Azure Networking Fall 2018 update
Posted on
14 min read
Announcing: 100 Gbps, fastest connectivity in public cloud and availability of branch connectivity, new cloud native security capabilities and application performance services
As enterprises move ever more demanding mission-critical workloads to the cloud, we strive to provide comprehensive networking services that are easy to deploy, manage, scale, and monitor. Customers continue to ask for better ways to connect to the cloud, better protection of their cloud workloads, optimal application performance delivery, and more comprehensive monitoring services.
In terms of how to Connect, customers have asked for significantly higher bandwidth solutions as they struggle to transit massive amounts of data into the cloud to take advantage of advanced analytics and machine learning. Software Defined Wide Area Networking (SDWAN) holds tremendous promise to reduce costs by intelligently routing more traffic onto the Internet and helping customers better manage connectivity to their branch offices. The concept of the virtual datacenter has taken hold but building such solutions on a global scale remain a challenge. With 54+ Azure regions and more on the way our global network continues to expand to new locations while we increase its overall capacity. Customers have asked us for new ways to take advantage of our global WAN. We are announcing ExpressRoute 100Gbps Direct, ExpressRoute Global Reach, and the general availability of Azure Virtual WAN along with enhancements to Virtual Networks and DNS.
Security is always top of mind as enterprises must Protect their mission-critical workloads. Protecting applications from malicious intent is critical and having full access control for all resources is critical. The cloud can help you embrace a zero-trust security posture as well as a DevOps model for managing security. Scaling, managing and understanding security polices becomes much easier with cloud native solutions. We are announcing general availability of Azure Firewall GA along with enhancements to DDoS protection and Web Application Firewall.
Application performance, availability, and resiliency are also critical to Deliver both global and regional workloads. The cloud was fundamentally designed to address application scalability to dynamically handle different types of traffic patterns. Azure combined with our global network naturally allows us not only to accelerate Microsoft services such as Bing, Office 365, and Xbox, we can also help accelerate your applications. We are announcing Azure Front Door Preview, general availability of Azure CDN along with enhancements to Application Gateway and Traffic Manager.
The DevOps model requires your team to Monitor the health and performance of your applications. The cloud can provide even better insights into your services allowing you to measure, troubleshoot, alert, and act. In running Azure 24x7x365 we have tremendous operational experience and fully understand the pressures placed on your own operations teams and the monitoring requirements to deliver world-class experiences. We are announcing preview of Virtual Network TAP along with enhancements to Network Watcher.
Here is a summary of our new networking services and enhancements to existing services to help you connect to the cloud, protect your workloads, deliver optimal performance, and monitor your service.
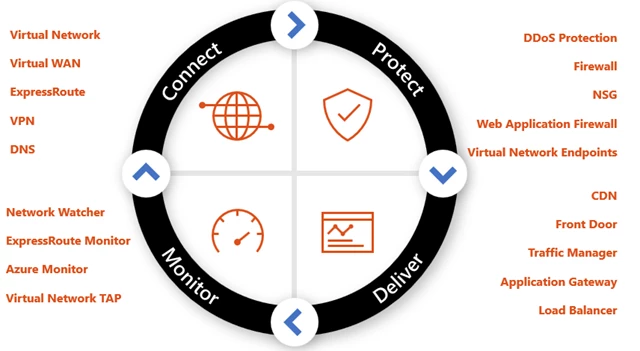
Azure helps you Connect, Protect, Deliver and Monitor your services
Connect
10X faster – ExpressRoute Direct 100Gbps connectivity
Azure is breaking the speed barrier in cloud connectivity. ExpressRoute Direct provides 100G connectivity for customers with extreme bandwidth needs. This is 10x faster than other clouds. Enterprise customers come to us with massive data ingestion scenarios such as telemedicine, content distribution, and IoT. With ExpressRoute Direct you can send 100 Gbps of network traffic to Azure services such as Azure Storage and Azure Virtual Networks. All your traffic can be on a single 100G ExpressRoute Circuit or you subdivide 100G among your business units in any combination of 40G, 10G, 5G, 2G, and 1G ExpressRoute circuits. By default, these circuits are ExpressRoute standard circuits providing connectivity to any Azure region in the same geographic region (e.g. North America, Europe, Australia, Japan, etc.). You can also designate any of the circuits as ExpressRoute Premium circuits providing global connectivity. This flexibility allows you to address the requirements of specific business units. For example, one business unit may require high bandwidth to access services within the local Azure region using a 40G ExpressRoute Standard circuit. Another business unit may require 2G global connectivity so would use a 2G ExpressRoute Premium circuit. You decide. Because ExpressRoute is for mission-critical workloads ExpressRoute Direct, like ExpressRoute, provides physical connectivity via two physical routers in an active-active configuration. Learn more about ExpressRoute Direct.
