Last year we committed to making it easier for customers to run their services in the public cloud. As we meet with customers from across the world a common concern voiced are the challenges of managing an ever-growing portfolio of cloud-based mission critical applications. In addition to our focus on the fundamental pillars of Security, Performance, Monitoring, Connectivity, Availability, and growing a rich partner Ecosystem, we are equally focused on simplifying the overall management of our networking services and providing you more choices to run your services in a secure and compliant manner. Here is an overview of announcements we are making at Ignite.
Security
Virtual Network Service Endpoints
Azures services such as Storage and SQL have Internet facing IP addresses. Many customers would prefer that their Azure services not be exposed directly to the Internet. Virtual Network Service Endpoints extend your virtual network private address space and the identity of your VNet to Azure services. You can restrict Azure resources to only be accessed from your VNet and not via the Internet. A single click enables VNet service endpoints on a subnet. Service Endpoints are available in preview for Azure Storage and Azure SQL Database in select regions. We will be including additional Azure services to VNet Service Endpoints in the coming months. For more information see VNet Service Endpoints.
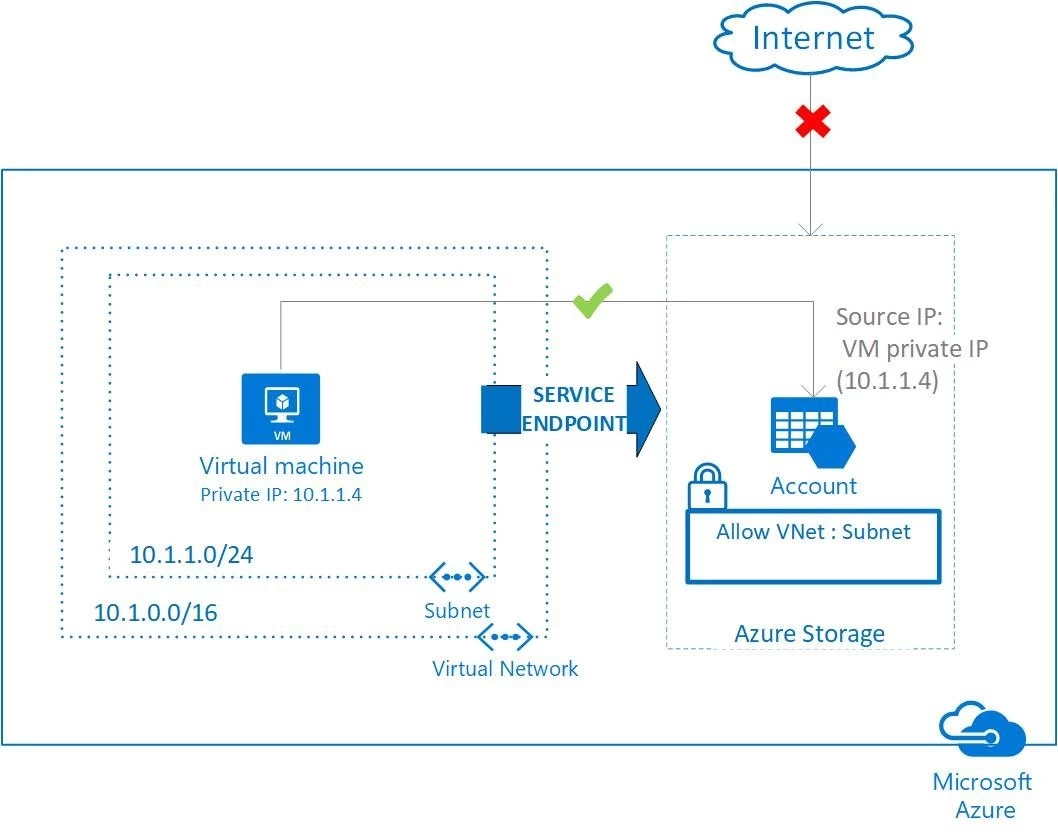
VNet Service Endpoints restricts Azure services to be accessed only from a VNet
DDoS Protection for Virtual Networks
As the types and sophistication of network attacks increase, Azure provides customers with solutions to protect the security and availability of your applications. Azure’s basic DDoS Protection automatically provides real-time mitigation to protect Microsoft’s cloud using the scale and capacity of our globally deployed DDoS infrastructure. However, your application may require finer-grained policies.
