What is database security?
Database security is the processes, tools, and controls that secure and protect databases against accidental and intentional threats. The objective of database security is to secure sensitive data and maintain the confidentiality, availability, and integrity of the database. In addition to protecting the data within the database, database security protects the database management system and associated applications, systems, physical and virtual servers, and network infrastructure.
To answer the question "what is database security," it's important to acknowledge that there are several types of security risks. Database security must guard against human error, excessive employee database privileges, hacker and insider attacks, malware, backup storage media exposure, physical damage to database servers, and vulnerable databases such as unpatched databases or those with too much data in buffers.
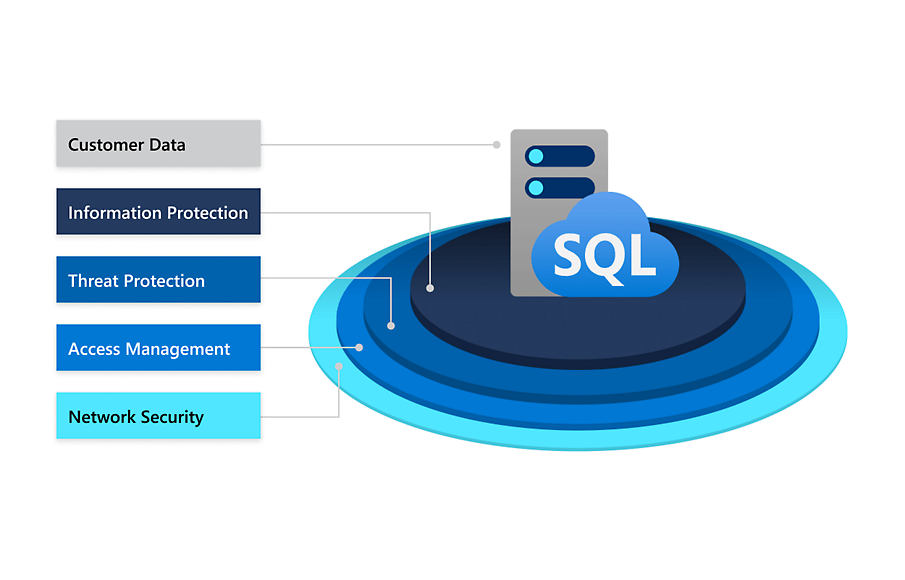
Types of database security
To achieve the highest degree of database security, organizations need multiple layers of data protection. To that end, a defense in depth (DiD) security strategy places multiple controls across the IT system. If one layer of protection fails, then another is in place to immediately prevent the attack, as illustrated below.
Network security
- Firewalls serve as the first line of defense in DiD database security. Logically, a firewall is a separator or restrictor of network traffic, which can be configured to enforce your organization's data security policy. If you use a firewall, you will increase security at the operating system level by providing a chokepoint where your security measures can be focused.
Access management
- Authentication is the process of proving the user is who he or she claims to be by entering the correct user ID and password. Some security solutions allow administrators to centrally manage the identities and permissions of database users in one central location. This includes the minimization of password storage and enables centralized password rotation policies.
- Authorization allows each user to access certain data objects and perform certain database operations like read but not modify data, modify but not delete data, or delete data.
- Access control is managed by the system administrator who assigns permissions to a user within a database. Permissions are ideally managed by adding user accounts to database roles and assigning database-level permissions to those roles. For example, row-level security (RLS) allows database administrators to restrict read and write access to rows of data based on a user's identity, role memberships, or query execution context. RLS centralizes the access logic within the database itself, which simplifies the application code and reduces the risk of accidental data disclosure.
Threat protection
- Auditing tracks database activities and helps maintain compliance with security standards by recording database events to an audit log. This allows you to monitor ongoing database activities, as well as analyze and investigate historical activity to identify potential threats or suspected abuse and security violations.
- Threat detection uncovers anomalous database activities that indicate a potential security threat to the database and can surface information about suspicious events directly to the administrator.
