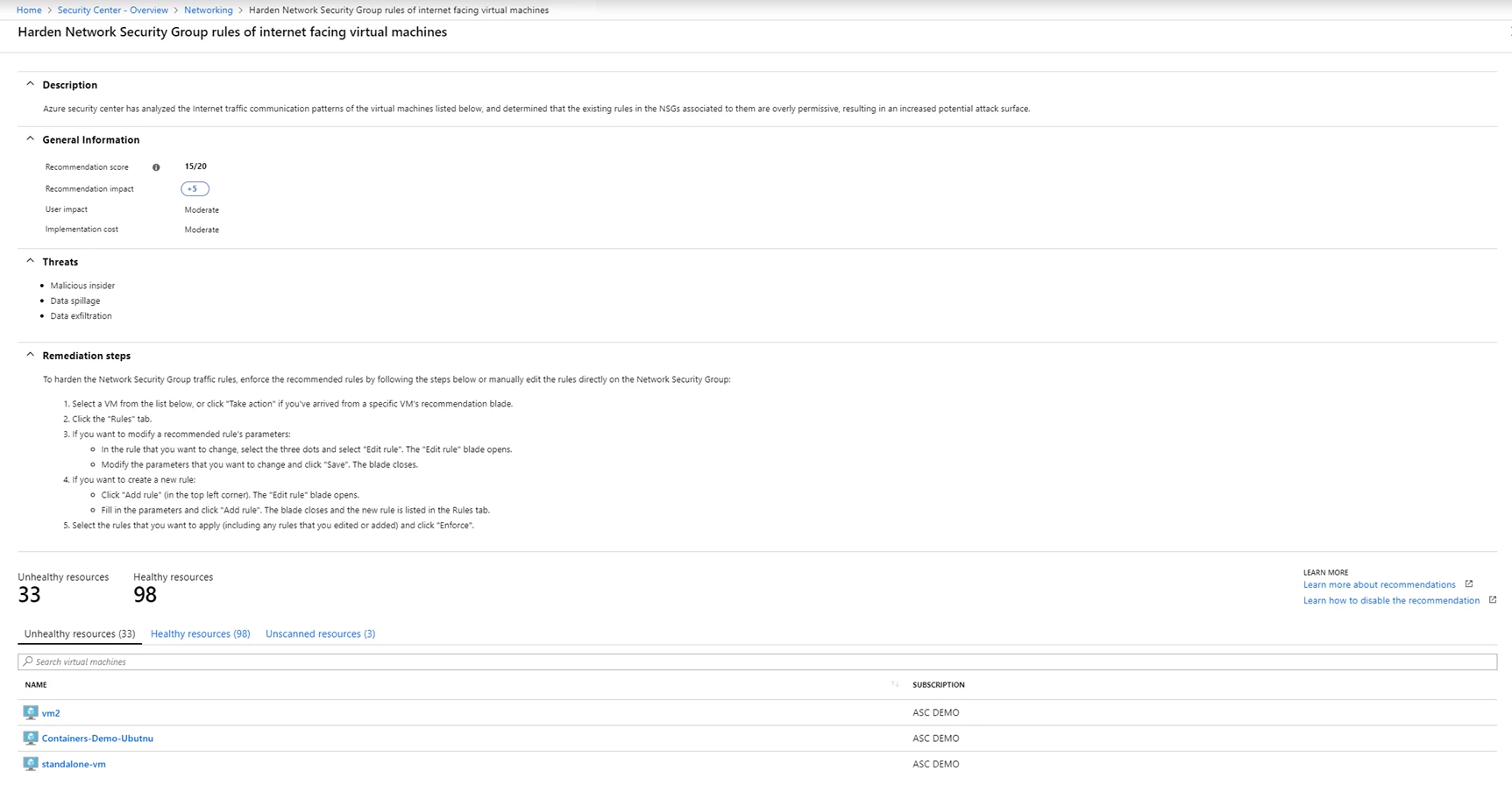
One of the biggest attack surfaces for workloads running in the public cloud is connections to and from the public internet. Our customers find it hard to know which network security group (NSG) rules should be in place to make sure that Azure workloads are only available to required source ranges.
With the release of the adaptive network hardening feature, Azure Security Center learns the network traffic and connectivity patterns of your Azure workloads and provides you with NSG rule recommendations for your internet-facing virtual machines. This helps you better configure your network access policies and limit your exposure to attacks, even when there are already filtering rules in place, as the filtering rules may be too permissive or the actual traffic flowing through the NSG is a subset of the NSG rules defined. In this case, you can further improve the security posture by hardening the NSG rules, based on the actual traffic patterns.
Azure Security Center uses machine learning to fully automate this process, including an automated enforcement mechanism, enabling customers to better protect their internet-facing virtual machines with only a few clicks. These recommendations also use Microsoft’s extensive threat intelligence reports to make sure that known bad actors are blocked.
Additionally, Azure Security Center will alert users when traffic is identified from IPs that aren’t recommended by the algorithm.
For example, let’s say the existing NSG rule is to allow traffic from 140.20.30.10/24 on port 22. Based on the analysis, the adaptive network hardening’s recommendation would be to narrow the range and allow traffic from 140.23.30.10/29 – which is a narrower IP range, and deny all other traffic to that port.
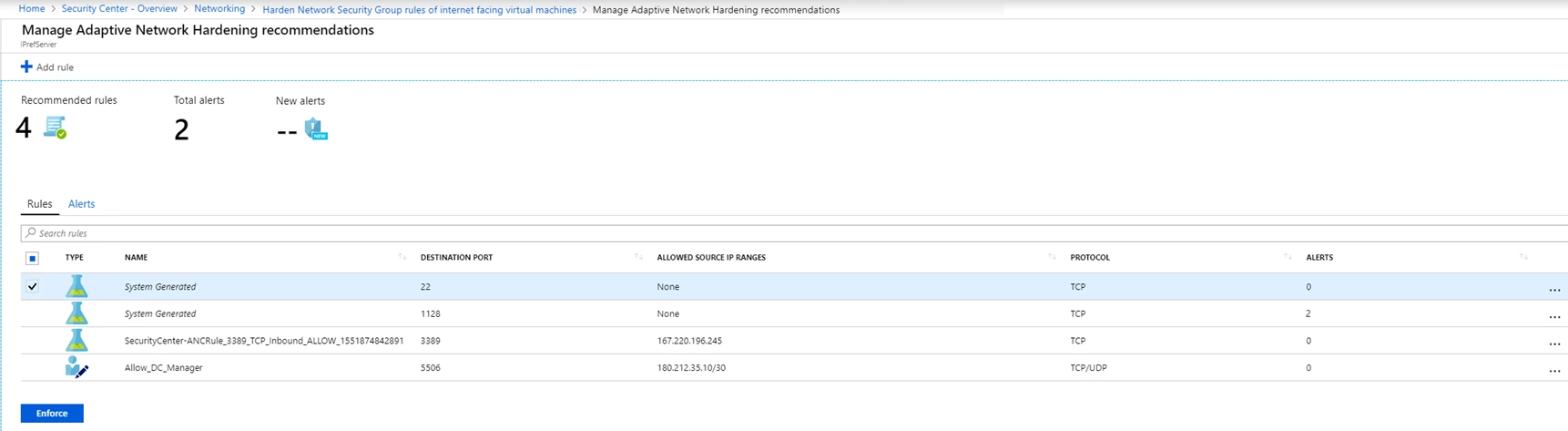
Adaptive network hardening is available within the standard pricing tier of Azure Security Center. Learn more about how adaptive network hardening provides recommendations to further harden NSG rules in the documentation.