The new Azure DDoS Protection service protects your application from targeted DDoS attacks and brings additional configuration, alerting and telemetry. Continuous and automatic tuning protects your publicly accessible resources in a VNet. By profiling your application’s normal traffic patterns using sophisticated machine learning algorithms to intelligently detect malicious traffic, targeted DDoS attacks are mitigated. Seamless integration with Azure Monitor provides detailed telemetry and alerting.

Azure DDoS Protection protects publicly accessible resources in a Virtual Network
Configuring is a simple click to activate protection for new or existing VNets. Additionally, you can use Azure Application Gateway WAF to protect against application-based (Layer 7) attacks. DDoS Protection complements existing Virtual Network security features such as Network Security Groups (NSG) for a comprehensive defense in depth security solution. For details visit DDoS Protection webpage.
Application Gateway and web application firewall enhancements
Application level load balancing and web application firewalls (WAF) are required for today’s cloud-based web applications. Azure Application Gateway provides Layer 7 Application Delivery Controller (ADC) service including cookie-based session affinity, SSL Offload, URL/Host based routing, SSL re-encryption, and WAF. Application Gateway’s enhanced SSL policy support for cipher suite selection and priority ordering increases security and simplifies your compliance. The new ability to redirect (e.g. HTTP to HTTPS) ensures all web site traffic is encrypted. Support now for multi-tenant backend entities like Azure Web Apps provides more flexibility and scalability. WAF now supports open source OWASP ModSecurity Core Rule Set 3.0 which is recommended for production services. With the ability to enable or disable specific rules you choose the rules most relevant to your application. Integration of WAF with Azure Security Center further simplifies WAF manageability and monitoring.
Simplifying Networking Security management
Network Security Groups (NSGs) allow you to define network security access policies based on IP addresses restricting access to and from VMs and subnets in your VNet. However, it can be cumbersome and error-prone to manage complex security policies using only IP addresses. We have simplified the management of NSGs with Service Tags, Application Security Groups and enhanced NSG rule capabilities.
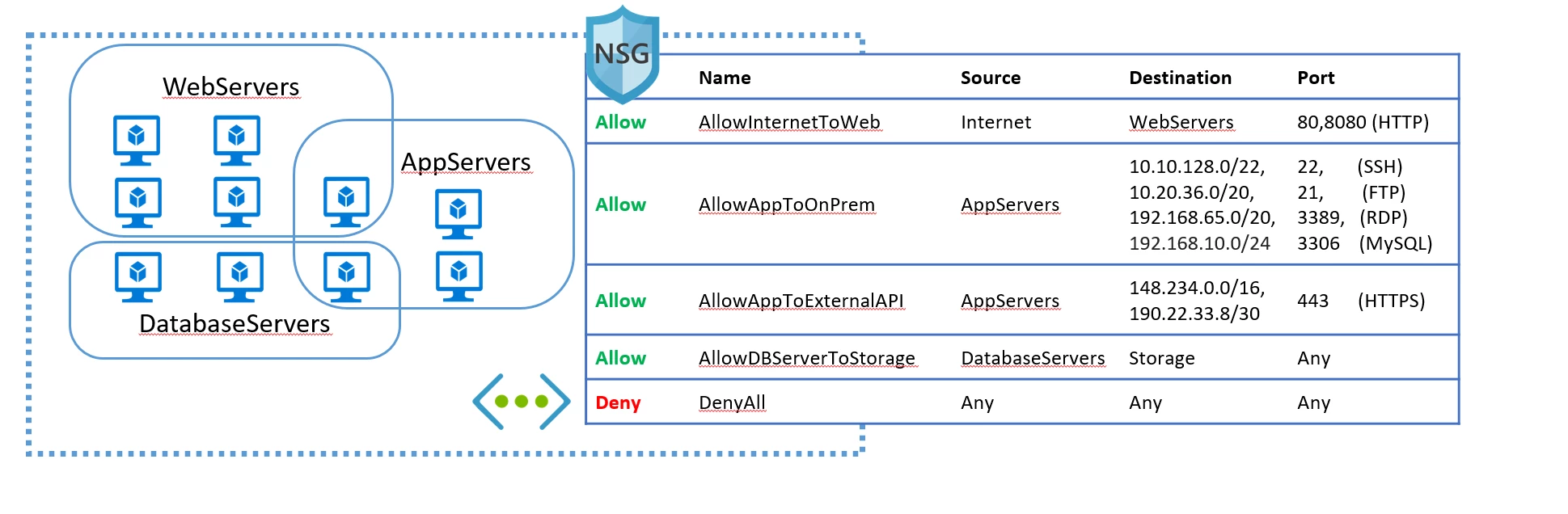
Simpler Network Security Group management with tags, groups, and enhanced rules
Service Tags: Tailoring network access to specific Azure services
Azure services use public IP addresses. A VNet that wants to access services such as Storage needs to open access to all Azure public IP addresses. Maintaining these IP addresses is problematic. A service tag is a name that represents all the IP addresses for a given Azure service, either globally or regionally. For example, the service tag named Storage represents all the Azure Storage IP addresses. You can use service tags in NSG rules to allow or deny traffic to a specific Azure service by service name. The underlying IP addresses for each tag is automatically updated by the platform. The initial release includes Service Tags for Storage, SQL, and Traffic Manager. More details are available at Service Tags.
