Azure Security, Security, Thought leadership
Always learning, always adapting: Unpacking Azure’s continuous cybersecurity evolution
Posted on
5 min read
In the first blog of our series on Azure Security, we discussed our approach to tackling cloud vulnerabilities. Our second blog highlighted our use of variant hunting to detect patterns and enhance security across our services. The third blog in the series introduced game-changing architecture to improve built-in security. In this installment, we share our integrated response strategy which provides a continuous learning model, leveraging big data, to improve response, detections, preventative controls, and governance to measure and improve effectiveness.
Azure Security’s “Integrated Response” is the function of incorporating security risk mitigation strategies into a durable security program, seamlessly coordinating across federated security functions to learn, share, and adapt effective strategies to address top risks and threats at hyper-scale. As new threats and security risks emerge from a variety of sources, we address them by evaluating root causes and developing security controls as a learning feedback system. Our learnings from proactive and reactive analysis turn into product updates and threat intelligence enhancements in our security products.
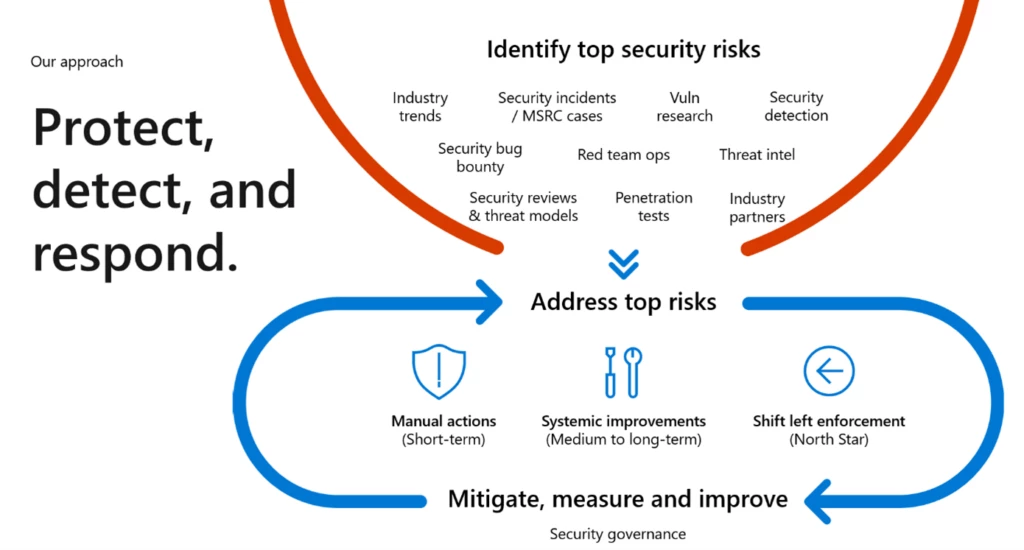
To maintain trust and accelerate response timelines, our closed-loop feedback cycle incorporates both internal and external risk drivers to improve each stage of our security response pipeline. Regularly reviewing security incidents is key to our ability to continuously improve our agility and response time to mitigate security risks for our customers. Each of our institutional processes, such as the Security LiveSite Review (SLR), Security Health Reviews (SHR), and our Security Operation Reviews (SOR) highlight and prioritize opportunities for improvement at all levels of Azure’s engineering organizations. Let’s dive into what each of these phases means and how they connect to each other.
Fostering a secure culture: A deeper look at Azure’s rigorous comprehensive protection and response
In a Cloud-First world, our customers trust us with their data, intellectual property, and critical business applications. To meet these expectations, we take a holistic approach to govern security and create an Integrated Response which incorporates a feedback cycle of identifying risk drivers and ensuring we drive the appropriate security controls to properly protect, detect and respond to threats. In addition, we ensure all products meet our security standards, such as Microsoft Cloud Security benchmarks. Here are the components of our Integrated Response:
First response on new threats: Microsoft Security Response Center (MSRC) and Cyber Defense Operations—Operating with an “Assume Breach” mindset, we have honed our ability to quickly and effectively respond to security incidents and drive rapid security mitigation and improvements. We engage customers, industry partners, and Microsoft product teams alike to work in this continuous feedback loop. MSRC is an integrated part of the defender community operating on the front line of security response for our Azure customers and for other products within Microsoft. For more than twenty years, MSRC has served to detect, respond, and recover from security vulnerabilities. Our decades of experience defending a wide range of technologies have shown us that continually learning and evolving, both inside and out, is essential to staying ahead of the ever-changing threat landscape.
