The Intelligent Edge brings the power of the cloud to mobile and Internet of Things (IoT) devices and demands security for trust. Azure IoT Edge is an implementation of the Intelligent Edge. Cloud-enabled computing at the edge means concentrating data, and therefore inherent value even if only momentarily. It also means moving tremendous value from the cloud to the edge in the form of intellectual property, algorithms, curated parameters, and value operations like policy enforcements, metering, and monetization. The Intelligent Edge is without a doubt a high-value bullseye to nefarious hacking and demands a high bar for security. Securing it requires a community effort and Microsoft, in alliance with many companies, is making great strides in this direction.
Why should an Intelligent Edge device demand the same rigor with which we secure the Microsoft Cloud? The Intelligent Edge device is physically accessible to potentially malicious actors, and therefore exposed to greater threats. These range from physical tampering to exploits from repurposing tools and knowledge from other disciplines.
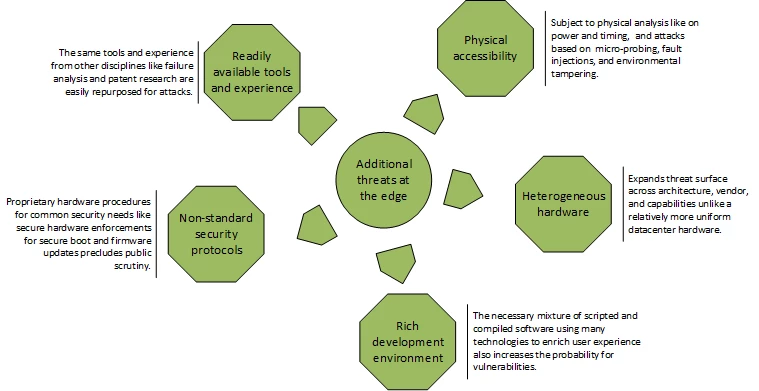
Figure 1: Additional threats to consider with cloud-enabled computing in Mobile and Internet of Things devices.
Knowing these threats exist creates awareness to foster the right solution. A careful security evaluation will reveal an optimal solution path that sometimes may need no more than diligence. This evaluation can happen in-house with sufficient expertise or farmed out to security auditors. Microsoft curates and maintains a list of security auditors in the Security Program for Azure IoT as a one stop shop evaluator.
With dependence on applications, deployments, and risk profiles, it stands to reason that the optimal security for the Intelligent Edge device should fall on a spectrum of protection rigor.
On one end of this spectrum Intelligent Edge devices are deployed in physically secured and access controlled facilities. Depending on security audit and risk assessment results, due diligence on security best practices might be sufficient for this deployment. The Internet of Things from the ground up offers some guidance on areas for diligence.
On the other end of the spectrum, Intelligent Edge devices can also be deployed harsher environments where they may be physically accessed without accountability. Examples may include smart building controllers for public buildings. Accessibility does not need to be localized to the installed device as a clever hacker may purchase a similar device for offline analysis and use the knowledge to attack installed devices. Intelligent Edge devices deployed in hostile environments therefore require security hardened hardware as the device itself is the last defense. Security hardened hardware offers resistance against attacks on keys and some offer trusted execution environments for higher trust.
There are several approaches to building security hardened hardware. For most, security hardening starts with appropriate processor architectures like those from ARM and Intel that add security features like secure enclaves. Silicon manufacturers then build on these processors to deliver hardened silicon chips that end up as the processing core of hardened Intelligent Edge devices. The Seven Properties of Highly Secure Devices offers a glimpse of necessary considerations for building hardened IoT devices. The hardening effort continues with firmware and software development best practices to adequately utilize the hardware security features. An ideal hardened Intelligent Edge device should lend itself to seamless secure provisioning, key management, authentication, authorization, and integrity protection of all content in memory and storage at all times.
Regardless of the approach, building secure hardware for hardened devices is difficult. It is for this reason Microsoft allies with domain masters of hardened hardware. Today we share progress with two of our secured silicon allies: NXP for LS1012 and Microchip for ATSAMA5D2, with both product families built using the ARM processor architecture with TrustZone® technology.
Firmware technology that provides the hardened hardware benefits to operating systems and applications is specialized and requires high expertise to develop. Today we share progress from one of our allies, Sequitur Labs, that has developed such firmware for both the LS1012 and ATSAMA5D2 secured hardware from NXP and Microchip respectively. Information on Sequitur’s solutions for hardened Azure IoT Edge devices is available from the Sequitur Labs website.
Microsoft is committed to making cloud-enabled edge computing a reality and regards security as a fundamental requirement for success. Microsoft is forging alliances to make Azure IoT Edge a secure Intelligent Edge platform that is operating system, processor architecture, and hardware agnostic.
Learn more about the Azure IoT Edge Intelligent Edge.