ExpressRoute Global Reach – Privately connecting your sites
ExpressRoute Global Reach allows you to connect two ExpressRoute circuits together. Your sites that are already connected to ExpressRoute can now privately exchange data via their ExpressRoute circuits. For example, a multinational company with datacenters in London and Tokyo each with an ExpressRoute circuit can enable ExpressRoute Global Reach so these sites can privately send traffic to each other using their local ExpressRoute circuits and Microsoft’s global network. ExpressRoute Global Reach can be enabled on both ExpressRoute Standard and ExpressRoute Premium circuits. ExpressRoute Global Reach is available in the following locations: Hong Kong, Ireland, Japan, Netherlands, United Kingdom, and United States with Korea and Singapore coming soon. More locations will be available later this year. Learn more about ExpressRoute Global Reach.
Virtual WAN generally available
20 Gbps S2S connectivity, new capabilities and a growing partner ecosystem
It’s quite challenging to manage 50 or 100 branch office devices connecting into a VPN service. This summer we introduced Azure Virtual WAN that simplifies large scale branch connectivity for branch to Azure and branch to branch scenarios over the Internet. We designed Virtual WAN for enterprises including large retail, medical, manufacturing, oil and gas customers looking to take advantage of SDWAN to connect their branch offices to Azure and to each other. By using SDWAN and VPN devices provided by our Virtual WAN ecosystem you get automated provisioning, configuration, scalability and high throughput. Virtual WAN supports up to 20 Gbps branch connectivity. This is a 20x improvement to our VPN gateways. Branch connectivity now becomes manageable. Virtual WAN is now generally available.
Microsoft recommends that Office 365 customers use local Internet breakouts to get onto Microsoft’s global network as quickly as possible and take advantage of the Office 365 distributed edge node ecosystem. The primary goal of the customer network design is to optimize latency to the nearest Office 365 front door and minimizing hair pining of Office 365 requests across the customer’s private network. Instead of backhauling to a central location or routing connections through another cloud service offering traffic Internet scanning, key Office 365 traffic should be allowed to egress using the Internet as locally to the user locations (branches) as possible and directly into the Microsoft network. This approach is called local and direct Internet break out and is often done by customers for selected applications, specified by policy. Customers can implement local and direct Internet breakout for Office 365 services by automating their branch routing policies by using a web service or by using an SD-WAN solution from a qualified partner. Azure Virtual WAN customers can configure their Office 365 Internet breakout policies in the Azure portal and have that policy pushed to supported SD-WAN devices in the branch offices. This ensures local and direct Internet escape of key Office 365 flows providing an optimal end user experience.
Our Virtual WAN ecosystem continues to grow. In addition to Citrix and Riverbed, Virtual WAN solutions are now available from 128 Technology, Barracuda, Check Point, NetFoundry, and Palo Alto. Coming soon Virtual WAN solutions will be available from CloudGenix, Nuage Networks, Silver Peak, Versa Networks, and VeloCloud.


Azure Virtual WAN ecosystem
New Virtual WAN preview capabilities include P2S VPN and ExpressRoute. With P2S VPN you can use an OpenVPN client to connect to your Virtual WAN. This enables mobile workers to securely access resources via the Virtual WAN from laptops and mobile devices while they travel or work from home. Azure P2S VPN is available in Azure Virtual WAN and can support up to 10,000 concurrent remote users per Virtual WAN hub with a throughput of 18 Gpbs.
