This post was contributed by Susie Adams, Chief Technology Officer, Microsoft Federal and Diego Lapiduz, Chief Information Security Architect, Azure Government at Microsoft.
Many government customers that are working to optimize security in the cloud have asked for guidance on how to align with the policies set by the Trusted Internet Connections (TIC) Initiative. A common myth is that this is possible for Infrastructure-as-a-Service (IaaS) but not for Platform-as-a-Service (PaaS) solutions.
To help agencies be as efficient as possible in their transition to the cloud, we recently published new Trusted Internet Connection guidance on how agencies can build IaaS and PaaS solutions that meet TIC requirements.
If you’re not familiar with the policy, the purpose of the Trusted Internet Connection (TIC) policy is to standardize the security of individual external network connections in use by federal agencies. The policy is outlined in the OMB (Office of Management and Budget) memorandum M-08-05. This policy originated in 2007, predating the demands of an increasingly mobile-first, cloud-first environment.
DHS has since published the TIC Reference Architecture v2.2 (2017) which introduced new capabilities in order to comply with this policy. As new updates to the policy are published, we will update our guidance accordingly.
Summary of Azure Networking Options
There are three main options when connecting to Azure services. In the documentation, you’ll learn several ways to meet the Trusted Internet Connection Appendix H (Cloud Considerations) requirements using these options:
- Direct internet connection
- Encrypted tunnel using the Virtual Private Network service
- Private connection to Azure using Microsoft ExpressRoute
IaaS solution
Complying with TIC policy using IaaS is relatively simple since Azure customers manage their own virtual network routing. Learn more in the documentation on configuration and auditing of Azure IaaS TIC compliance.
PaaS solutions
Because Azure PaaS services, such as Azure App Service, continue to evolve and add new networking and security features, achieving TIC compliance for PaaS solutions is easier than ever. In fact, the architecture that we propose for PaaS is essentially the same as the IaaS recommendation due to new private networking options.
Learn more about how Azure Platform-as-a-Service offerings can help with TIC compliance.
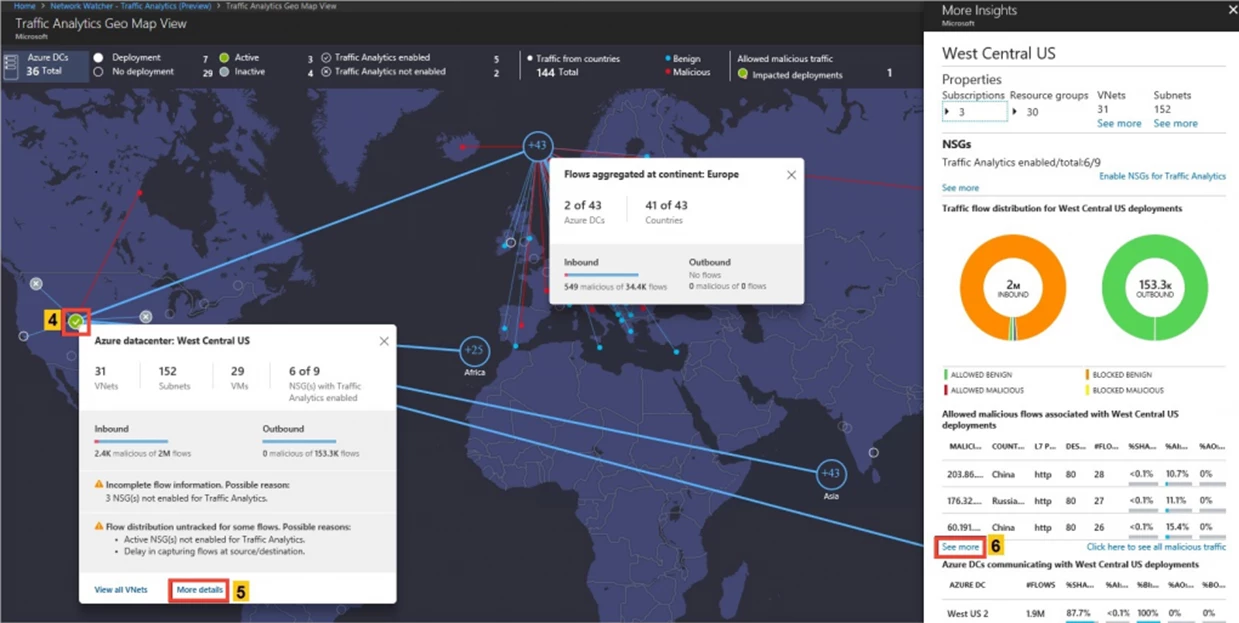
Situational Awareness with Azure Traffic Analytics
Coming soon to Azure Government is Traffic Analytics which consumes flow log data and other logs to provide high-level overview of network traffic. This data can be useful for auditing TIC compliance and identifying trouble spots. A high-level dashboard can be used to rapidly screen which VMs are communicating with the internet, providing a focused list for TIC routing.
Stay tuned for update
As TIC policy evolves, we’ll update the Trusted Internet Connection guidance accordingly. To stay up to date on all things Azure Government, be sure to subscribe to our RSS feed and to receive emails, click “Subscribe by Email” on the Azure Government Blog.