Information protection
- Data encryption secures sensitive data by converting it into an alternative format so only the intended parties can decipher it back to its original form and access it. Although encryption doesn't solve access control problems, it enhances security by limiting data loss when access controls are bypassed. For example, if the database host computer is misconfigured and a malicious user obtains sensitive data, such as credit card numbers, that stolen information might be useless if it’s encrypted.
- Database backup data and recovery is critical to protecting information. This process involves making backup copies of the database and log files on a regular basis and storing the copies in a secure location. The backup copy and file are available to restore the database in the event of a security breach or failure.
- Physical security strictly limits access to the physical server and hardware components. Many organizations with on-premises databases use locked rooms with restricted access for the database server hardware and networking devices. It's also important to limit access to backup media by storing it at a secure offsite location.
Database security platforms
Depending on the database platform, the amount of database security responsibility you carry can vary. If you have an on-premises solution, you need to provide everything from end-point protection to physical security of your hardware—which is no easy task. If you choose a platform as a service (PaaS) cloud database provider, your area of concern shrinks considerably.
The cloud offers significant advantages for solving long standing information security challenges. In an on-premises environment, organizations likely have unmet responsibilities and limited resources available to invest in security, which creates an environment where attackers are able to exploit vulnerabilities at all layers.
The following diagram shows a traditional approach where many security responsibilities are unmet due to limited resources. In the cloud-enabled approach, you are able to shift daily security responsibilities to your cloud provider and can get more security coverage, which frees your organization to reallocate some security resources and budget to other business priorities.

Why is database security important?
Organizations of every size in the public and private sectors struggle with database security challenges. Preventing data breaches is business-critical because they can lead to:
Data theft
Databases are prime targets for cyberattacks because they often store valuable, confidential, and sensitive information, including customer records, credit card numbers, bank account numbers, and personal identification numbers. Hackers use this information to steal identities and make unauthorized purchases.
Damage to business and brand reputation
Customers hesitate to do business with companies that don't protect their personal data. Database security issues that compromise customer information can damage the organization's reputation, resulting in a decline in sales and customer churn. To protect their reputation and rebuild customer trust, some businesses increase their investments in public relations, and offer credit monitoring systems to their data breach victims at no charge.
Revenue loss
A data breach can halt or slow down business operations and revenue generation until the database security challenges are resolved, the system is completely up and running again, and business continuity is restored.
Increased costs
Although the numbers vary by industry, data breaches can cost millions of dollars to fix, including legal fees, assisting victims, and extra expenses to recover data and restore systems. Companies might also pay ransomware to hackers who demand payment to restore their locked files and data. To protect against these costs, many businesses add cyber insurance to their policies.
Data breach violation penalties
State and local agencies impose fines, and in some cases require that customers are compensated, when companies don’t protect their customer data.

Database security best practices
We've discussed that how to secure a database includes encrypting data, authenticating only authorized users against the database or application, limiting user access to the appropriate subset of the data, and continuous monitoring and auditing of activities. Database security best practices further expand these functions to provide even more protection against threats.
Database hardening
Securing or "hardening" a database server combines physical, network, and operating system security to address vulnerabilities and make it more difficult for hackers to access the system. Database hardening best practices vary according to the type of database platform. Common steps include strengthening password protection and access controls, securing network traffic, and encrypting sensitive fields in the database.
Comprehensive data encryption
By strengthening data encryption, these capabilities make easier for organizations to secure their data and comply with regulations:
- Always encrypted data offers built-in protection of data against theft in transit, in memory, on disk, and even during query processing.
- Transparent data encryption protects against the threat of malicious offline activity by encrypting stored data (data at rest). Transparent data encryption performs real-time encryption and decryption of the database, associated backups, and transaction log files at rest without requiring changes to the application.
When combined with support for the strongest version of Transport Layer Security (TLS) network protocol, always encrypted data and transparent data encryption provide a comprehensive encryption solution for finance, banking, and healthcare organizations that need to comply with Payment Card Industry Data Security Standard (PCI DSS), which mandates strong, end-to-end protection of payment data.
