Azure Resource Manager, Management and Governance
Azure Security and Compliance Blueprint for PCI DSS-compliant Payment Processing environments
Posted on
2 min read
Today we are pleased to announce the general availability of a new Azure Security and Compliance Blueprint for PCI DSS-compliant Payment Processing environments, the only auditor reviewed, 100% automated solution for Payment Card Industry Data Security Standard – PCI DSS 3.2 technical controls. The architectural framework is designed to help companies deploy and operate a payment processing system, or credit card handling solution in Microsoft Azure. This automation solution will help customers adopt Azure solutions, showcasing a simple-to-understand reference architecture, and teach administrators how to deploy a secure and compliant workload while adhering to the PCI DSS compliance standard.
The solution was jointly developed with our partner Avyan Consulting, and subsequently reviewed by Coalfire, Microsoft’s PCI-DSS auditor. The PCI Compliance Review provides an independent, third-party review of the solution, and components that need to be addressed.
For a quick look at how this solution works, watch this five-minute video explaining, and demonstrating its deployment.
This automated architecture includes: Azure Application Gateway, Network Security Groups, Azure Active Directory, App Service Environment, OMS Log Analytics, Azure Key Vault, Azure SQL DB, Azure Load Balancer, Application Insights, Azure Web App, Azure Automation, Azure Runbooks, Azure DNS, Azure Virtual Network, Azure Virtual Machine, Azure Resource Group and Policies, Azure Blob Storage, Azure Active Directory access control (RBAC), and Azure Security Center.
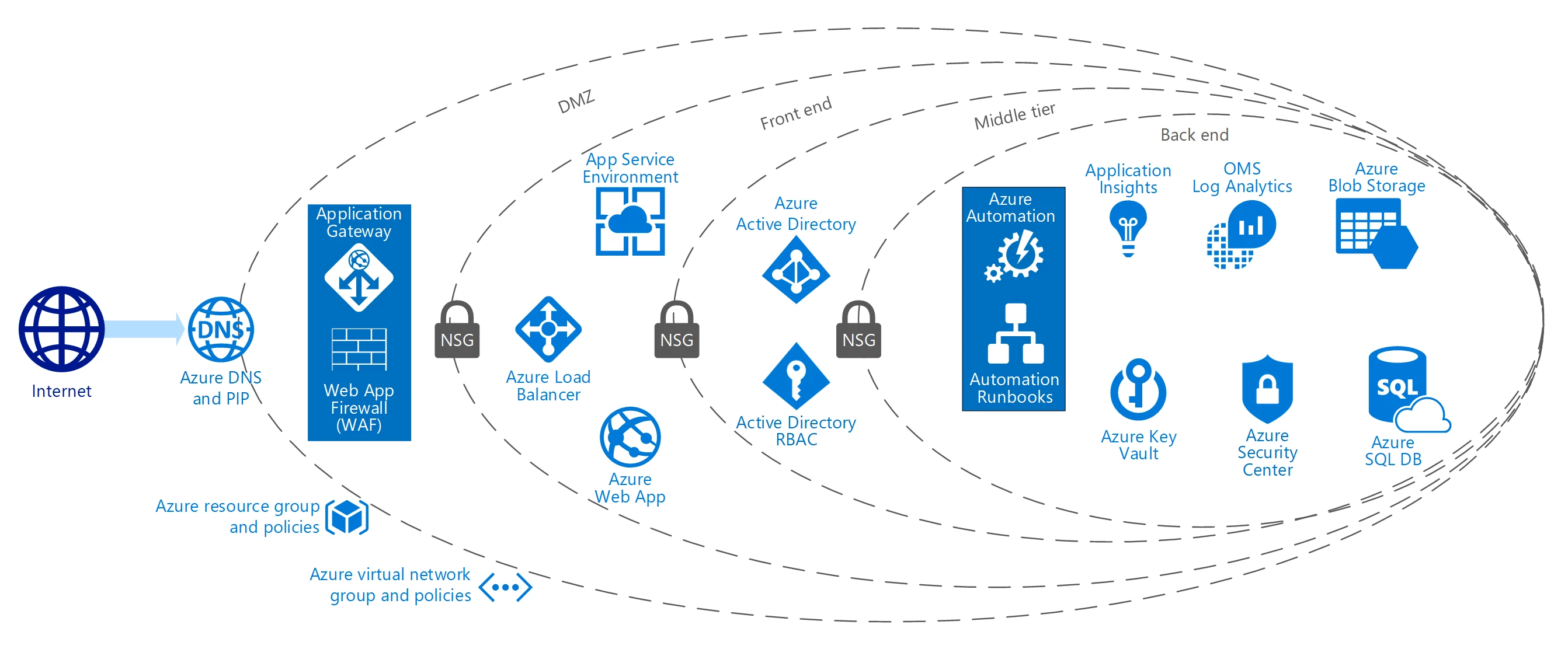
The foundational architecture is comprised of the following components:
- Architectural diagram. The diagram shows the reference architecture used for the Contoso Webstore solution.
- Deployment templates. In this deployment, Azure Resource Manager templates are used to automatically deploy the components of the architecture into Microsoft Azure by specifying configuration parameters during setup.
- Automated deployment scripts. These scripts help deploy the end-to-end solution. The scripts consist of:
- A module installation and global administrator setup script is used to install and verify that required PowerShell modules and global administrator roles are configured correctly.
- An installation PowerShell script is used to deploy the end-to-end solution, including security components built by the Azure SQL Database team.
- A sample customer responsibility PCI DSS 3.2 workbook. The workbook provides an explanation of how the solution can be used to achieve a compliant state in each of the 262 PCI DSS 3.2 controls. This workbook provides details on how a shared responsibility between Azure, and a customer can successfully be implemented.
- A PCI Compliance Review which outlines the topics necessary to build on the foundational architecture toward a full PCI-compliant business. The Coalfire’s review explores additional dimensions in advance of further solution design that will yield better results for an eventual PCI assessment.
- A customer ready threat model. This data flow diagram (DFD) and sample threat model for the Contoso Webstore the solution that provides detailed explanation on the solution boundaries and connections.
The deployed application illustrates the secure management of credit card data including card numbers, expiration dates, and CVC (Card Verification Check) numbers in a four-tier architecture that includes built-in security and compliance considerations and can be deployed as an end-to-end Azure solution.
To stay up-to-date with Azure Security and Compliance Blueprints and Azure Government, be sure to subscribe to our RSS feed and to receive emails by clicking “Subscribe by Email!” on the Azure Government Blog, additionally check back frequently to learn more about Azure automated foundational architectures.
To experience the power of Azure Government for your organization, sign up for an Azure Government Trial.