Application Security Groups: Network security based on user defined VM groups
Application Security Groups allow you to create your own tags that represent a group of VMs. You can use this tag in your NSGs. For example, you can create a group for all your WebServers or a group for your AppServers and use these names in your security policies. More details are available at Application Security Groups.
Network Security Group Augmented Rules: Enhanced network security definition
Augmented Rules for Network Security Groups simplify security definitions. You can define larger, more complex network security policies with fewer rules. Multiple ports, multiple explicit IP addresses, Service Tags and Application Security Groups can all be combined into a single easily understood security rule. More details are available at NSG Augmented Rules.
Performance – Azure remains the fastest public cloud
Azure continues to be the fastest public cloud. Performance is critical for running mission critical workloads in the cloud. Last year we introduced 25 Gbps VMs and now we are announcing 30 Gbps VMs. Create  D64 v3, Ds64 v3, E64 v3, Es64 v3, or M128ms VMs to get 30 Gbps performance with Accelerated Networking providing ultra-low latency and high packet per second rates for VM to VM traffic.
D64 v3, Ds64 v3, E64 v3, Es64 v3, or M128ms VMs to get 30 Gbps performance with Accelerated Networking providing ultra-low latency and high packet per second rates for VM to VM traffic.
Accelerated Networking support has been greatly expanded to all 4+ physical core VMs on Dv2, Dv3, Ev2, Ev3, F and M series instances for Windows and Linux. Accelerated Networking is generally available in all public regions for Windows, and we’ve expanded the preview of Linux support to 20 regions. Azure Marketplace Ubuntu, SLES, and CentOS images now support Accelerated Networking with no manual steps. Automation for more Linux distros are coming soon.
We’ve been working with our partners to deliver performant network virtual appliances with fast packet processing using Data Plane Development Kit (DPDK) technology that provides direct access to network hardware. As announced in our Ignite session, we’ve been working with A10 to bring up their appliance in a production environment in Azure using Accelerated Networking and DPDK in D series VMs and they are seeing 30Gbps line rate with their vThunder appliance!
In A10’s own words, “A10 and Microsoft are helping customers to achieve the very best performance when migrating workloads to the public cloud,” said Raj Jalan, Chief Technology Officer, A10 Networks. “Azure cloud with DPDK significantly improves network performance. A10’s vThunder ADC on Azure will offer customers 10x more performance and reduced latency.”
