This blog post was co-authored by Anupam Vij, Principal PM Manager & Syed Pasha, Principal Network Engineer, Azure Networking.
2020 was a year unlike any other. It brought major disruptions to both the physical and digital worlds, and these changes are also evident in the cyberthreat landscape. The prevalence of Distributed Denial-of-Service (DDoS) attacks in 2020 has grown more than 50 percent with increasing complexity and a significant increase in the volume of DDoS traffic.
With the COVID-19 pandemic, billions of people across the world have been confined to their home environments, working, learning, and even socializing remotely, and internet traffic has exploded. Now, DDoS attacks are one of the largest security concerns: the surges in internet traffic make it easier for attackers to launch DDoS attacks since they don’t have to generate as much traffic to bring down services. Cybercriminals can exploit huge traffic streams to launch DDoS attacks, which makes it harder to distinguish between legitimate and malicious traffic.
At Microsoft, the Azure DDoS Protection team protects every property in Microsoft and the entire Azure infrastructure. This past year, we continued to defend against DDoS attacks in the face of an ever-evolving cyber landscape and unprecedented challenges. In this review, we share trends and insights into DDoS attacks we observed and mitigated throughout 2020.
2020 DDoS attack trends
COVID-19 drove a sharp increase in DDoS attacks
Throughout the year, we mitigated an average of 500 multi-vector attacks on Azure resources a day. In total, we mitigated upwards of 200,000 multi-vector DDoS attacks against our global infrastructure.
The peak attack period was during March to April 2020 with the onset of the COVID-19 outbreak, as countries across the globe implemented lockdowns and stay-at-home measures. We mitigated around 800 to 1,000 multi-vector attacks per day, more than 50 percent higher than pre-COVID levels during the same time in previous years.
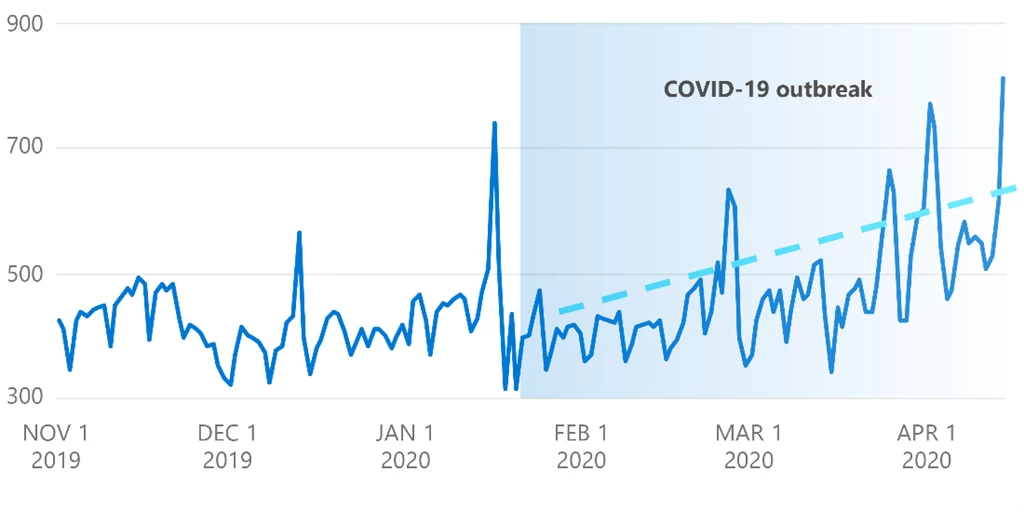
Number of DDoS attacks during COVID-19 outbreak
Short bursts of high-volume attacks
In 2020, we observed a trend towards high-volume attacks with shorter durations. Multi-vector attacks continued to be prevalent as well.
Attack bandwidth
The highest attack bandwidth volume we recorded on a single public IP was 1 tbps. In another instance, we mitigated a reflection attack of 1.6 tbps against multiple customers. These two attacks occurred during the peak attack period in March to April 2020.
