Container based applications are growing at a strong pace, as result, we are seeing an increasing number of customers using Azure Container Registry to manage their Linux and Windows container images. Azure Container Registry provides a network-close, private registry and integrates well with orchestrators hosted in Azure as well as other Azure Services including Service Fabric, Azure App Service, IoT, Machine Learning, and more to come.
Today, we are excited to announce:
- The general availability of the Azure Container Registry geo-replication
- ACR Build (preview) – providing inner-loop and trigger-based container build capabilities
- Secure by default container registries (private preview)
Previewed in October of 2017, geo-replication enables small startups, working in disparate locations, to enterprises operating at global scale. With geo-replication, customers can harness the global footprint of Azure. With the click of a map, customers can geo-replicate their container images and metadata across 23 regions, with Korea, South India, Azure China and other regions coming online soon.
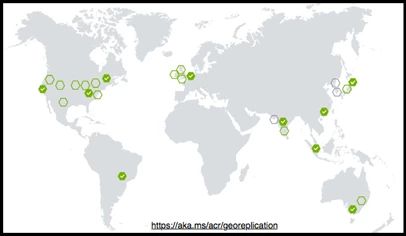 Leveraging Azure Traffic Manager, registry requests are routed to the closest replicated region, assuring customers are served from the closest, fastest data center. All role-based access control configurations and metadata are automatically replicated assuring compute redundancy, in addition to the secured at rest data redundancy provided with single region registries. Geo-replication is a feature of the premium registry tier, enabling customers to opt into the level of support they need.
Leveraging Azure Traffic Manager, registry requests are routed to the closest replicated region, assuring customers are served from the closest, fastest data center. All role-based access control configurations and metadata are automatically replicated assuring compute redundancy, in addition to the secured at rest data redundancy provided with single region registries. Geo-replication is a feature of the premium registry tier, enabling customers to opt into the level of support they need.
ACR Build – Lifecycle Management, OS & Framework Patching
As containers provide new levels of virtualization, enabling application and developer dependencies to be isolated from the infrastructure and operational requirements, we must address how the application virtualization is patched. Azure Container Registry launches ACR Build, a container build capability, enabling inner-loop development extended to the cloud and automated container builds from git commits and base image updates. With base image update triggers, customers can automate their OS & Framework patching needs, maintaining secure environments, while adhering to the principals of immutable containers. ACR Build will dynamically discover base image dependencies, hooking base image update notifications from other ACR registries, with Docker Hub and other public registries coming in the future.
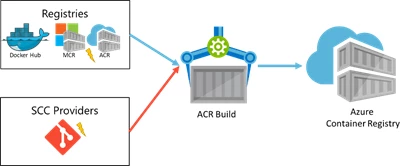
The preview of ACR Build currently supports Linux, with Windows coming soon. As IoT edge devices grow, ARM based builds will become common and required to automate securing devices on the edge. ACR Build will add ARM support, securing IoT edge devices.
“The fact that we could use the same syntax with the docker and az CLIs made it trivial for us to adopt and getting started on using the service has almost no set up, just create a registry and you’re on your way. ACR Build is exactly what we needed for a successful and timely launch of Azure support in Stacksmith.” Martin Albisetti, Software Architect at Bitnami Stacksmith
Secure by default Container Registries
As customers move from development to production, we’ve seen challenges with the notion of fast, and secure deployments. The current container scanning workflow protects nodes from insecure images, however there’s no prescribed or enforced pattern for assuring source registries have already had their images scanned. Without this, deployments must either be stalled or fail while a scan completes. In some cases, customers deploy the un-scanned image, hoping a trojan horse isn’t lurking inside.
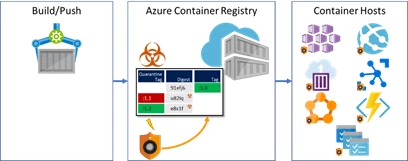
Working with great partners like Aqua Security and Twistlock, Azure Container Registry introduces a new pattern to secure image pulls until security scanning has determined the image is safe to deploy. Integrating webhooks enables an asynchronous, yet deterministic pattern for developers and CI solutions to push their images, put the image in quarantine while the scanner completes its task. ACR will emit a quarantine webhook, enabling immediate scanning, and when completed successfully, a push webhook is triggered, enabling CD solutions to kick-in, triggering deployments based on already scanned images.
“Twistlock is proud to have worked with Microsoft on the secure by default pattern. Pushing security ‘left’ in the CI/CD process helps reduce risk and the ACR quarantine pattern with Twistlock scanning is a simple and powerful layer of defense in depth for enforcing what images you allow to run.” John Morello CTO at Twistlock
“Securing the build-ship-run process is an essential part of any container-based application deployment. By providing policy-driven quarantining of images on the Azure Container Registry, Microsoft is providing customers with an easy way to prevent unauthorized images from introducing vulnerabilities, malware, and other risks. We are thrilled to be selected by the Azure team to support these capabilities with our container security platform, and enable a smoother and more secure experience for Azure customers.” Amir Jerbi, CTO and co-founder of Aqua Security.
At Azure, we see containers as the modern packaging format for custom and ISV software, across all Azure services. As the enterprise cloud, Azure focuses on lifecycle management enabling customers large and small to focus on their business needs, while enabling flexibility and capabilities required to automate secure and productive environments.