DPDK support for Linux VMs using Accelerated Networking is now in a Developer Preview for partners looking to provide the best networking performance. For more details contact us at AzureDPDK@microsoft.com.
6x VPN performance
We’ve increased our VPN gateway performance so that you can have a 1 Gbps VPN connection to your Azure Virtual Network. With such performance VPN becomes a good backup option to ExpressRoute, our private network connectivity solution. The new VPN Gateway can also be used for connecting branch offices to a VNet while the core network uses ExpressRoute. Expect more performance updates from our VPN gateways early next year.
Monitoring
Customers entrust Azure to run their mission critical workloads. Providing deep operational insights into the real-time behavior of these production applications is essential. We have enhanced our network monitoring capabilities to address these needs.
Monitoring ExpressRoute with Operations Management Suite
ExpressRoute provides private network connectivity to Microsoft’s cloud services bypassing the Internet. Two new capabilities in the Operations Management Suite (OMS) provide end-to-end monitoring of ExpressRoute from on-premises to Microsoft.
- Network Performance Monitor (NPM) for ExpressRoute – Customers can monitor their connectivity end-to-end to see continuous measurements of latency, packet loss and topology snapshots in the Azure service management portal. You can set alerts and act on latency variations, packet loss and view ExpressRoute circuit, peering and connection statistics.
- Endpoint monitoring – Customers can measure latency, packet loss and view the network topology of their connectivity to PaaS or SaaS services hosted in Microsoft. For example, Endpoint monitoring can track reachability to Office 365 and Azure storage accounts.
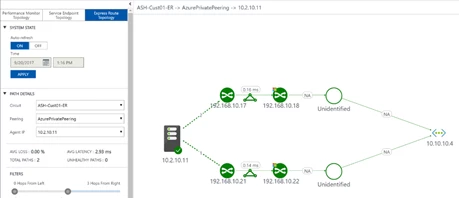
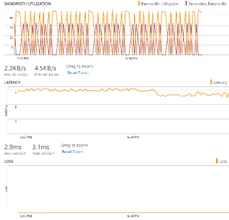
Network Performance Monitor and Endpoint monitoring enhance ExpressRoute monitoring
Enhanced Site-to-Site (S2S) VPN Monitoring
Azure VPN Gateways for Azure Monitor provides both metrics and diagnostics logs giving you the throughput of your S2S VPN tunnels and critical event logs. You can also set alerts based on VPN tunnel metrics. You get better visibility into routing information with BGP peering status for both learned and advertised routes.
Network Watcher Connectivity Check and NSG Flow Log Integration
Network Watcher enables you to diagnose, and gain insights in your Azure services using network diagnostic and visualization tools. The new Connectivity Check feature provides advanced connection diagnostics to see hop by hop information such as latency and the paths packets take to reach their destination. You can also identify configuration issues including traffic blocked by NSGs, guest firewalls, and user defined routes. Network Watcher NSG Flow Logs can be easily integrated with open source log management tools like Elastics Stack, Grafana and Graylog.
Azure Traffic Manager – Real User Measurements and Traffic View
Traffic Manager directs the end users of a global cloud service to the Azure regional endpoint with the lowest latency. Azure Traffic Manager uses the network latency measurements it collects through Microsoft’s cloud services to customize incoming queries based on location. With the new Azure Traffic Manager’s Real User Measurements, you can contribute your end users’ experience. For more information please visit the Real User Measurements Overview.
Traffic Manager Traffic View allows you to understand where your users are located, the traffic volume from these regions, the representative user latency, and specific traffic patterns. With this actionable intelligence, you can better manage your capacity and global expansion so your users get a great network experience. For more information please visit the Traffic View Overview.
Connectivity
Global Virtual Network Peering
Global VNet Peering enables linking VNets in different Azure regions allowing direct VM to VM communication via Microsoft’s global backbone network. Resources within VNets communicate with each other as if they are part of a single global network. Data replication, disaster recovery, and data base failover becomes significantly easier with a global abstraction. To learn more about Global VNet Peering please visit Global VNet Peering.