With ExpressRoute as part of your Virtual WAN your branches can securely use the Internet to access the Virtual WAN and then have that traffic privately go to your datacenter connected to ExpressRoute.
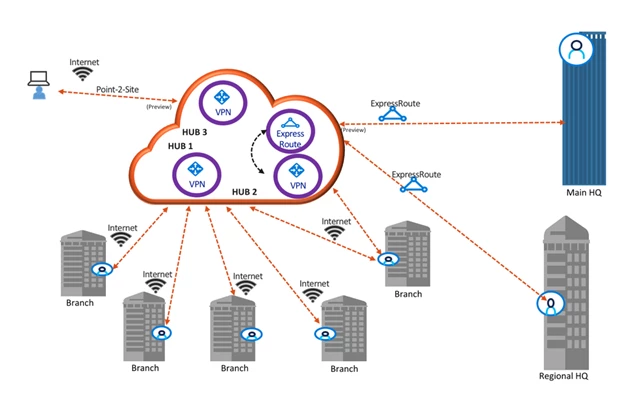
Azure Virtual WAN simplifies all your connectivity
Learn more about Virtual WAN.
Zone-Redundant VPN and ExpressRoute Virtual Network Gateways
Many customers use VPNs and ExpressRoute to access their Virtual Networks. To improve the resiliency, scalability and availability of gateways, we now have new Zone Redundant VPN and ExpressRoute Gateways that bring support for Azure Availability Zones. With these new Zone-Redundant/Zonal Gateways, you will be able to deploy Azure VPN and Azure ExpressRoute gateways in Azure Availability Zones, thus making them physically and logically separate within a region to protect your on-premises network connectivity to Azure from zone-level failures. We have also reduced the deployment time for these gateways. For more information on Zone Redundant gateways please refer to our documentation.
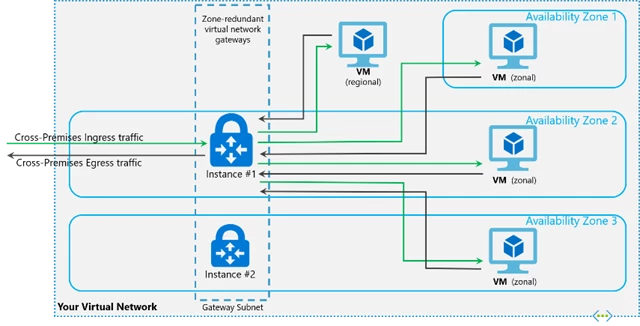
Zone redundant gateways provide better resiliency
Public IP Prefix
A Public IP Prefix is a contiguous range of IP addresses for your Azure public endpoints that enables you to associate your Azure resources with public IP addresses from a known fixed range. This significantly reduces management overhead by eliminating the need to change firewall rules as you assign IP addresses to new resources. Get started with the preview and learn more about Public IP Prefix.
Load Balancer – Outbound Rules and TCP Reset on Idle
Outbound rules make it simple to configure public Load Balancer’s pool-based outbound network address translation (NAT). You can use declarative configuration to scale and tune your outbound configuration to your specific needs.
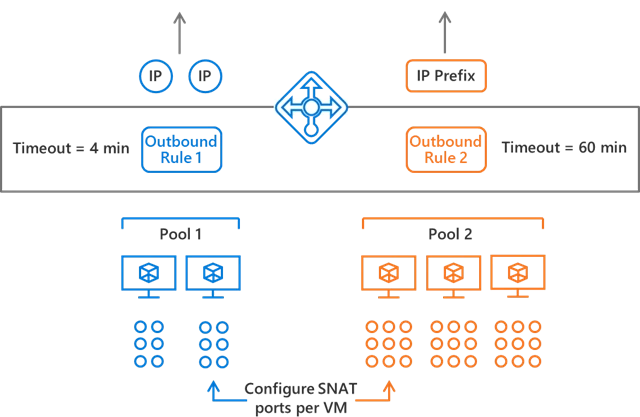
Simple load balancer configuration
Outbound rules describe which pool of virtual machines should be translated to which public IP addresses, how many outbound SNAT ports to allocate, and change outbound idle timeout. You can simplify whitelisting by using outbound rules with public IP prefix. Review Outbound Rules for details.
