Azure Firewall
Protect your Azure Virtual Network resources with cloud-native network security.
Firewall security to help protect your digital assets
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. The stateful firewall service has built-in high availability and unrestricted cloud scalability to help you create, enforce, and log application and network connectivity policies across subscriptions and virtual networks.
Threat intelligence–based filtering
Enable real-time alerts and deny traffic from/to known malicious IP addresses and domains.
Deploy and scale in minutes
Simplify deployment and management of your network security with a scalable and highly available cloud native firewall.
Full visibility and protection
Transport Layer Security (TLS) inspection prevents malware from being transmitted through encrypted connections.
Unified management
Centrally manage security across all virtual networks with a common set of network and application rules.
Strengthen your network security posture
Get advanced threat protection that meets the needs of highly sensitive and regulated environments. Azure Firewall taps into real-time security signals from a wide range of sources using Microsoft threat intelligence to guard against evolving threats and zero-day vulnerabilities.


Deploy a stateful firewall in minutes
Enable turnkey firewall security capabilities in Azure Virtual Network to control and log access to apps and resources. Azure Firewall supports filtering for both inbound and outbound traffic, internal spoke-to-spoke connections, and hybrid connections through Azure VPN and ExpressRoute gateways.
Prevent malware and viruses from spreading
Azure Firewall decrypts outbound traffic, performs required security checks, and then encrypts the traffic to the destination. It works in conjunction with URL filtering and web categories by letting administrators allow or deny user access to website categories such as gambling or social media.


Inspect traffic in real time
The intrusion detection and prevention system (IDPS) capability uses signatures to continuously monitor activities, generate alerts, log information, and optionally attempt to block the attack. It can detect attacks in all ports and protocols for non-encrypted traffic. Encrypted traffic utilizes the TLS inspection capability for decryption.
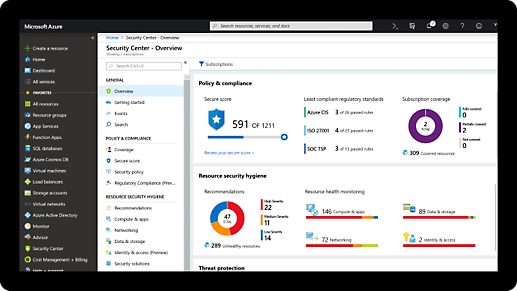
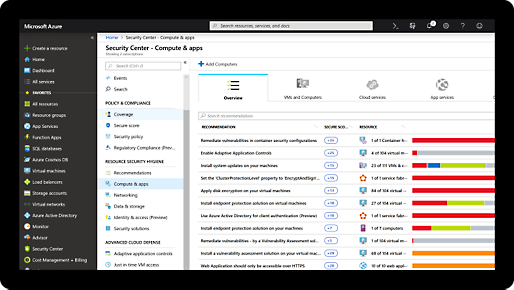
Comprehensive security and compliance, built in
-
Microsoft invests more than USD 1 billion annually on cybersecurity research and development.


-
We employ more than 3,500 security experts who are dedicated to data security and privacy.
-
Azure has more certifications than any other cloud provider. View the comprehensive list.
-
Azure Firewall pricing
Setup is easy, and billing comprises a fixed per-hour consumption rate and variable fees based on traffic. There are no upfront costs or termination fees—pay only for what you use.
Get started with an Azure free account
1

Start free. Get USD 200 credit to use within 30 days. While you have your credit, get free amounts of many of our most popular services, plus free amounts of 55+ other services that are always free.
2

After your credit, move to pay as you go to keep building with the same free services. Pay only if you use more than your free monthly amounts.
3

Trusted by companies of all sizes
"Microsoft has created a single ecosystem that incorporates the scalability and security of Azure, Microsoft 365, and Dynamics 365, and which will grow synergistically over time."
Joe Ferlisi, CIO and Chief Security Officer, Rockefeller Capital Management

"Azure Security Center is one of the most critical security tools managing the Azure ecosystem at NCR. With its single pane of glass, we get an overview of security across our Azure cloud deployments in real time."
Isidro Rodriguez, Head of Digital Transformation, SaaS Operations, NCR

a
"As we looked at other vendors and platforms, we realized that it was a no-brainer. Microsoft offers the cohesive solution we need. Everything it brings to the table fits beautifully with our direction. It has become an outstanding support for us."
Michael Della Villa, CIO and Head of Shared Services, MVP Health Care

i
"[With Azure] Virtual WAN and Azure Firewall, we can see all traffic moving across our networks, control it with Azure Firewall, and feed the logs into Azure Sentinel for our security operations center. This definitely helps us reduce risk; seeing is knowing."
Barry King, Cloud Infrastructure Chief Technology Officer, Costain

1
"We were struggling with the scripting of multiple technologies… and the unified, automated Azure infrastructure really presented itself as the best way for us to improve efficiency moving forward."
Igor van Haren, Lead Architect, VECOZO

.
"Understanding the inner workings of a firewall is not our expertise, and with Azure Firewall Premium, it doesn't have to be. We use Azure Firewall Premium to protect Dematic and our customers around the clock, and we can depend on it."
Brandon Bates, Principal Architect, Dematic

Azure Firewall resources and documentation
Related services
Frequently asked questions about Azure Firewall
-
Set up Azure Firewall in the Azure portal or with PowerShell, REST API, or templates. Read a tutorial for step-by-step instructions.
-
Yes. Azure Firewall supports inbound and outbound filtering. Inbound protection is typically used for non-HTTP/S protocols such as RDP, SSH, and FTP protocols. For the best inbound HTTP/S protection, use a web application firewall such as Azure Web Application Firewall (WAF).
-
Azure Firewall is integrated with Azure Monitor for viewing and analyzing firewall logs. Logs can be sent to Log Analytics, Azure Storage, or Event Hubs. They can be analyzed in Log Analytics or by different tools such as Excel and Power BI. For more information, see Tutorial: Monitor Azure Firewall logs.
-
Yes, Azure Firewall Premium provides advanced threat protection that meets the needs of highly sensitive and regulated environments, such as the financial services and healthcare industries. A signature-based IDPS looks for specific patterns to rapidly detect attacks. These patterns can include byte sequences in network traffic or known malicious instruction sequences used by malware. There are more than 58,000 signatures in more than 50 categories which are updated in real time to protect against new and emerging exploits. The exploit categories include malware, phishing, coin mining, and Trojan attacks.
-
Yes, Azure Firewall allows you to inspect traffic destined for a private endpoint. Private endpoints enable Azure resources deployed in a virtual network to communicate privately with private link resources. You may need to inspect or block traffic from clients to the services exposed via private endpoints using Azure Firewall.
-
For secure access to platform services, we recommend service endpoints. You can choose to enable service endpoints in the Azure Firewall subnet and disable them on the connected spoke virtual networks. This way you benefit from both features—service endpoint security and central logging for all traffic.