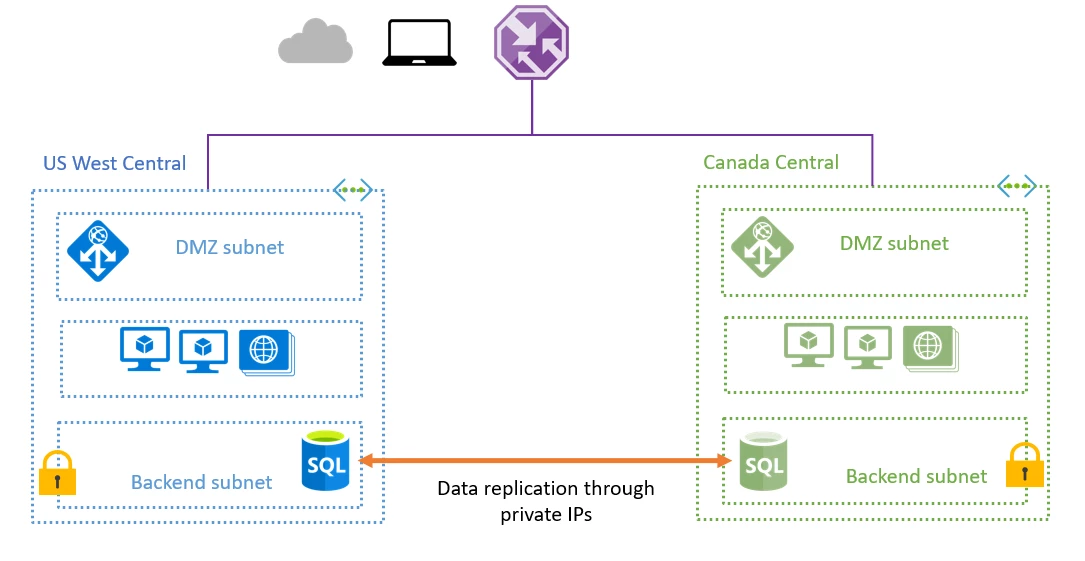
Global VNet Peering connects VNets in different regions
ExpressRoute enhancements
Accessing Azure Services through Microsoft peering, Route Filters, IPv6
Previously, ExpressRoute had three peerings: private peering for connecting to Azure VNets, public peering to reach Azure services, and Microsoft peering for Office 365 and Dynamics 365. To simplify ExpressRoute management and configuration we merged public and Microsoft peering. You can now access Azure PaaS and Microsoft SaaS services via Microsoft peering.
Route filters can dramatically reduce the number of IP prefixes advertised over ExpressRoute into your network. You can select the specific Office 365 or Dynamics 365 services you want to access via ExpressRoute. You can also select Azure services by region. Additionally, you can now use IPv6 to access Office 365 over Microsoft peering.
VPN enhancements
Point-to-Site (P2S) VPN Support for macOS and Active Directory (AD) Authentication
P2S VPN connectivity allows customers to connect to their Azure VNet from anywhere using their Windows machines and now macOS. With Active Directory domain authentication customers can now use their organization’s domain credentials for VPN authentication instead inserting certificates on the client machines. The Azure VPN Gateway integrates with your RADIUS and AD Domain deployment running either in Azure or on-premises. Integrate your RADIUS server with other identity systems for additional authentication options for P2S VPN.
Azure DNS – Private Zones
Azure Domain Name Service (DNS) Private Zones provides a DNS service to manage and resolve names within and across VNets. You can manage internal DNS names for your application without exposing this information to the Internet keeping the internal structure of your application private. Private Zones automatically maintain hostname records for the VMs in the VNets. All the common record types are supported including A, NS, TXT, CNAME, SOA, SPF and Wildcard.