You can optimize application performance by enabling TCP Resets on Idle on any rule for clean connection releases without changing the application. When enabled, TCP Reset packets are sent to both client and server endpoints at idle timeout. Review Load Balancer with TCP Reset on idle timeout for details.
Virtual Network for Containers
The Azure Container Networking Interface (CNI) plugin attaches containers to a VNet. It brings the rich set of Azure Networking capabilities to containers by utilizing the same SDN stack that powers Azure VMs. Containers can now connect to peered VNets and to on-premises over ExpressRoute or site-to-site VPN and access services such as Storage and SQL protected by VNet Service Endpoint. Network Security Group (NSG) and User Defined Routing (UDR) rules can be applied directly to containers.
Azure CNI is utilized by the Azure Kubernetes Service. It is also integrated into the Azure Container Instance Service and Azure WebApps for App Services which utilize an improved SDN stack for fast and secure injection of containers into customer VNets. For more information please refer to documentation.
Alias (Reference) Record support for Azure DNS
Azure DNS customers sometimes face problems keeping track of the lifecycle of Azure resources from within their DNS zones. For example, when the Public IP resource associated with an application gets deleted, the customer needed to manually update their DNS zone to prevent a dangling reference that could potentially blackhole their traffic. We are announcing support for Alias records for DNS zones. This allows customers to reference other Azure resources from within their DNS zones such that the DNS records get updated automatically when there is a lifecycle event on the referenced Azure resources. We support Alias record references to two Azure resources – Public IP and Azure Traffic Manager – with more resources planned in the future. For more details on the Alias Record support within Azure DNS, please see this blog post.
Protect
Azure Firewall – General availability, new capabilities
Azure Firewall, now GA, offers fully stateful network and application level traffic filtering for VNet resources, with built-in high availability and cloud scalability delivered as a service. Customers can protect their VNets by filtering Outbound, Inbound, Spoke-Spoke, VPN and ExpressRoute traffic. Connectivity policy enforcement is supported across multiple VNets and Azure subscriptions. Centralized logging using Azure Monitor, allows you to archive logs to a storage account, stream events to your Event Hub, or send them to Log Analytics or your SIEM of choice. Azure Firewall supports FQDN Tags to allow traffic to well-known Microsoft Services (e.g. ASE, Azure Backup and Windows Update) and Destination NAT configuration.
For more information, please refer to Azure Firewall documentation.

We are working with our partner ecosystem to provide SaaS based security policy management capabilities using the Azure Firewall public REST APIs. Solutions will be available in preview later this year including central management with Barracuda and AlgoSec AlgoSaaS, and Security policy management for containers Azure Kubernetes Service (AKS) using Tufin Orca.

Growing Azure Firewall ecosystem
DDoS Protection Attack Analytics
The sophistication and frequency of DDoS attacks continue to increase, hitting nearly two in five businesses. DDoS attacks cause service outages. With the proliferation of compromised IoT devices that are weaponized as botnets to launch mega DDoS attacks, hackers are well equipped to achieve their nefarious goals. Azure DDoS Protection provides countermeasures against sophisticated DDoS threats.
We are announcing general availability of three new features for Azure DDoS Protection: Attack Mitigation Reports, Attack Mitigation Flow Logs and DDoS Rapid Response. Customers protecting their virtual networks against DDoS attacks with Azure DDoS Protection get detailed visibility into attack traffic and actions taken to mitigate the attack via diagnostic settings in Azure Monitor. DDoS Rapid Response will enable customers to engage DDoS experts during an active attack for specialized support.
Attack Mitigation Reports provide near-real time information about an attack and comprehensive reports summarizing the attack after it’s been mitigated. Attack Mitigation Flow Logs provide network level 5-tuple packet data (protocol, source/destination port, source/destination IP) and action taken during an active DDoS attack. This data can be integrated with Security information and Event Management (SIEM) systems via Event Hub for near-real time monitoring. Both Mitigation Reports and Flow logs can be integrated with Azure Analytics for data visualization.
