address according to this feed.
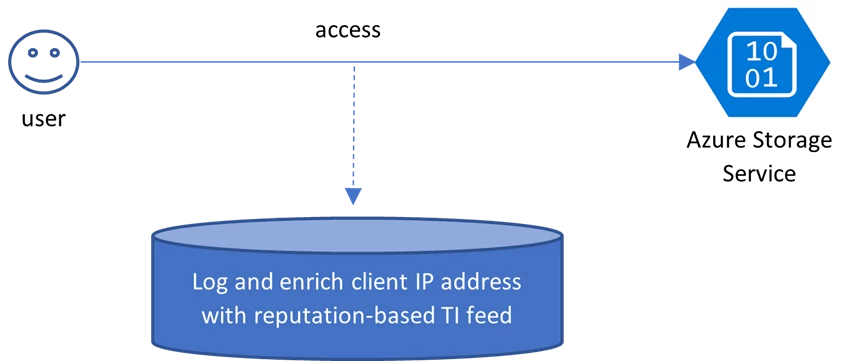
Figure 1: Enriching Azure Storage Service access logs with the reputation of client IP.
This new alert has been vital in revealing and preventing cyber-attacks, which may have otherwise caused severe damage, as observed in two real customer case-study scenarios described below.
First case study: Detecting malicious access to critical customer data
Figure 2 depicts a hybrid architecture in which on-premises machines are monitored using Security Center Log Analytics agent. These machines access a storage service via a gateway that has an external IP address and is installed on-premises. The storage is protected by a firewall, which permits access only from the dedicated gateway.
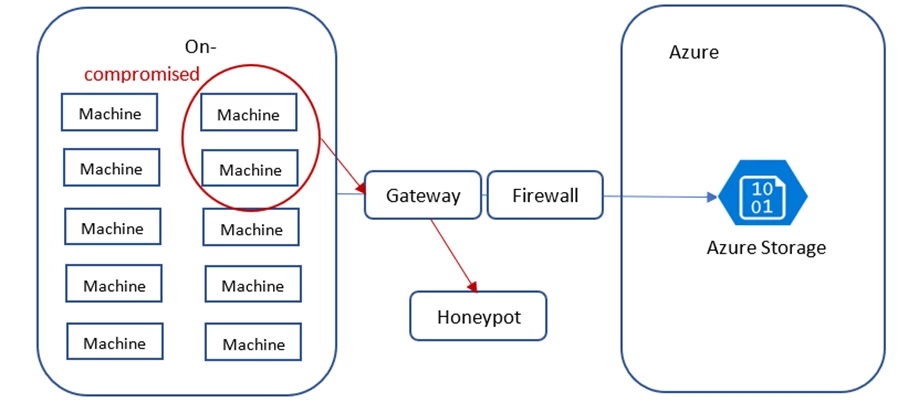
Figure 2: Attack on a hybrid environment uncovered by tracking IP reputation.
Two on-premises machines were infected by malware. Although the malware remains undetected, the compromise was exposed by observing the two machines initiate access to a honeypot via the gateway. Our Azure Defender for Storage service used the TI feed about IPs that have accessed a honeypot network. The customer was alerted accordingly, preventing a situation in which compromised machines will access critical customer data. Note that the firewall that was setup was not enough to guarantee that compromised machines will not be able to access critical data. Hence this detection was vital in uncovering the breach.
Second case study: Identifying potential malware infection from virtual machines
Figure 3 depicts a virtual machine (VM) infected with a bot spreading an innocent-looking malware to SMB-protocol enabled file systems (such as Azure File Storage). The malware can be anything from an executable file or DLL to an Excel or Word file with macros enabled. The infected virtual machine’s communication to its Command and Control Server is intercepted and reported to the TI feed. Azure Defender for Storage flagged access from the VM’s IP address even though it’s not hosted in Azure. As soon as the infected VM copied a file to a protected Azure Storage account, the incident was reported as an alert to the customer, who immediately mitigated the risk preventing further infection to customer machines.
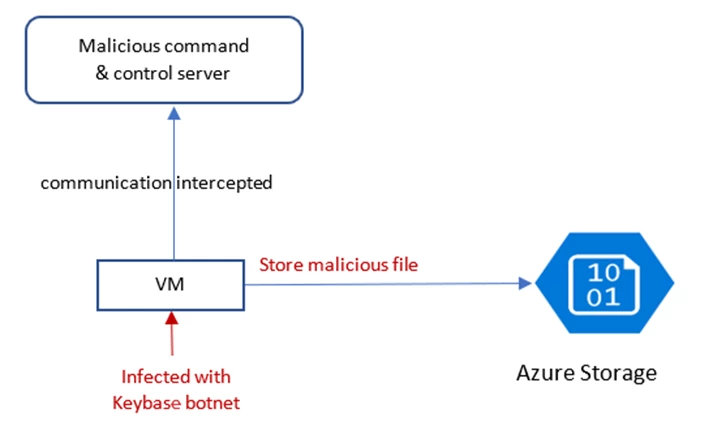
Figure 3: A Keybase-infected VM stores a malicious file in Azure Storage.
Get started today
We encourage you to try out Azure Defender for Storage and start detecting potential threats on your blob containers, file shares, and data lakes. Azure Defender for Storage needs to be enabled on the storage accounts containing the data you want to protect.
- We recommend enabling Azure Defender for Storage on the subscription level by following the instructions here: Configure Azure Defender for Storage.
- For validation or penetration testing purposes, you can trigger the TOR alert of Azure Defender for Storage by following the steps in our documentation.
- Learn more about the pricing of Azure Defender for Storage in Azure Defender pricing page.
For more information on Azure Security Center, please visit Azure Security Center web page.