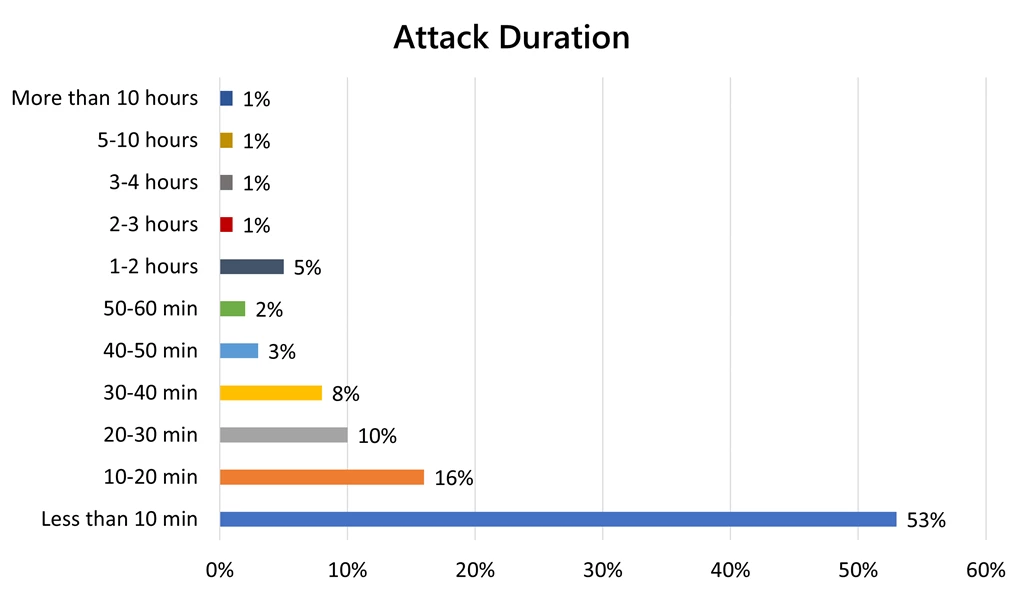
Attack duration
At the same time, we noticed that a majority of the attacks were short burst attacks. 87 percent of the DDoS attacks were under an hour, with 53 percent of the attacks under 10 minutes in duration.
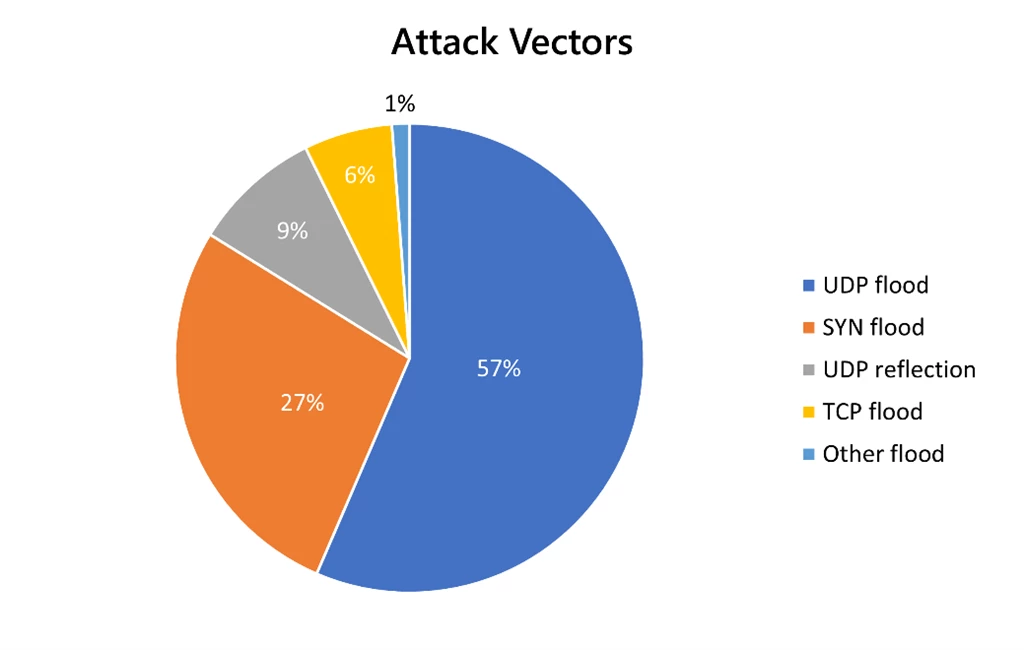
Increase in User Datagram Protocol (UDP) flood and reflection attacks
The top attack vectors were User Datagram Protocol (UDP) flood attacks followed by UDP reflection attacks and SYN flood attacks. The top reflection attacks were DNS, NTP, CLDAP, WSD, SSDP, memcached, and OpenVPN. This is due to the rise in IoT-connected devices, with vulnerable operating systems that are exploited to build botnets and launch reflection attacks.