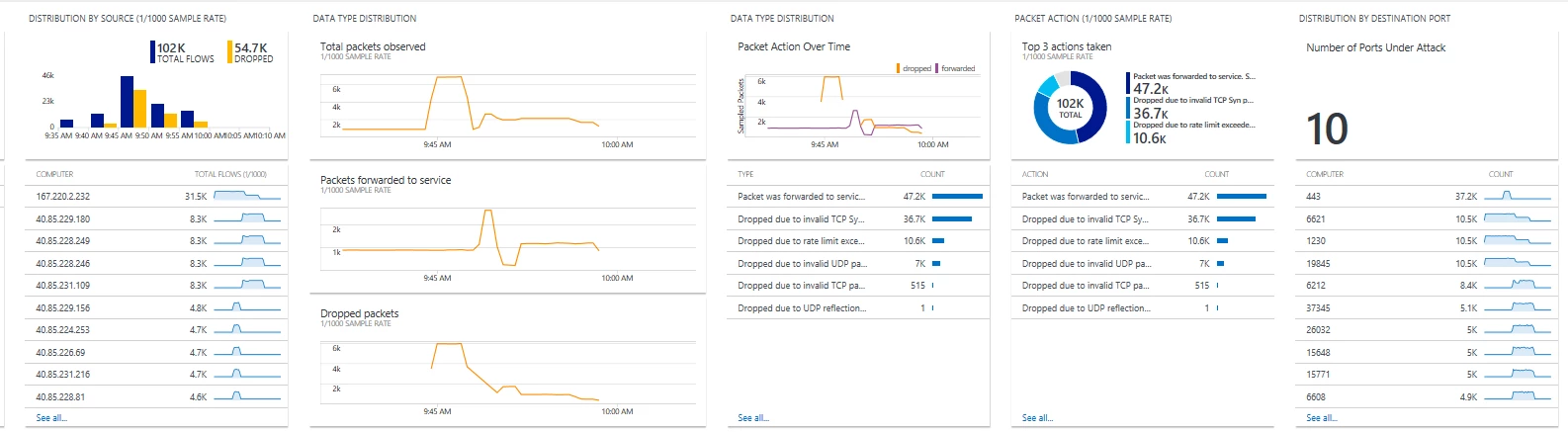
DDoS Attack Mitigation Reports
Customers now have access to the DDoS Rapid Response (DRR) team for specialized support during an active attack. The DRR team helps with attack investigations, custom mitigations during an attack and post attack analysis. For more details, please refer to this blog post and product documentation.
Azure Virtual Network Service Endpoint Policies
Azure VNet service endpoint policies enable you to prevent unauthorized access to Azure service resources from your virtual network. Endpoint policies provide more granular control over the Network Security Group (NSG) service tags. You can allow access to only specific Azure service resources (e.g. Azure Storage accounts), using service endpoint policies. The feature is available in preview for Azure Storage. For more information, please refer to service endpoint policies documentation.
Deliver
Azure Front Door Service – Global HTTP load balancing
Azure Front Door Service (AFD), is a global, scalable entry-point that utilizes our intelligent network edge so you can create fast, secure and massively scalable web applications. Built to support Microsoft’s biggest web workloads including Bing, Office 365, Xbox Live, MSN, and Azure DevOps, AFD offers web-scale reliability and scalability.