Learn from every Security Incident: Security Live Site Reviews (SLR)—Following a security incident originating from MSRC or Red Team Operations, after the immediate remediation activity concludes, we prioritize conducting SLRs to drive 5-why analysis with product teams and executive leadership. Deeply focusing every single week from the Executive VP level down on deconstructing incidents down to their contributing root cause(s) drives Microsoft’s strategies on identifying process gaps, security control updates, and product improvements to improve Azure’s security posture. As discussed earlier in the series, throughout the investigation, we identify additional patterns beyond the specific incident to ensure we address beyond the symptom to the holistic solution. We track these repair items through all phases of our product and service development lifecycle including operations, engineering workflow, and security governance processes.
Ensure security culture and improve operational rigor: Security Operations Review (SOR)—To improve security for operational hygiene and foster a deep security culture, we conduct regular SOR. These reviews bring together executive leaders and product teams to share best practices and review behavioral trends, security control performance, and demonstrate a proven ability to maintain security SLAs as a proactive process.
Understand and reduce holistic security risk: Security Health and Risk Reviews (SHR)—Understanding the security risk of various requirements are an important element to maintaining a proper security-first mindset. We rationalize control performance and risk in the aggregate to conduct deep dives with product teams, creating a joint security-review conversation to learn and drive strategies to address emerging threats more broadly. The SHR provides a deep link to emerging risk by merging Azure Security perspectives with strategic product improvements to ensure we meet our customers’ needs now and into the future, providing confidence that we are investing in groundbreaking security innovation for tomorrow’s threats.
Govern effectively and drive security standards: Azure Security Governance—Always following a growth mindset, we drive security governance at scale across more than six thousand unique products, driving security baseline compliance, ensuring our customers have the right security capabilities integrated into our products before release as documented in Microsoft Cloud Security Benchmark (MCSB), which helps customers ensure their service configurations of Azure and other clouds meet the security specification defined in frameworks such as the Center for Internet Security, the National Institute of Standards and Technology, and the Payment Card Industry. MCSB provides an efficient alignment approach for customers to leverage as controls are pre-mapped to these industry benchmarks.
Internally, this governance function measures and provides insights and trends around behavioral and security control performance across our products, integrating new controls in SDL to stay relevant and mitigating emerging risks, while also empowering leaders with security optics to help them understand their security posture and drive security-first culture within their teams. We track security key performance Indicators (KPIs), at scale, and prioritize controls effective at mitigating threats based on real-world findings from root cause analysis of malicious attacks, RED Team discovery, MSRC findings, and industry incidents. Many are broadly identified as the industry’s best practices and requirements of Microsoft Security Policy (SDL/OSA) as well as regulatory compliance standards. These security KPIs are measured with Microsoft security technologies which have expanded and matured over time.
Embracing continual learning: How Azure’s Integrated Response strategy innovates security for a changing world
Our Integrated Response strategy provides a holistic approach to incorporate risk drivers with security controls and ensure products meet Microsoft Cloud Security benchmarks, leveraging measurement at scale and governance to identify and mitigate risks end-to-end. Microsoft combines our strong internal security response program with a broad and diverse ecosystem of security partners to supply world-class protection for billions of customers and the broader market. We recognize that security is a culmination of product and process and that Defense-in-Depth is a layered approach to both. As such, we embrace feedback and iterate improvements by measuring for effect. Our decades of experience defending a wide range of technologies have shown us that continually learning and evolving, both inside and out, is essential to staying ahead of the ever-changing threat landscape.
Learn more
- Read additional blogs in this series to learn how Azure leverages cloud variant hunting, secure multitenancy, Confidential Compute, and Rust to layer protection throughout every phase of design, development, and deployment.
- Learn more about the out-of-the-box capabilities embedded in our platforms.
- Learn more about how Microsoft Azure can help strengthen your security posture.