Announcements, Networking, Security, Web Application Firewall
Intelligent application protection from edge to cloud with Azure Web Application Firewall
Posted on
6 min read
Threat intelligence at scale!
Changes to how we work and operate our businesses have driven every company to now be a digital company. This acceleration in digital transformation has also led to a rise in security risks. Cyberattacks are becoming more common and advanced with growing attack surfaces due to the proliferation of mobile and IoT devices and increasing cloud adoption. Basic protection measures are no longer sufficient as new attack vectors have emerged and attacks have become more sophisticated with automated and large-scale attacks. To help our customers address these security challenges, we have been evolving Azure Web Application Firewall (Azure WAF), our cloud-native, self-managed security service to protect your applications and APIs running in Azure or anywhere else—from the network edge to the cloud.
A quick primer on Azure WAF
We offer two options—global and regional—for deploying Azure WAF for your applications and APIs.
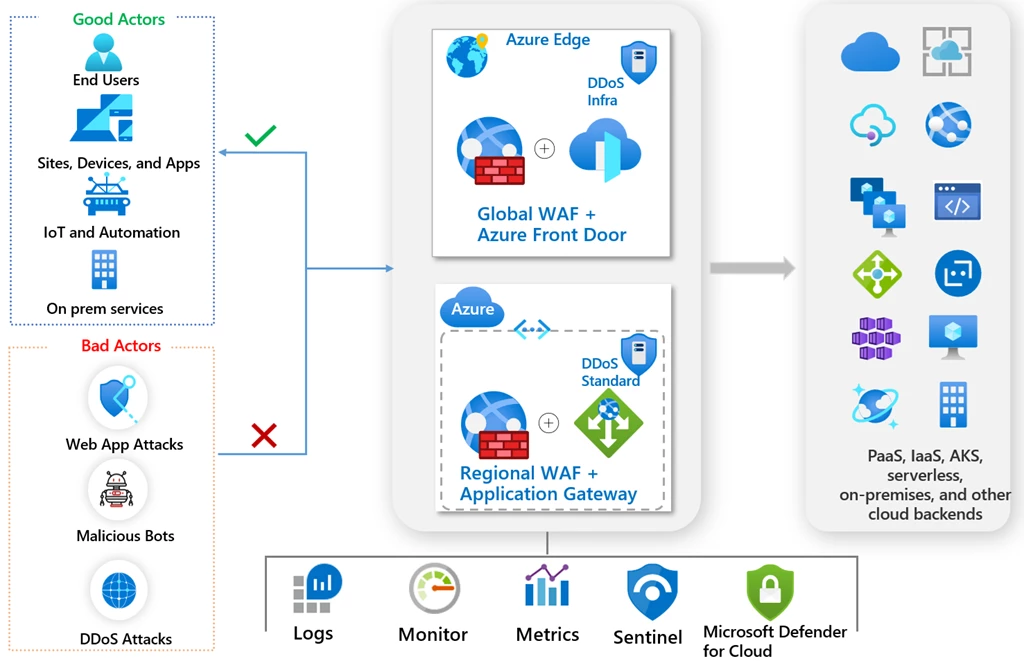
- Global WAF: Azure WAF attaches to Azure Front Door, our native, modern cloud content delivery network (CDN), to provide global application acceleration and intelligent security at scale. Azure WAF stops the security attacks at the network edge closer to the source of attack with over hundreds of edge locations around the world.
- Regional WAF: Azure WAF attaches to Azure Application Gateway, a highly scalable, web application regional load balancer running in a virtual network. It manages traffic for both internal and external websites and provides application protection in over 60 Azure regions worldwide.
What’s changed?
We are excited to share recent updates and announce many new features that will offer customers better security, improved scale, easier deployment, and better management of their applications.
Application and API protection
- Improved security posture with new rulesets: On March 29, we announced the general availability of Managed Default Rule Set 2.0 (DRS 2.0) integrated with Azure Front Door Premium tier. DRS 2.0 includes the latest Microsoft proprietary rules authored by Microsoft Threat Intelligence. Today, on regional WAF attached to Azure Application Gateway, we are excited to announce the general availability of Open Web Application Security Project (OWASP) Core Rule Set 3.2 (CRS 3.2). These updated rulesets provide increased coverage for web vulnerabilities, reduce false positives, and protect against specific vulnerabilities, like Log4J and SpringShell CVEs.
- Anomaly scoring with reduced false positives: Like regional WAF, we also introduced anomaly scoring with DRS 2.0 on global WAF which drastically helps reduce false positives for customer applications. In anomaly scoring mode, when an incoming request violates WAF rule, it is assigned an anomaly score based on the severity of the rule, and an action is taken only when the anomaly score reaches a threshold.
- Increased size limits: With CRS 3.2, regional WAF can now support request body size inspection up to 2MB and file upload size up to 4GB.
- API security: With DRS 2.0, global WAF now also supports XML and JSON content types that allow request inspection to secure inbound traffic. Azure WAF on Azure Front Door and Azure Application Gateway seamlessly integrates with Azure API Management to provide advanced API management and security features.