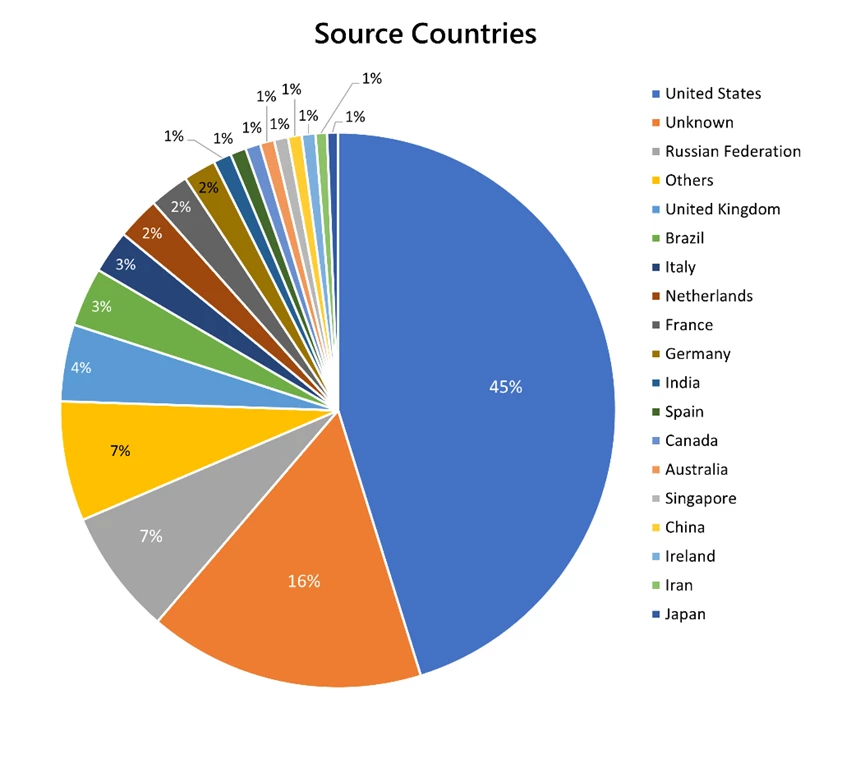
Wider range of attack sources and industries targeted
The top source countries to generate DDoS attacks were the United States and Russia, followed by the United Kingdom. Unknown sources indicate that the autonomous system numbers (ASNs) were either garbage, spoofed, or private ASNs that we could not translate.
Most attacks were concentrated in Europe, Asia, and the US as the financial services and gaming industries are especially vulnerable to DDoS attacks, although we also saw that a wider range of industries were just as susceptible.
New attacks observed
In 2020, we defended against three zero-day attack vectors:
Electrum DDoS malware
We detected Azure virtual machines (VMs) in Europe were exploited with this malware running on TCP port 50002 and were a target of DDoS attacks.
Trojan.ElectrumDoSMiner: Malwarebytes Labs Malwarebytes Labs Detections
DVR exploit reflection attack
This exploit specifically targeted Azure gaming customers on UDP port 37810. The amplification factor of this attack was 30 times, which means for every 1 byte of inbound traffic, 30 bytes was sent out in response. AMP-Research/Port 37810 – Dahua DVR IP Camera (refined payload) at master · Phenomite/AMP-Research · GitHub
MacOS vulnerability reflection attack with WSD
Mac OS vulnerability leads to DDoS attacks on UDP SRC Port -3283.
Low barriers to entry for DDoS attacks
The barriers to entry for DDoS attacks are becoming extremely low, and the easy availability of DDoS for-hire services makes it far easier and inexpensive to generate targeted DDoS attacks. At Microsoft, our research team found that in 2020, the average price of a one-hour DDoS attack was $48, a one-day attack was $134, and a one-month attack was $1,000.
