As a cloud service provider, we understand the importance of maintaining the integrity and confidentiality of customer data. To continue to help you maximize your data security and privacy, we are announcing Customer Lockbox for Microsoft Azure. It is a service integrated into Azure portal that gives you explicit control in the very rare instance when a Microsoft Support Engineer may need access to your data to resolve an issue.
There are very few instances, such as a debugging remote access issue, where a Microsoft Support Engineer requires elevated permissions to resolve this issue. In such cases, Microsoft engineers use just-in-time access service that provides limited, time-bound authorization with access limited to the service. While Microsoft has always obtained customer consent for access, Customer Lockbox now gives customers the ability to review and approve or deny such requests from Azure Portal. Until the request is approved, Microsoft Support Engineer will not be granted access.
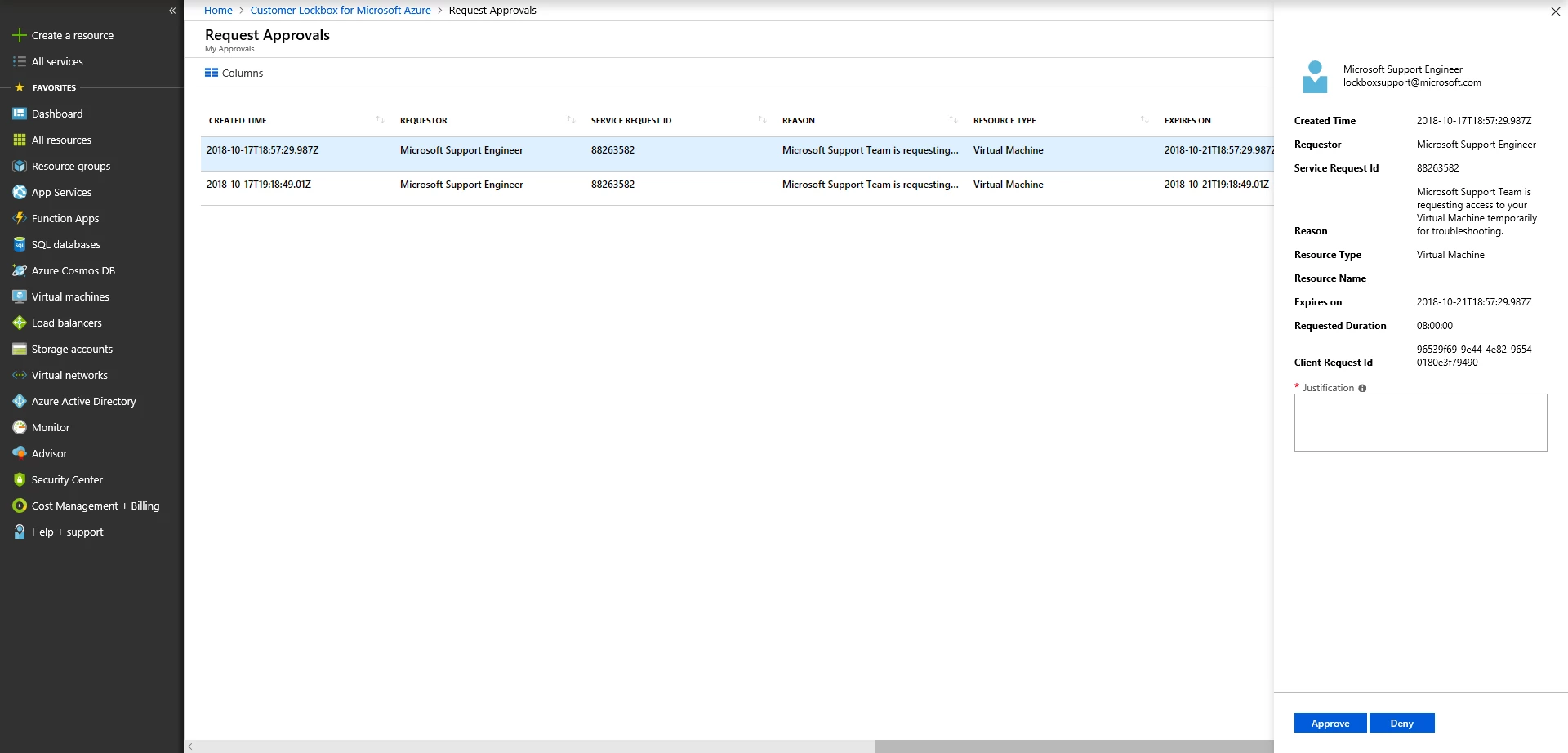
The entire process is audited so customers maintain full visibility and control. All Customer Lockbox activity will be available in Azure Portal. If you are using Azure Security Center, the VM agent that you have installed on your virtual machines can provide logs on activities carried out on these VMs. For further analysis, these logs can also be easily integrated to security monitoring and reporting systems. While Customer Lockbox will be in the portal by default, during public preview, you will have to take a few steps to enable the feature.
Enable Customer Lockbox for your tenant
During public preview phase, customers will need to opt-in to enable this feature. Follow steps detailed below to enable customer lockbox for your Tenant. This will enable Customer Lockbox service to send email notifications to approvers and route requests for approval to Customer Lockbox blade in Azure portal.
Note: You must be in Global Administrator role to enable customer lockbox for your tenant.
1. Launch Azure PowerShell in Administrator Mode and execute the following:
2. Install-Module -Name AzureRM
3. Import-Module AzureRm.profile
4. Login-AzureRmAccount
When prompted, login using Global Administrator credentials.
5. Select-AzureRmSubscription –TenantID ” xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx” –SubscriptionID “xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”
TenantID: Enter the Directory ID (GUID) of your Azure Active Directory Tenant. Refer to the ‘Get TenantID’ section if you need more details on how to get TenantID.
SubscriptionID = Enter any SubscriptionID within your Tenant.
6. New-AzureRmADServicePrincipal –ApplicationID a0551534-cfc9-4e1f-9a7a-65093b32bb38
7. New-AzureRmADServicePrincipal –ApplicationID 01fc33a7-78ba-4d2f-a4b7-768e336e890e
This command enables Customer Lockbox Service Principal (SPN) for your tenant. Please do not change the ApplicationID.
You can verify that the provisioning is completed using the following command:
8. Get-AzureRmADServicePrincipal | ? { $_.applicationID -match “a0551534-cfc9-4e1f-9a7a-65093b32bb38”}
Get-AzureRmADServicePrincipal | ? { $_.applicationID -match “01fc33a7-78ba-4d2f-a4b7-768e336e890e”}
This should list ApplicationID “a0551534-cfc9-4e1f-9a7a-65093b32bb38” with Application Name “Azure Lockbox” and ApplicationID “01fc33a7-78ba-4d2f-a4b7-768e336e890e” with Application Name “MS-PIM.”
Customer Lockbox for Azure is now in public preview for Azure Compute workloads (Azure Virtual Machines). This feature will replace the existing approval process followed by the Microsoft support team for their support ticket workflow.
For more information on how Microsoft protects the privacy and integrity of customer data, visit Microsoft’s trusted cloud page.
Frequently asked questions
Who can approve a Customer Lockbox for Azure Request?
Users who are assigned with ‘Owner’ role permission for the Azure subscription is notified about a pending lockbox request and can approve the request. Read more information on Azure RBAC roles.
I received a notification in an email about a Pending Customer Lockbox request for approval, what is my next step?
Please visit Azure Portal and search for ‘Customer Lockbox for Microsoft Azure’, if you select ‘Customer Lockbox for Microsoft Azure’ blade, then you will see a pending request for your review. We are working on creating a direct link to the blade.