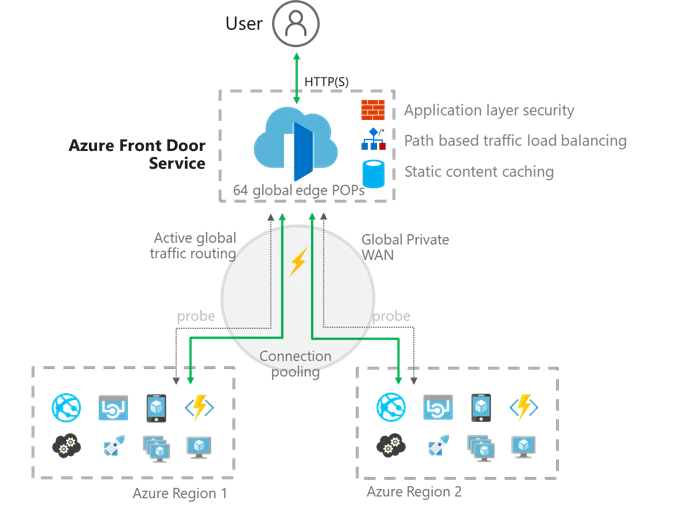
Azure Front Door Service accelerates your applications
Currently located in 33 countries at Microsoft network edge locations connected by our global WAN, AFD improves your application’s performance through application acceleration, SSL offload, allows routes your global HTTP traffic to your closest available backend, and enables enterprise-grade reliability with automated instant failover.
Using AFD’s path aware routing, inline caching, rate limiting and application layer security, you can build modern, global applications in Azure. A central control plane and dashboard enables you to manage and monitor service traffic and global microservice backends inside or outside of Azure.
AFD’s integration with Azure Web Apps, Azure Monitor and Log Analytics enables you to easily accelerate and deliver your applications with lower latency, higher reliability and deeper global traffic insights. Refer to AFD documentation to explore how to accelerate your application.
Azure CDN from Microsoft general availability
Cloud services require reliability, scale, agility and performance. Azure CDN delivers an easy to setup and use CDN platform to distribute your videos, files, web sites and other HTTP content to the world. With CDN services from Verizon, Akamai and now Microsoft, Azure CDN is built from the ground up to deliver best in class CDN services through our multi-CDN ecosystem for your Azure applications.
Azure CDN’s multi-CDN ecosystem enables you to manage CDN as an Azure resource through an on-demand API driven model. This flexibility along with three strong CDN infrastructures enables you to easily add multi-CDN as part of your content delivery strategy. Using these CDN solutions on their own, side-by-side in a multi-CDN solution or tiering them to maximize reliability, offload and performance, you can focus on optimizing your delivery to suit your business needs. See the Azure CDN documentation to learn more.
Application Gateway autoscaling, 5x better performance, zone redundancy and analytics
Application Gateway and Web Application Firewall (WAF) provides Application Delivery Controller as a service. We are announcing preview of a new elastic autoscaling option enabling deployments that automatically scales up or down based on the application’s traffic pattern. Management is greatly simplified since customers do not need to pre-provision for anticipated peak traffic volumes. Autoscaling also supports Azure Zones for zonal failure resiliency. A single Application Gateway or WAF deployment can now span multiple Availability Zones that are physically and logically separate and can route traffic to backend servers in any zone. The autoscaled Application Gateway also provides better performance, reduced provisioning time and support for Static VIPs. SSL offload performance is now 5X better. Please refer to documentation for additional details and tutorials.
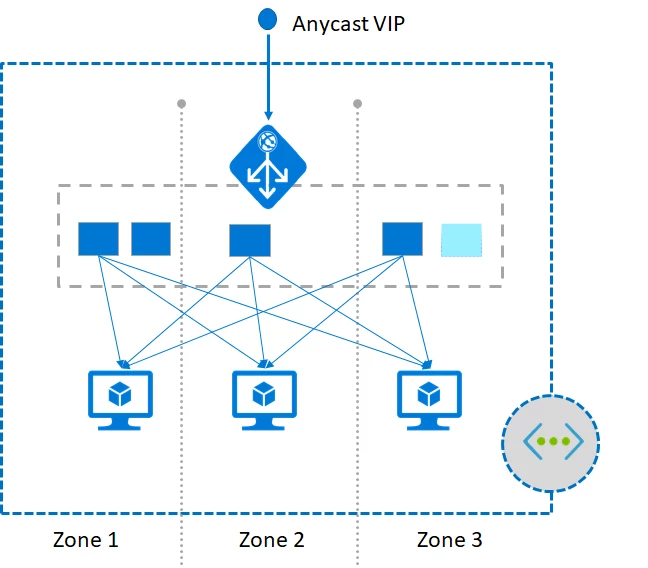
Zone Redundant Web Application Firewall
We are announcing preview of Application Gateway integration with Azure Kubernetes Service (AKS) Ingress Controller. The Application Gateway Ingress controller runs as a pod within the AKS cluster and allows Application Gateway to act as ingress for an AKS cluster. It listens to Kubernetes Ingress Resources from the Kubernetes API server and converts them to Azure Application Gateway configuration and updates the Application Gateway through Azure Resource Manager (ARM). For more details please refer to our documentation.
