Companies of all sizes are embracing containers as a fast and portable way to lift, shift and modernize into cloud-native apps. As part of this process, customers need a way to store and manage images for all types of container deployments. In November, we announced the preview of Azure Container Registry, which enables developers to create and maintain Azure container registries to store and manage private Docker container images.
On March 27th Azure Container Registry became generally available, supporting a network-close, private registry for Linux and Windows container images. Azure Container Registry integrates well with orchestrators hosted in Azure Container Service, including Docker Swarm, Kubernetes and DC/OS as well as other Azure Services including Service Fabric and Azure App Services. Customers can benefit from using familiar tooling capable of working with the open source Docker Registry v2. Learn more by watching this Azure Container Registry GA video.
Building on the November Preview, we’ve added the following features and capabilities:
- Availability in 23 regions, with a global footprint (with more coming)
- Repositories, tag, and manifest listing in the Azure Portal
- Dual-key password providing key rotation
- Nested level repositories
- Azure CLI 2.0 support
Global Availability
Container registry is now available globally. As part of our general availability release, all features are now available in all regions.
A full list of the supported regions are:
|
|
|
Multi-Arch Support
With the release of Windows Containers, we’re increasingly seeing customers who want both Windows and Linux images. While the Azure Container Registry supports both Windows and Linux, docker has added the ability to pull a single named image and have it resolve the os version based on the host the image is pulled from. Using multi-arch support, a customer can push both Windows and Linux based tags and their development teams can create their dockerfiles using FROM contoso.comaspnetcorecorpstandard. The Azure Container Registry multi-arch features will pull the appropriate image based on the host it’s called from.
Nested Repositories
Development teams often work in hierarchies and deploy solutions based on collections. The bikesharing team may have a collection of images they wish to group together (bikesharingweb, bikesharingapi), while the headtrax team has their collection (headtraxweb, headtraxapi, headtraxadmin), with a set of corporate images available to all members (aspnet:corpstandard).
The Azure Container Registry supports nested repos to enable teams to group their repos and images to match their development.
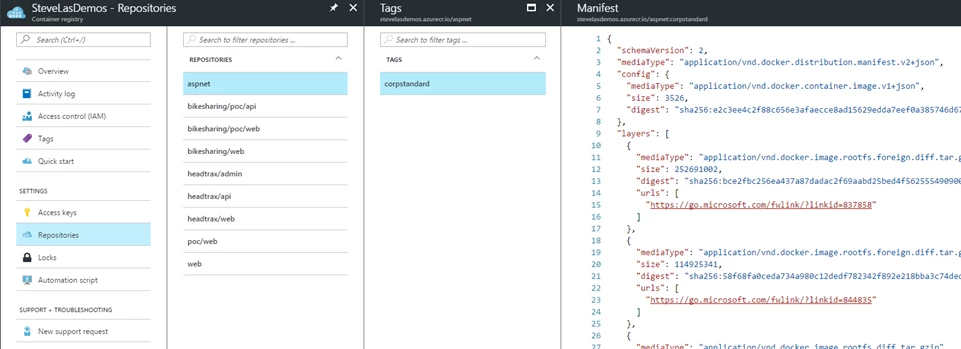
Repositories, tags, manifests
Customers have requested visibility into the contents of their registry. With the GA release, you will now have an integrated experience in the Azure portal to view the repositories, images, tags and the contents of manifests associated with an image.
To view repositories and tags you’ve already created in your repository:
- Log in to the Azure Portal.
- Select “More Services” on the left-side panel.
- Search for “Container registries“.
- Select the registry you want to inspect.
- On the left-hand side panel, select “Repositories“.
The repositories blade will display a list of all the repositories (including nested registries) that you have created, as well as the images that are stored in these repositories.
If you select a specific image, it will open up a “Tags” blade containing the tags associated with that image. Additionally, if you select a tag, you will have the ability to see the manifest for that image tag.
Improved passwords
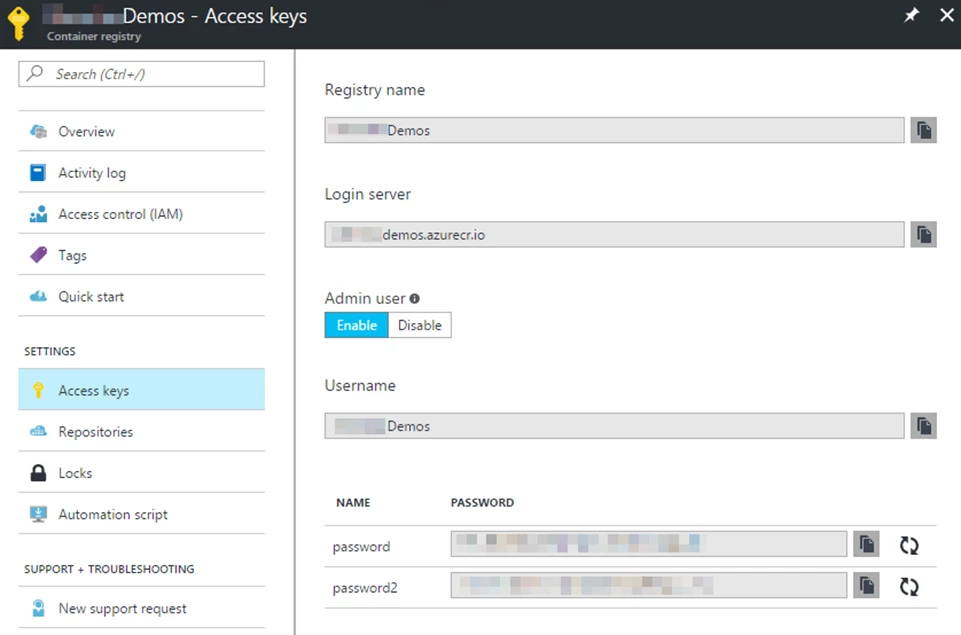
We have also made improvements for registry admin accounts. While we recommend using a service principal as a best practice, we wanted to improve on the safety of this alternative providing the ability to do key rotation. As such, new container registries will have access to two admin passwords, both of which can be regenerated. Having two passwords allows you to maintain connections by allowing you to swap to another password if you need to regenerate one.
To regenerate passwords, go to the “Access Keys” section of a registry on which you have enabled an Admin user.
Summary
We hope you enjoy the new features and capabilities of container registries. If you have any comments, requests, or issues, you can reach out to us on StackOverflow or log issues at https://github.com/azure/acr/issues