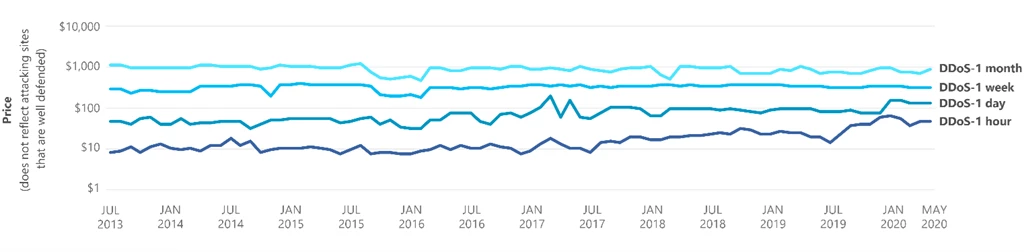
Trends and approximate average price for cybercriminal DDoS attack services
Sadly, it remains easy for cybercriminals to evade prosecution. The World Economic Forum’s Global Risks Report 2020 reveals that in the US, the chances of catching and prosecuting a cybercrime actor are almost nil (0.05 percent).
No DDoS protection means devastating consequences
DDoS attacks can incur extensive financial damage. At its core, companies would suffer immediate production and operational disruptions due to service downtime and absorb significant recovery costs. According to Gartner research, the average cost of downtime for a small to medium-sized business is $5,600 per minute. This leads to a huge loss in revenue and business opportunities, particularly if intellectual property is stolen.
Intangible costs due to reputation damage are especially devastating, as such attacks expose non-compliance and the failure to protect sensitive customer data, resulting in customer churn to competitors.
What’s next for 2021?
As we head into the new year, the threat of cyberattacks will continue to rise. We have observed that DDoS attacks are often used as smoke screens to cover up bigger network intrusions, which can wreak immense havoc on both businesses and users. There is also a new brewing national security threat: as healthcare organizations fight to cope with the growing demands of COVID-19, they are also becoming the prime target of cyber-attacks.
As the COVID-19 pandemic persists, the world will continue to be heavily dependent on digital services, and service availability and performance will become more important than ever. Given the evolving cyber-risks, it is all the more crucial for both business and users to develop a robust DDoS response strategy, and be proactive in protecting their resources.
Azure DDoS Protection Standard
Azure DDoS Protection Standard provides enhanced DDoS mitigation features to defend against DDoS attacks. It is automatically tuned to protect all public IP addresses in virtual networks. Protection is simple to enable on any new or existing virtual network and does not require any application or resource changes. You can even leverage the scale, capacity, and efficiency of Azure DDoS Protection Standard to protect your on-premises resources, by hosting a public IP address in Azure and redirecting the traffic to the backend origin to your on-premises environment.
Azure DDoS Protection Standard offers the following key benefits:
- Backed by the Microsoft global network: We bring massive DDoS mitigation capacity to every Azure region, scrubbing traffic at the Azure network edge before it can impact the availability of your services. If we identify that the attack volume is significant, we leverage the global scale of Azure to defend the attack from where it is originating.
- Cost protection: DDoS attacks often trigger the automatic scale-out of the service running in Azure. This could lead to a significant increase in network bandwidth, the scaling-up of the virtual machine count, or both. In the event of an attack, you can receive Azure credits for any scale-out of resources, so you do not have to worry about setting your application to auto-scale or paying the excess cost for egress data transfer.
- DDoS Rapid Response: During an active attack or after an attack, you can engage the DDoS Protection Rapid Response team for help with attack investigation and specialized support. The DDoS Protection Rapid Response team follows the Azure Rapid Response support model.
- Rich attack analytics: With DDoS attack analytics, you get access to detailed reports in five-minute increments during an attack, and a complete summary after the attack ends. You can also stream DDoS mitigation flow logs to an online or offline security information and event management (SIEM) system for near real-time monitoring during an attack. Review Azure DDoS Protection Standard reports and flow logs documentation to learn more. You can also connect logs to Azure Sentinel, view and analyze your data in workbooks, create custom alerts, and incorporate it into investigation processes. To connect to Azure Sentinel, see Connect to Azure Sentinel documentation.
Learn more about Azure DDoS Protection Standard
- Azure DDoS Protection Standard product page.
- Azure DDoS Protection Standard documentation.
- Azure DDoS Protection Standard reference architectures.
- DDoS Protection best practices.
- Azure DDoS Rapid Response.
- DDoS Protection Standard pricing and SLA.
