Save costs and operate more efficiently with managed domain services
Microsoft Entra Domain Services (formerly Azure Active Directory Domain Services), part of Microsoft Entra, enables you to use managed domain services—such as Windows Domain Join, group policy, LDAP, and Kerberos authentication—without having to deploy, manage, or patch domain controllers.
Access to managed domain services such as Windows Domain Join, group policy, LDAP, and Kerberos authentication
Ability to join Azure virtual machines to a managed domain without domain controllers
Simple sign-in to apps connected to your managed domain with Microsoft Entra ID (formerly Azure AD) credentials
Lift-and-shift migration of legacy applications from your on-premises environment to a managed domain
Increase operational efficiency
Enable managed domain services for virtual machines and directory-aware applications deployed in Azure with a click of a button. Reduce operational and maintenance costs associated with managing identity infrastructure for your virtual machines and legacy applications.


Run legacy applications in the cloud
Easily migrate on-premises apps to a managed domain. Streamline management of all applications from your legacy, directory-aware apps alongside your modern cloud apps with a single identity solution.
Rely on a managed, highly available service
Domain Services includes multiple domain controllers to provide high availability for your managed domain. Ensure business continuity with guaranteed service uptime and resilience to failures.


Unify your identity infrastructure management
Simplify the experience of managing and securing your entire identity infrastructure including Domain Services with the Microsoft Entra admin center.
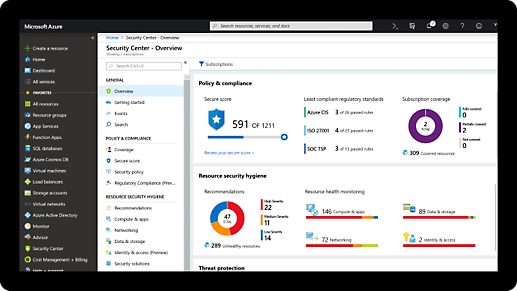
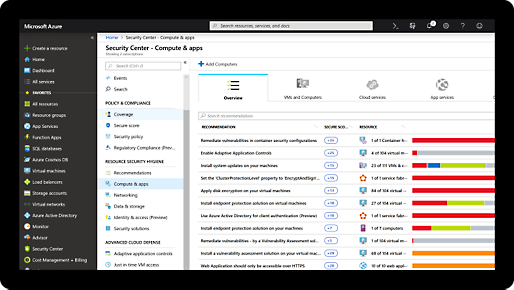
Comprehensive security and compliance, built in
-
Microsoft invests more than USD1 billion annually on cybersecurity research and development.


-
We employ more than 3,500 security experts who are dedicated to data security and privacy.

Pricing for Microsoft Entra Domain Services
Domain Services offers built-in conditional access and security threat intelligence for all your users. Usage is charged per hour, based on the SKU selected by the tenant owner. Explore pricing options to find the version that fits your needs.
Get started with an Azure free account
1

2

After your credit, move to pay as you go to keep building with the same free services. Pay only if you use more than your free monthly amounts.
3

Microsoft Entra Domain Services resources and documentation
Code samples
Identity services documentation
Frequently asked questions about Microsoft Entra Domain Service
-
Domain Services is a part of Microsoft Entra, the new product family for multicloud identity and access solutions.
-
No. You can create a single managed domain serviced by Microsoft Entra Domain Services for a single Microsoft Entra tenant.
-
Yes. Domain Services can be enabled in an Azure Resource Manager virtual network. Classic Azure virtual networks are no longer available when you create a managed domain.
-
No. Guest users invited to your Microsoft Entra tenant using the Microsoft Entra B2B invite process are synchronized to your Domain Services managed domain. However, as passwords for these users aren't stored in your Microsoft Entra tenant,Domain Services has no way to synchronize NTLM and Kerberos hashes for these users to your managed domain, so they can't sign in or join computers to the managed domain.
-
Yes. Each Domain Services managed domain includes two domain controllers. You don't manage or connect to these domain controllers—they're part of the managed service. If you deploy Domain Services into a region that supports availability zones, the domain controllers are distributed across zones. In regions that don't support availability zones, the domain controllers are distributed across availability sets. Learn more about availability options for virtual machines in Azure.
-
Changes made in your Microsoft Entra tenant using either the Microsoft Entra admin center or PowerShell are automatically synchronized to your managed domain. This synchronization process runs in the background. There's no defined time period for this synchronization to complete all the object changes.
-
No. Once you've enabled a Domain Services managed domain, the service is available within your selected virtual network until you delete the managed domain. There's no way to pause the service. Billing continues on an hourly basis until you delete the managed domain.

