This blog post was co-authored by Sumeet Mittal, Senior Program Manager, Azure Networking.
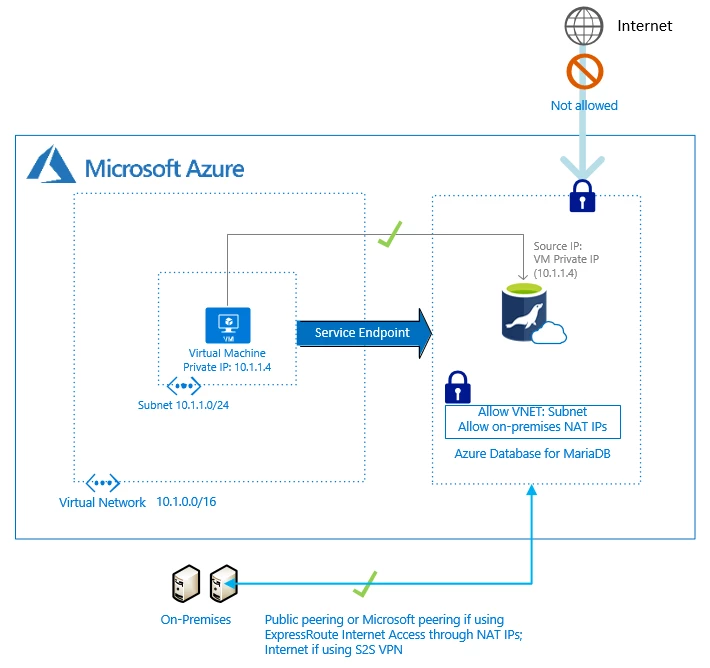
Ensure security and limit access to your MariaDB server with the virtual network (VNet) service endpoints now generally available for Azure Database for MariaDB. VNet service endpoints enable you to isolate connectivity to your logical server from a given subnet within your virtual network. The traffic to Azure Database for MariaDB from your VNet always stays within the Azure network. Preference for this direct route is over any specific ones that route Internet traffic through virtual appliances or on-premises.
There is no additional billing for virtual network access through VNet service endpoints. The current pricing model for Azure Database for MariaDB applies as is.
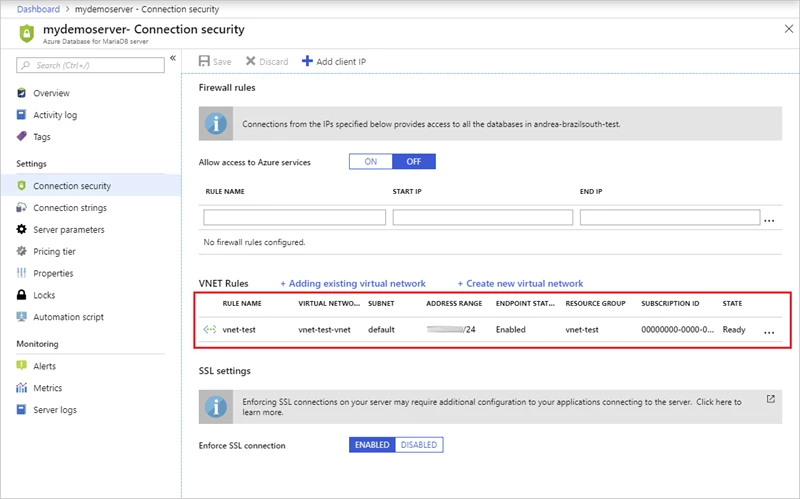
Using firewall rules and VNet service endpoints together
Turning on VNet service endpoints does not override firewall rules that you have provisioned on your Azure Database for MariaDB, both remain applicable.
VNet service endpoints don’t extend to on-premises. To allow access from on-premises, you can use firewall rules to limit connectivity only to your public (NAT) IPs.
To learn more about VNet protection view our documentation, “Use Virtual Network service endpoints and rules for Azure Database for MariDB.”
Turning on service endpoints for servers with pre-existing firewall rules
When you connect to your server with service endpoints turned on, the source IP of database connections switches to the private IP space of your VNet. Configuration is via the “Microsoft.Sql” shared service tag for all Azure Databases including Azure Database for MariaDB, MySQL, PostgreSQL, Azure SQL Database and Managed Instance, and Azure SQL Data Warehouse. If at the present time your server or database firewall rules allow specific Azure public IPs, then the connectivity breaks until you allow the given VNet/subnet by specifying it in the VNet firewall rules. To ensure connectivity, you can preemptively specify VNet firewall rules before turning on service endpoints by using the IgnoreMissingServiceEndpoint flag.
Support for ASE
As part of general availability, we support service endpoints for App Service Environment (ASE) subnets deployed into your virtual networks.
Next steps
- Get started with the service by creating your first Azure Database for MariaDB server using the Azure portal or Azure CLI.
- Learn how to configure VNet service endpoints for MariaDB using the Azure portal or Azure CLI.
- Reach us by emailing our team AskAzureDBforMariaDB@service.microsoft.com.
- File feature requests on UserVoice.
- Follow us on Twitter @AzureDBMariaDB to keep up with the latest features.