With the Private Zones, Azure DNS supports split-horizon views. You can use the same name in a Private Zone and an Internet facing zone. The DNS query resolves to an internal IP address if executed within a VNet and to an external IP address if queried from outside. This is useful for websites with the same internal and external name resolving to different IP addresses.
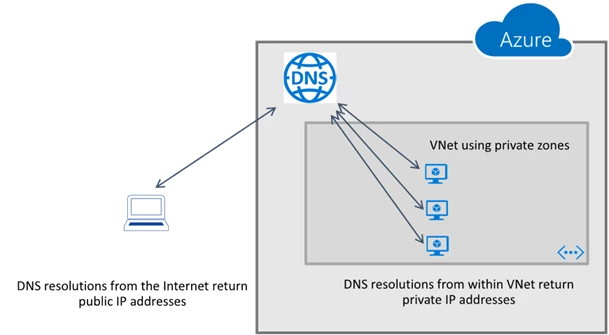
Azure DNS Private Zones can return different IPs if the DNS query is called from within the VNet or outside the VNet
Availability
New Load Balancer: 10x Scale, advanced analytics, Availability Zones, HA Ports
Load balancing enhances service availability for your applications. With the new Azure Load Balancer you can now increase your load balanced VMs by 10x from 100 to 1000 VMs. Load Balancer takes advantage of regional anycast IPs to quickly load balance external or internal traffic to ensure availability in the presence of failures. You can load balance across all your VMs deployed in Availability Zones enabling scenarios with zonal frontends and cross-zone load balancing for the backend. You also get extensive health and diagnostic metrics including continuous in-band measurements for data plane health, per endpoint health probe status, and counters for packets, bytes, connection attempts, and outbound connections.
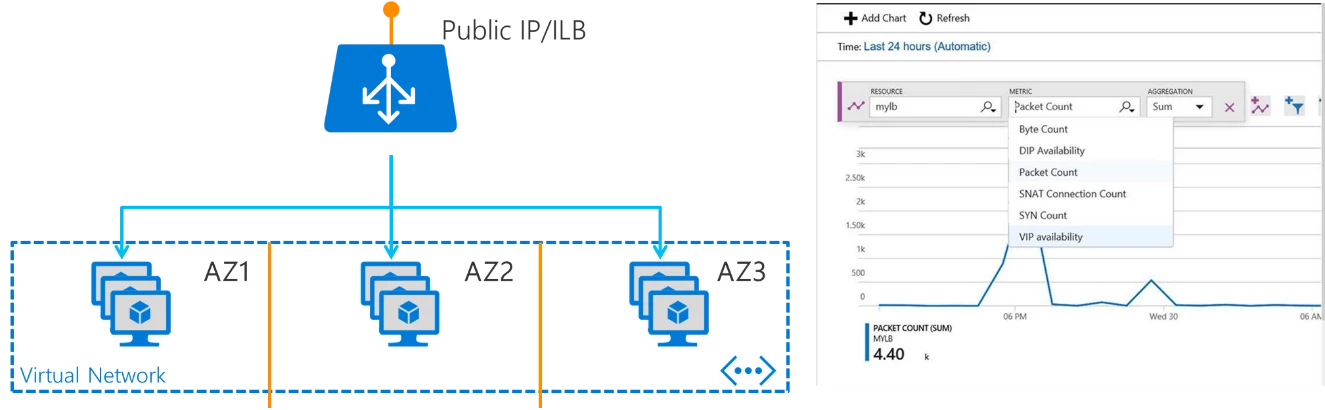
Azure’s new Load Balancer supports Availability Zones and provides better diagnostics.
High Availability for Network Virtual Appliances: HA Ports
Network Virtual Appliances (NVAs) help customers secure their critical workloads. With the new Load Balancer, you can take advantage of Highly Available (HA) Ports to easily configure a single load balancing rule to process and distribute VNet traffic coming across any Layer 4 port to your NVAs increasing reliability with faster failover and more scale-out options. Internal network traffic is load balanced across multiple NVAs such as virtual routers, firewalls, and application delivery controllers.
