Attackers commonly target cloud environments with Brute Force or Port Scanning attacks, typically against management ports like RDP and SSH that are left open to enable administrators access. In addition to detecting and alerting you to these attacks, Azure Security Center just released a new Just-In-Time (JIT) VM Access mechanism. JIT VM Access, now in public preview, significantly reduces your exposure to these attacks by enabling you to deny persistent access while providing controlled, audited access to VMs when needed.
Based on the security policy you set, Azure Security Center can recommend that JIT Access be enabled on your existing VMs and any new ones that are created. When JIT VM Access is enabled, Azure Security Center locks down inbound traffic to defined ports by creating Network Security Group rule(s). You can request access to the VM when needed, which opens the needed port for an approved amount of time, from approved IP addresses, and only for users with proper permissions. Requests are logged in the Azure Activity Log, so you can easily monitor and audit access. You can also enable JIT VM Access, configure policies and request access through Powershell cmdlets.
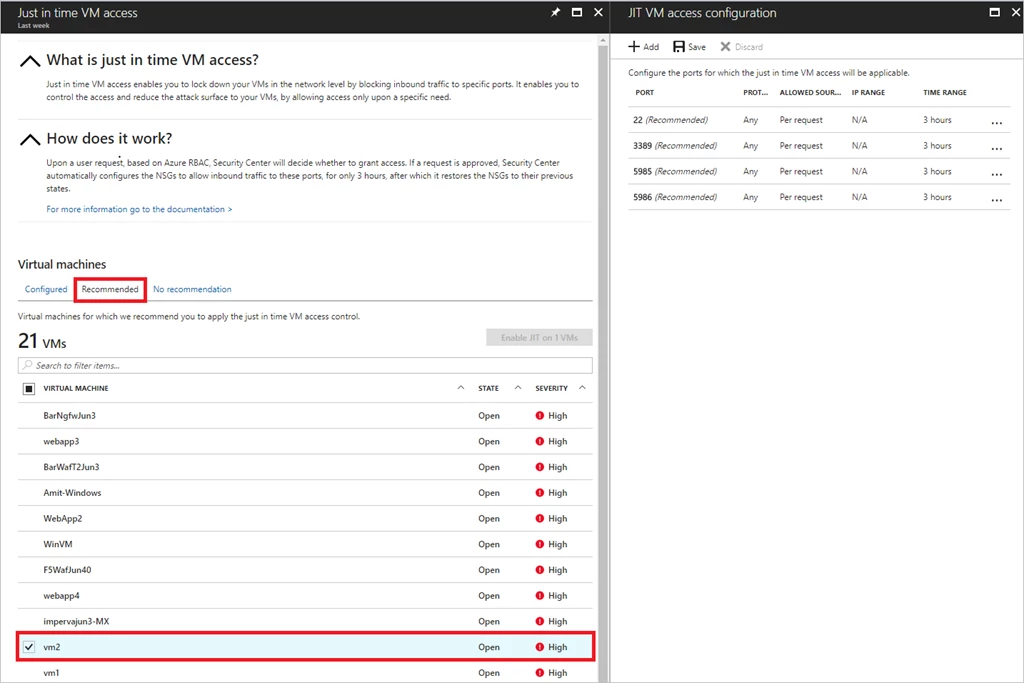
Enable JIT VM Access and Apply policies
In the JIT VM Access blade, administrators can easily enable JIT VM Access for all or select VMs. They can configure the policy that will determine the ports to be protected, allowed protocols, IP addresses from which these ports can be accessed, and the maximum time window for which a port can be opened. The policy will determine which options are available to users when they request access.
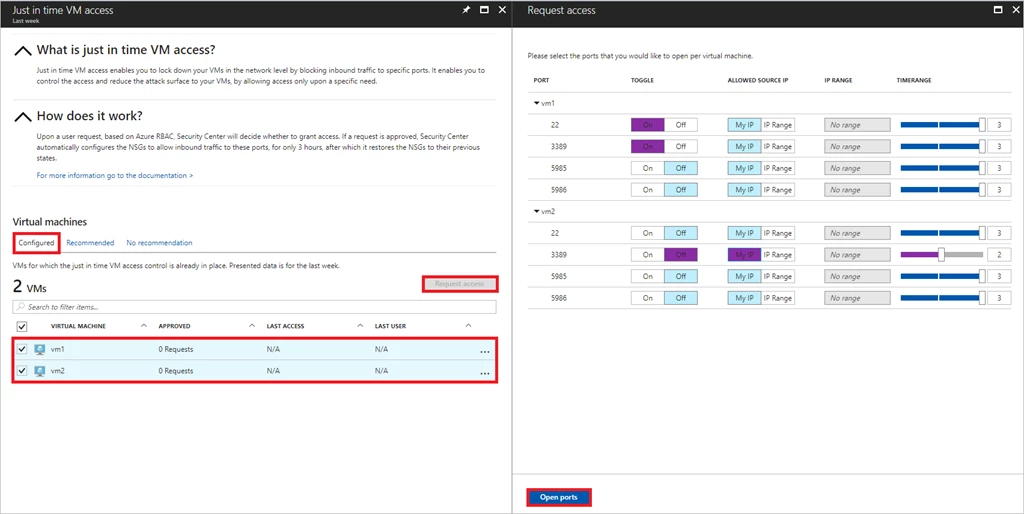
Requesting JIT Access to a VM
Anyone with the right permissions (based on Azure RBAC), can request access to a VM. Based on the JIT VM Access policy, they can select the ports they need access to, from which IPs, and for what timeframe. Access is automatically granted.
These new capabilities are available within the standard pricing tier of Azure Security Center, and you can try it for free for the first 60 days.
To learn more about JIT VM Access, watch the microlearning video or see the documentation.
