Azure App Service, Azure Security Center, Security, Web
Azure Security Center can identify attacks targeting Azure App Service applications
Posted on
2 min read
One of Azure’s most popular service is App Service which enables customers to build and host web applications in the programming language of their choice without managing infrastructure. App Service offers auto-scaling and high availability, supports both Windows and Linux. It also supports automated deployments from GitHub, Visual Studio Team Services or any Git repository. At RSA, we announced that Azure Security Center leverages the scale of the cloud to identify attacks targeting App Service applications.
Vulnerabilities in web applications are frequently exploited by attackers, as they are a common and dynamic interface for almost every organization on the internet. Requests to applications running on top of App Service go through several gateways deployed in Azure datacenters around the world, responsible for routing each request to its corresponding application. Recently, Security Center and App Service embarked on a journey aimed at building a security offering to support App Service customers.
By leveraging the visibility that Azure has as cloud provider, Security Center analyzes App Service internal logs to identify attack methodology on multiple targets. For example, attempts to access the same Uniform Resource Identifiers (URI) on various web sites. This type of attacker typically exhibits a pattern of crawling to the same web page on multiple web sites, searching for a particularly vulnerable page or plugin. Security Center can detect and alert on behavior that may pass through Web Application Firewalls (WAF) instruments.
WAFs are a widespread protection mechanism employed to protect web applications. WAFs typically perform rule-based string analysis to the requested URIs, and successfully identify prevalent attacks. Examples include: SQL injection, cross-site scripting and other HTTP violations. While successfully mitigating known attacks, the rule-based approach fails to keep up with the rate of new vulnerabilities.
Security Center leverages the scale of the cloud to identify attacks on App Service applications while focusing on emerging attacks, as attackers are on the reconnaissance phase, scanning to identify vulnerabilities across multiple websites, hosted on Azure. Security Center’s new capabilities include analytics and machine learning models that cover all interfaces allowing customers to interact with their applications, whether it’s over HTTP or through one of the management methods. Moreover, as a first-party service in Azure, Security Center is also in a unique position to offer host-based security analytics covering the underlying compute nodes for this PaaS. Thus, Security Center can detect attacks against web applications that has already been exploited.
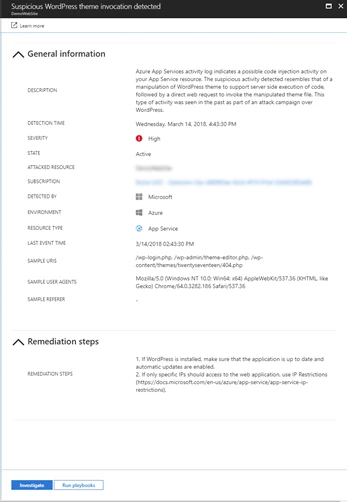
Managing web applications can expose your workload to security vulnerabilities, which needs to be thought of and address. These vulnerabilities can lead to your web applications exploited and attackers gaining a footprint in your workload. Security Center offers a set of recommendations both for windows and Linux web applications with security best practices that will help guide you of the process of configuring your web applications correctly.
A public preview of this feature is available now on the Standard and Trial tiers of Security Center at no additional cost.
To learn more about Security Center threat detection, see the documentation or review case studies from security researchers about how Security Center detects SQL Brute Force attacks, Bitcoin mining, DDoS attack using cyber threat intelligence, and good applications being used maliciously.