Web Application Firewall (WAF) is previewing enhanced configurability so customers can control request body and file upload size. Customers can enable/disable request body payload inspection. Web Application Firewall provides the ability to exclude request’s headers, cookies or query string from rule evaluation via exclusion lists. This allows customers to reduce false positives by whitelisting known safe parameters such as bearer tokens from WAF rules. For additional details and tutorials please refer to documentation.
More routing and endpoint monitoring options in Azure Traffic Manager
Customers can now add their endpoints to a Traffic Manager profile using IPv4 or IPv6 addresses and get A / AAAA type responses for DNS queries made against that profile. This option, currently limited to external type endpoints, enables endpoints without DNS names associated with them to be part of any Traffic Manager routing method and get the benefits of high availability and low latency connections for end users. Associated with that is a new routing method, Multi-Value routing, allowing you to specify how many healthy endpoints to be returned as part of a single DNS query response. This capability increases the reliability of your application by giving the callers multiple options to retry before querying again for a healthy endpoint.
Traffic Manager now supports multi-tenant endpoints by letting you specify headers (including host headers) in the health checks that are initiated by Traffic Manager. This allows accurate health checking of those multi-tenant endpoints and routing traffic appropriately towards them. To learn more about these new capabilities in Traffic manager please visit the endpoint monitoring documentation.
Monitor
Virtual Network TAP – Visibility for monitoring, security, and performance
We are announcing preview of the first native distributed network TAP available in any public cloud. Azure Virtual Network TAP provides continuous mirroring of virtual machine network traffic to a packet collector without using agents.
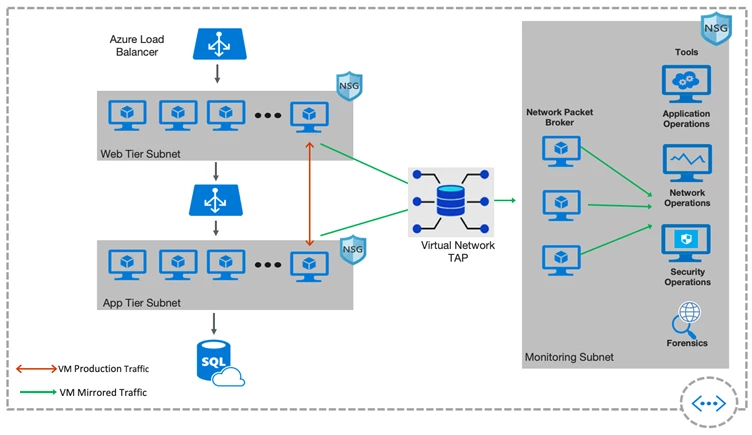
Azure Virtual Network TAP enables out of band monitoring
Out of band monitoring, security, and performance solutions can now be deployed in your Virtual Network. Solutions are available from Big Switch Networks, ExtraHop, Fidelis, Flowmon, Gigamon, Ixia, Netscout, Nubeva, RSA and Vectra.

Azure Virtual Network TAP ecosystem
For more information, please refer to Azure Virtual Network TAP documentation.
Summary
We are fully committed to helping you connect to Azure, protect your workloads, deliver a great networking experience and provide extensive monitoring to simplify your deployment and operational costs while helping you better support your customers. At Ignite 2018 we will add more details about our announcements. Here is a list of our technical sessions. We’ll continue providing innovative networking services and guidance to help you take full advantage of the cloud. We’re excited to learn about your new scenarios enabled by our networking services. As always, we welcome your feedback.