How do you go about answering those perplexing questions such as what secure hardware to use? How do I gauge the level of security? How much security do I really need and hence how much premium should I place on secure hardware? We’ve published a new whitepaper to shed light on this subject matter.
In our relentless commitment to securing IoT deployments worldwide, we continue to raise awareness to the true nature of security—that it is a journey and never an endpoint. Challenges emerge, vulnerabilities evolve, and solutions age thereby triggering the need for renewal if you are to maintain a desired level of security.
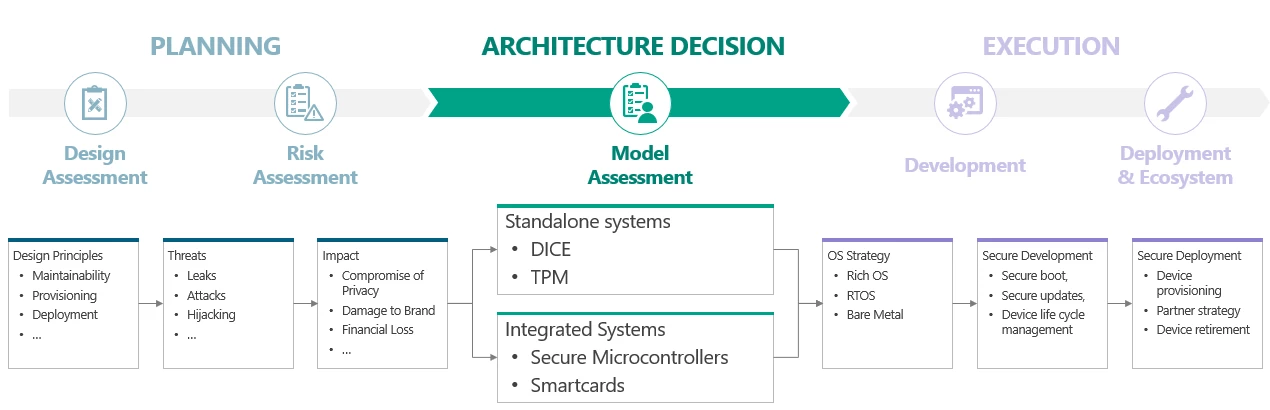
Securing your deployment as desired comprises planning, architecture, and execution main phases. For IoT, these are further broken down into sub-phases to include design assessment, risk assessment, model assessment, development, and deployment as shown in Figure 1. The decision process at each phase is equally important, the process must take all other phases into consideration for optimal efficacy. This is especially true when choosing the right secure hardware, also known as secure silicon or Hardware Secure Module(HSM), to secure an IoT deployment.
Figure 1: The IoT Security Lifecycle
Choosing the right secure hardware for securing an IoT deployment requires that you understand what you are protecting against (risk assessment), which drives part of the requirements for the choice. The other part of the requirements entails logistical considerations like provisioning, deployment and retirement, as well as tactical considerations like maintainability. These requirements in turn drive architecture and development strategies which then allow you to make the optimal choice of secure hardware. While this prescription is not an absolute guarantee for security, following these guidelines allows one to comfortably claim due diligence for a holistic consideration towards the choice of the right secure hardware, and hence the greatest chance of achieving security goals.
The choice itself requires knowledge of available secure hardware options as well as corresponding attributes such as protocol and standards compliances. We’ve developed a whitepaper, The Right Secure Hardware for Your IoT Deployment, to highlight the secure hardware decision process. This whitepaper educates on the Architecture Decision phase of the IoT security lifecycle. It comprises the second whitepaper for the IoT security lifecycle decision making series following previously published whitepaper, Evaluating Your IoT Security, which offers education on the Planning phase.
Download IoT Security Lifecycle whitepaper series:What strategies do you use in selecting the right hardware to secure your IoT devices and deployment? We invite you to share your thoughts in comments below.
Whitepaper: Selecting the right secure hardware for your IoT deployment
How do you go about answering those perplexing questions such as what secure hardware to use? How do I gauge the level of security? How much security do I really need and hence how much premium should I place on secure hardware? We’ve published a new whitepaper to shed light on this subject matter.