Learn more at Load Balancer Standard Preview and HA Ports.
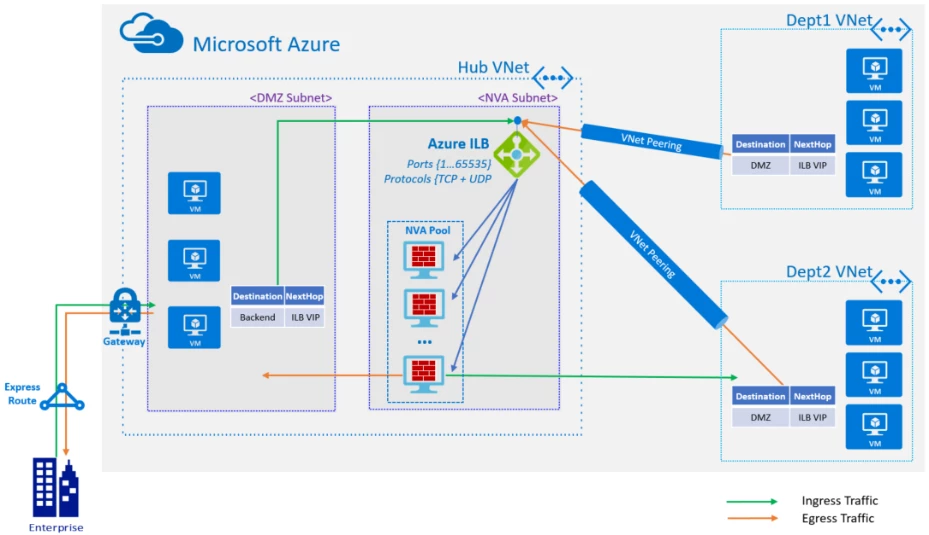
HA Ports simplifies the deployment of highly available NVAs
Ecosystem: Providing better solutions and more choices
Building a rich ecosystem of partners provides more comprehensive solutions and a variety of choices on how best to meet your specific requirements. Using our global network with over 1.6 Pbps capacity per region and the great network performance available in Azure, we see a trend of Software as Service companies and Network Virtual Appliance (NVA) companies offering compelling solutions on Azure.
Zscaler Private Access: Built on Azure for fast local breakouts to access your Azure applications
Enterprises struggle with providing secure per-user access to line of business applications. Zscaler helps to simplify the enterprise journey to Azure for both public and hybrid environments. Zscaler Private Access (ZPA), built on Azure, provides a better, fast, seamless, policy-based SaaS-like access experience for users securely accessing business applications without exposing the entire corporate network. Zscaler integrates with Active Directory for authentication and simplified policy management.
F5 WAF as a Service: Built on Azure
Maintaining a Web Application Firewall infrastructure can be a burden to your team. F5’s new WAF as a Service, built on Azure, combines enterprise grade WAF with API driven services, making it easier to protect your apps. From the Azure Marketplace you can deploy the WAF as a Service. Read F5’s announcement.
Network Virtual Appliances: More partners and more choices
The number of NVAs available in the Azure Marketplace continues to increase. Recent additions include Arista vRouter, Citrix Netscaler SD-WAN, Riverbed SteelConnect , Cisco Viptela vEdge, and Verisign DNS Firewall. See here from more information on our NVA ecosystem.
ExpressRoute Partners Tripled
We have tripled the ExpressRoute partner ecosystem providing you even more options to meet us at 40 ExpressRoute meet-me locations throughout the world. With this strong partner ecosystem, you can privately connect to us from anywhere in the world.

Summary
As you continue to bring your mission-critical workloads to Azure, we will continue to simplify the overall network management, security, scalability, availability and performance of your applications. You can fully reap the benefits offered by our global cloud and our global backbone network. One key lesson we have learned is that network-based Software-as-a-Service offerings greatly simplify your experience. Be prepared for more exciting announcements from us in the coming months. We welcome your feedback on our new features and capabilities as well as your guidance to further refine our roadmap to meet your requirements.