- Advanced customization with per rule exclusions: As in global WAF, today we are also introducing per rule exclusions with CRS 3.2 on regional WAF with Application Gateway. Exclusions allow you to override WAF engine behavior by specifying certain request attributes to omit from rule evaluation. In addition, we now allow attribute exclusions definitions by name or value of header, cookies, and arguments. Exclusions can be applied to a rule, set of rules, rule group, or globally for the entire ruleset, providing increased flexibility to help reduce false positives and meet application-specific requirements. This feature is currently available via Azure portal, Azure Resource Manager, PowerShell, CLI, and SDK.
Bot protection
Bots have become an essential part of our customer’s digital footprint, helping to automate and perform key functions. However, attackers are increasingly taking advantage of this by manipulating bots to carry out malicious tasks. We’re continuously improving our platform capabilities to better protect against bot attacks—bot protection with Bot Manager 1.0 ruleset is available through integration with the Azure Front Door Premium tier. Our bot detection and protection rules are based on Microsoft Threat Intelligence and support bot classification for good, bad, and unknown bots. Bad bots include bots from malicious IP addresses or bots that have falsified identities. The malicious IPs are provided by Microsoft’s Threat Intelligence feed, which is based on feeds from external providers and internal threat intel. For good bots, WAF uses reverse DNS lookups to validate if the user-agent and IP address range match what the agent claims it to be. Bot signatures are dynamically managed and automatically updated by WAF when new threat actors are detected.
Performance and scale with the next generation of WAF engine
We are excited to announce the general availability of our next-generation WAF engine on Azure Application Gateway. The new WAF engine, released with CRS 3.2, is a high-performance, scalable Microsoft proprietary engine and has significant improvements over the previous WAF engine.
Benefits of the new Azure WAF engine include:
- Improved performance: In our test lab, the new engine resulted in significant reduction in WAF latencies when compared with the previous version of engine. We also observed significant reduction in P99 tail latencies with up to ~8 times in processing POST requests and ~4 times reduction processing GET requests.
- Increased scale: Our next-gen engine can scale up to 8 times more RPS using the same compute power and has the ability to process 16 times larger request sizes (now up to 2MB request size), which was not possible earlier with the previous engine.
- Better protection: New redesigned engine with efficient regex processing offers better protection against RegEx DoS attacks.
- Richer feature set: The new engine is available with the CRS 3.2 version. New features and future enhancements will only be available through the new engine and the later versions of CRS. Customers are strongly encouraged to move to CRS 3.2 version. We are in the process of phasing out CRS 2.2.9 and will stop onboarding new customers on the older CRS 2.2.9 version. Existing customers on CRS 2.2.9 will continue to be supported.
To learn more about the new engine, see WAF engine documentation.
Management and monitoring
- Native consistent experience with WAF policy: Application Gateways WAF v2 now natively utilizes regional WAF policy instead of config by default, removing the need for the legacy WAF config experience on Azure Application Gateway. All the latest features and future enhancements will be available via WAF policies. Application Gateway configuration continues to be supported for existing deployments of v1 and v2 SKUs, but customers are strongly encouraged to migrate to Application Gateway v2 with WAF policies that offer a richer feature set and improved experiences at no additional cost. Azure policies can be shared across multiple application gateway deployments, simplifying the management experience. With Azure policy, customers can easily automate deployment and provisioning of applications using DevOps and APIs friendly tools—Azure Resource Manager, REST API, PowerShell, CLI, and Terraform.
- Advanced analytics capabilities: You can now access new Azure Monitor metrics on regional WAF for more effective monitoring, troubleshooting, and debugging. Azure Monitor logs and metrics for WAF can be streamed to a central log platform for advanced log analytics and are further consumed by Microsoft Sentinel and Microsoft Defender for Cloud for security monitoring and alerting. Microsoft Sentinel integration allows security analysts to analyze and correlate data from other sources, detect threats, and automate incidence response. For example, we recently released Sentinel hunting queries to detect and respond to zero-day critical vulnerabilities like—Log4J Sentinel hunting queries and SpringShell Sentinel hunting queries.
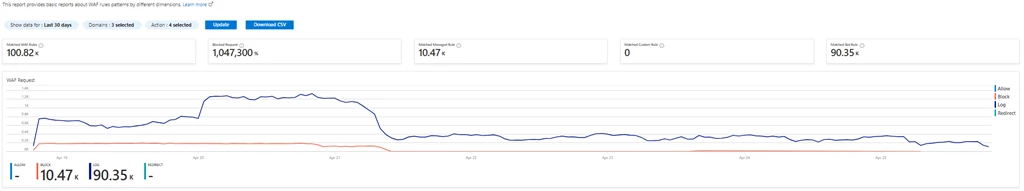
- Built-in security reports: Security reports on Azure Front Door provide powerful visualization of WAF patterns, trends by action, and events by rule types and rule groups. Security threat analysts can view breakdown top events by different dimensions like IP, country, URL, hostname, and user-agent for threat analysis.
- Improved manageability: Azure WAF integration with Azure Firewall Manager is coming soon. With this integration, customers will be able to manage WAF policies at scale for applications hosted on Azure Front Door and Azure Application Gateway platforms.
Get started and share your feedback
You can try Azure WAF with Azure Application Gateway and Azure Front Door today. Visit Azure WAF documentation to learn more. As we continue to enhance the Azure WAF offering, we would love to hear your feedback. Post your ideas and suggestions on the networking community page or email us at azurewaf@microsoft.com.
Stay safe!