Advanced threat protection
Advanced threat protection analyzes logs to detect unusual behavior and potentially harmful attempts to access or exploit databases. Alerts are created for suspicious activities such as SQL injection, potential data infiltration, and brute force attacks, or for anomalies in access patterns to catch privilege escalations and breached credentials use.
Separate authentication accounts
As a best practice, users and applications should use separate accounts to authenticate. This limits the permissions granted to users and applications and reduces the risks of malicious activity. It's especially critical if application code is vulnerable to a SQL injection attack.
Principle of least privilege
The information security principle of least privilege asserts that users and applications should be granted access only to the data and operations they require to perform their jobs. This best practice helps reduce the application's attack surface and the impact of a security breach (the blast radius) should one occur.
Zero Trust security model
Database security best practices should be part of a comprehensive approach to security that works together across platforms and clouds to safeguard your entire organization. A Zero Trust security model validates identities and device compliance for every access request to protect people, devices, apps, and data wherever they're located. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to "never trust, always verify."

Database security solutions and tools
Recent high-profile data breaches have underscored the growing sophistication of today’s threat actors and the complexity of managing business risk in an increasingly connected world. Confidently help your organization combat threats and keep your data safe with these end-to-end security and database security products.
Database security solutions
Enable Zero Trust with Microsoft security solutions. Take an end-to-end approach to security to safeguard your people, data, and infrastructure.
Strengthen your security posture with Azure. Use multilayered, built-in security controls and unique threat intelligence from Azure to help identify and protect against threats. More than 3,500 global cybersecurity experts work together to help safeguard your data in Azure.
Database security tools
Take advantage of built-in Azure Database security tools and services including Always Encrypted technology; intelligent threat protection; security controls, database access and authorization controls such as row-level security and dynamic data masking, auditing, threat detection, and data monitoring with Microsoft Defender for Cloud.
Protect your NoSQL databases with Azure Cosmos DB, which includes comprehensive advanced database security tools to help you prevent, detect, and respond to database breaches.
Database security software and services
Protect access to resources and data with Microsoft Entra ID. This enterprise identity service provides single sign-on, multifactor authentication, and conditional access to guard against 99.9 percent of cybersecurity attacks.
Securely store and access secrets using Azure Key Vault. A secret is anything that you want to tightly control access to, such as API keys, passwords, certificates, or cryptographic keys. Secure key management is essential to protecting data in the cloud.
Frequently asked questions
-
Database security is the processes, tools, and controls that secure and protect databases against accidental and intentional threats. The objective of database security is to secure sensitive data and maintain the confidentiality, availability, and integrity of the database. In addition to protecting the data within the database, database security protects the database management system and associated applications, systems, physical and virtual servers, and network infrastructure.
-
To achieve the highest degree of database security, organizations need multiple layers of data protection. This includes firewalls for network security, access controls, auditing and threat detection capabilities, data encryption, database backup and recovery, and physical security of the server, hardware components and backup media.
-
Database security guards against data breaches. Preventing data breaches is business-critical because they can cost millions of dollars to fix, including legal fees, victim compensation, data and system restoration, and fines for non-compliance with regulations. Companies might also pay ransomware to hackers who demand payment to restore their locked files and data.
-
Database security best practices address vulnerabilities and make it more difficult for hackers to access the system. They include database hardening, always encrypted data, separate authentication, advanced threat protection, and the principle of least privilege, which asserts that users and applications should be granted access only to the data and operations they require to perform their jobs.
-
Strengthen your security posture with Microsoft Zero Trust end-to-end security and Azure database security. Use multilayered, built-in security controls and unique threat intelligence to help identify and protect against threats. The defense-in-depth design of Azure services provides multi-layered security across physical data centers, infrastructure, and operations in Azure.
Start building with Azure
Try Azure cloud computing services free for up to 30 days, or get started with pay-as-you-go pricing. There's no upfront commitment—cancel anytime.
